Trustwave researchers outline free card skimmer detection techniques

Online shoppers and merchants can detect whether websites are infected by Magecart with easy to use techniques provided from researchers at Trustwave.
In a blog post published yesterday (December 19), security researcher Michael Yuen outlined how to determine whether websites had been compromised by the notorious card skimmer and its varied obfuscation methods.
“Over the last few years, we’ve observed multiple ways that were used to inject skimming scripts into ecommerce sites,” Ziv Mador, vice president of security research at Trustwave SpiderLabs, told The Daily Swig.
“This blog is not a perfect solution but, in most cases, the steps described will help reveal Magecart scripts if they are present.”
Magecart attacks mainly work by injecting malicious JavaScript code into websites in order to sniff out user payment card data and credentials, which have been entered via online forms.
While a Content Security Policy (CSP) and Subresource Integrity (SRI) checks are the most common ways to protect against the card skimming malware, many small companies are unable to put forward the resources and necessary training to deploy these defense mechanisms.
Trustwave suggests using urlscanl.io, an online tool that analyzes websites, in order to determine whether Magecart scripts have compromised websites.
Entering an online store’s address in urlscan will return all the domains from which the website retrieves its web assets.
The first step is to look for suspicious items in the list of domains that the website communicates with. Details of domains can be found in the “IP Detail” tab of urlscan’s “Domain & IP information” section.
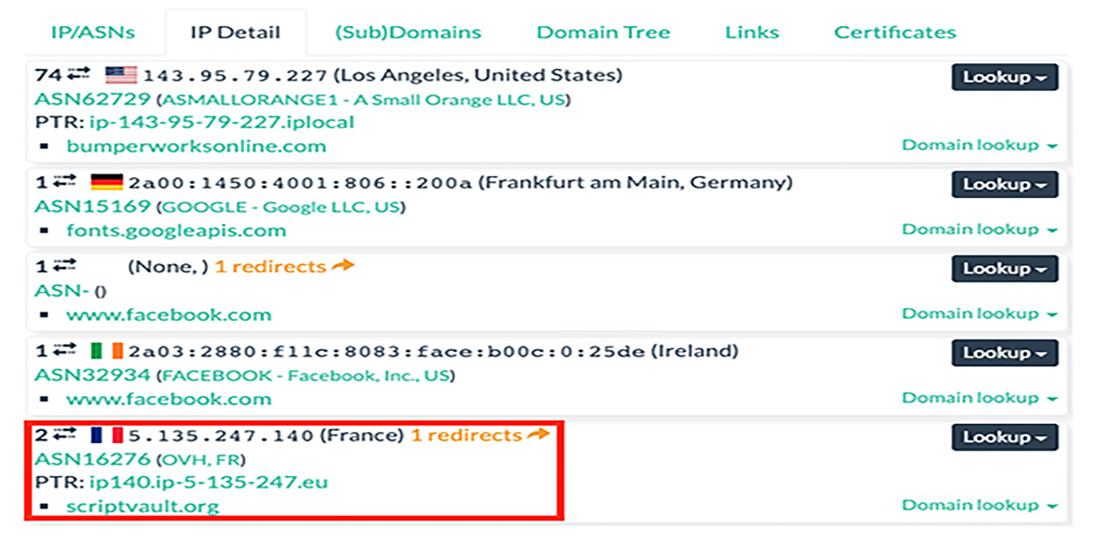
Since Magecart attacks are conducted through JavaScript files, the next step is to check the scripts the website downloads from the suspicious domain. The HTTP tab provides the list of web assets, which can be filtered to only show scripts.

In the example above, the website in question (bumperworksonline.com) is downloading the script bumperworksonline.js from the scriptvault.org domain. This is a red flag because namesake scripts are usually hosted on the website’s own servers.
Clicking on “Show response” returns the content of the file and reveals an obfuscated Magecart script.
How can online store owners harden their websites against Magecart attacks?
Mador provides the following tips:
- Make sure web server software is fully patched
- Remove extensions that are not mandatory
- Make the critical checkout page as static as possible
- Evaluate loading third-party scripts whenever possible. Consider using a local copy
- Adopt a hardened Content Security Policy (CSP) and Subresource Integrity (SRI) throughout the site
Not all skimmers are created equal
Not all Magecart scripts are hosted on third-party servers. In many cases, the malicious actors manage to compromise and infect scripts stored on the main server of the targeted website.
To check in-page scripts, users can try some of the open-source tools mentioned at the end of the post or submit the URL to VirusTotal, a free online tool that scans files and web addresses against known vulnerabilities.
Malicious actors also use novel methods, such as compromising abandoned GitHub projects and inserting Magecart snippets into their JavaScript files. This pushes the malicious code to all the websites and applications that depend on them.
“[Finding and taking down skimming files] is ultimately a game of whack-a-mole because new domains get created all the time,” Yuen said.
“The only reliable way of preventing Magecart is to detect, fix, and harden the security of websites.”
YOU MIGHT ALSO LIKE SwigCast, Episode 4: MAGECART






