The tool has already unearthed critical flaws in Microsoft’s Azure DevOps Server

A team of researchers has developed a new open source tool that can help automate the discovery of dangerous deserialization vulnerabilities in .Net applications.
Named SerialDetector, the tool has already netted the researchers bug bounties after helping them to unearth three critical vulnerabilities potentially leading to remote code execution (RCE) in Microsoft’s Azure DevOps Server.
The researchers, from Sweden’s KTH Royal Institute of Technology, also used the tool to uncover object injection vulnerabilities (OIVs) in six other applications.
The tool has been released on GitHub and documented in a paper (PDF) presented at the Network and Distributed Systems Security (NDSS) Symposium in late February.
From deserialization to object injection vulnerabilities
Many modern programming languages and software frameworks support serialization and deserialization, features that allow inter-process exchange of objects through JSON, XML, binary, and other data formats. For instance, a client-side mobile or desktop application can use the serialization/deserialization features of its underlying framework to send structured objects to a RESTful service in XML format.
Serialization simplifies programming and adds flexibility to frameworks, enabling developers to avoid locking their programs into specific types of objects.
It does, however, come with security trade-offs. For instance, if the deserialization process is not controlled on the server, it can lead to OIVs, where malicious actors modify a serialized object’s properties before sending it to the server, which then executes arbitrary code during deserialization.
RECOMMENDED H2C smuggling named top web hacking technique of 2020
The famous Equifax hack that leaked the sensitive financial information of 143 million US customers in 2017 was caused by a deserialization vulnerability in Apache Struts that led to RCE.
“Although deserialization vulnerabilities were known for a long time, developers kept using insecure deserializers like JSON libs for many years until these vulnerabilities were exploited,” Mikhail Shcherbakov, PhD student at KTH Royal Institute of Technology and lead author of the SerialDetector paper, told The Daily Swig.
Shcherbakov describes the process of discovering and patching deserialization as “more of an art than science.”
A lack of thorough research and tool development on deserialization and OIVs means most current approaches treat object injection like other types of injection attacks such as SQL and command injection. OIVs are more complex and harder to discover because they are caused by vulnerabilities that exist not only in a target application but also in the underlying framework.
A systematic approach
Along with his supervisor Musard Balliu, an assistant professor at KTH, Shcherbakov wanted to develop a systematic approach to automating the drudge work involved in discovering OIVs. “From the very beginning, we wanted to develop a tool that would scale to large code bases such as the .NET platform,” Shcherbakov said.
Microsoft Azure DevOps, which is built on top of the .Net framework, works with many different data formats and implements complex workflows for input data, so the researchers figured that there was a possibility for insecure deserialization vulnerabilities.
Read more of the latest hacking tools news
With a bit of probing, they found that the DevOps server had several OIVs, including a JSON deserialization bug that emerged in 2017.
“At this point, we wondered why JSON and Yaml serialization libraries were considered safe for so long and if/how we could describe and detect the root causes of such vulnerabilities,” Shcherbakov said. “So we started working on SerialDetector and the development of a static analysis tool for .NET code formed its basis.”
SerialDetector under the hood
“There is no automatic analysis tool for detecting such vulnerabilities in large code bases like .NET framework. SerialDetector is the first step to help framework developers discover OIVs early on,” Shcherbakov said.
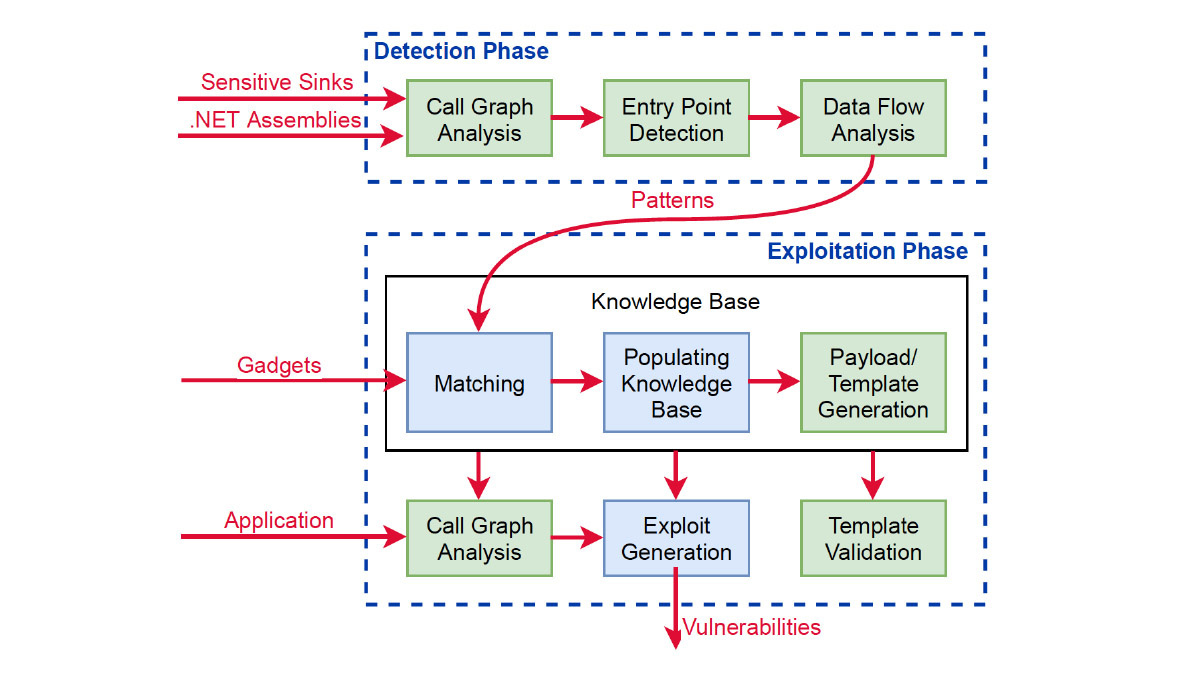
Existing methods for discovering OIVs rely on knowledge of known vulnerable application APIs, whereas SerialDetector spots new vulnerable patterns. The tool works in two phases: fully automated detection and semi-automated exploitation.
During the detection phase, SerialDetector gets a list of .Net assemblies and sensitive sinks, which can be exploited to find OIVs. The tool performs a thorough analysis of the assemblies and automatically generates patterns that could be used for OIV attacks.
In the exploitation phase, SerialDetector matches the patterns found in the detection phase with a list of vulnerable gadgets until it finds one or more that can be sent to the server and trigger malicious behavior such as RCE. The tool draws on a knowledge base of malicious payloads.
YOU MIGHT ALSO LIKE Prime-factor mathematical foundations of RSA cryptography ‘broken’, claims cryptographer
 Expanding work on deserialization vulnerabilities
Expanding work on deserialization vulnerabilities
Shcherbakov and Balliu are planning to further improve the tool’s automation features. “If we could find gadgets automatically in a large code base such as .NET Framework, then we can validate all detected OIV patterns and report only the exploitable ones,” he said. “This would allow us to detect and validate new vulnerable APIs on framework level automatically.
“We are exploring a combination of static and dynamic techniques to achieve this.”
While SerialDetector has been developed for the .Net framework, the concept can be applied to other frameworks and languages.
“The approach is framework-agnostic in the sense that it can be applied to other languages that use features like reflection to create objects of arbitrary type at runtime,” Shcherbakov explained. “Namely, it does not rely on external knowledge about vulnerable methods.”
YOU MAY ALSO LIKE Dispute rages over ModSecurity 3 WAF ‘bypass risk’






