The Top 10 list is a widely used guide to modern web application security threats

The Open Web Application Security Project (OWASP) has published its draft Top 10 2021 list revealing a shake-up of how modern threats are categorized.
In an announcement yesterday (September 8), OWASP said the draft Top 10 web application security threats for 2021 has been published for the purposes of “peer review, comment, translation, and suggestions for improvements”.
The draft report, available to view online, contains important changes to how the non-profit categorizes today’s web app threats, which have not been refreshed since 2017.
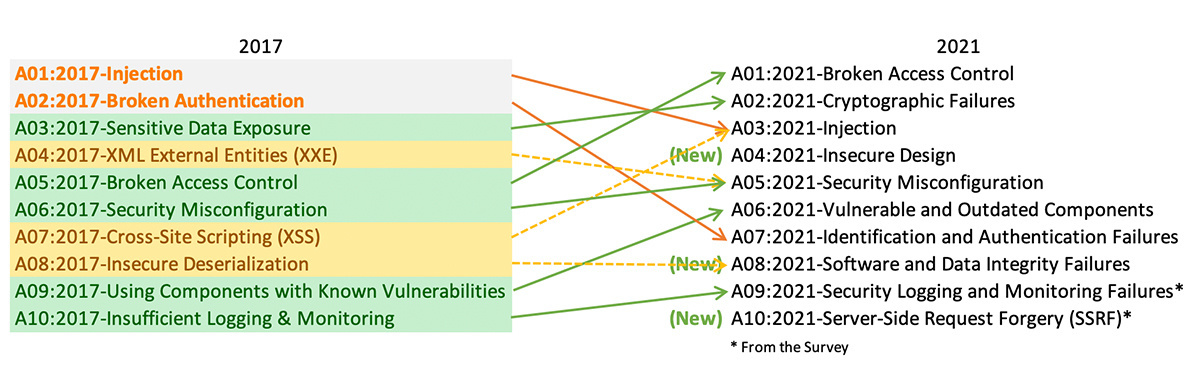 State of play: OWASP Top 10 changes in 2021 (draft edition)
State of play: OWASP Top 10 changes in 2021 (draft edition)
Digging into the draft Top 10
There are three new categories: ‘Insecure Design’, ‘Software and Data Integrity Failures’, and a group for ‘Server-Side Request Forgery (SSRF)’ attacks.
2017’s ‘XML External Entities (XXE)’ section has been added to 2021’s Security Misconfiguration category, ‘Cross-Site Scripting (XSS)’ has been added to the ‘Injection’ section, and ‘Insecure Deserialization’ is now part of ‘Software and Data Integrity Failures’.
OWASP has also renamed several categories to match scoping changes.
Read more of the latest security vulnerability news and analysis
When the organization analyzes threat intel, provided by cybersecurity firms, there are specific data factors that are used to generate the Top 10 list. These include software and hardware Common Weakness Enumeration (CWE) mapping, the percentage of apps vulnerable to a particular CWE, and their coverage in organizations.
OWASP also considers the weighted exploit and average metrics of a vulnerability, based on CVSSv2 and CVSSv3 scores, and the total number of apps found to have CWEs mapped to a category, as well as total CVE numbers attributable to a particular type of threat.
OWASP Top 10: The full list
1.A01:2021-Broken Access Control: 34 CWEs. Access control vulnerabilities include privilege escalation, malicious URL modification, access control bypass, CORS misconfiguration, and tampering with primary keys.
2.A02:2021-Cryptographic Failures: 29 CWEs. This includes security failures when data is in transit or at rest, such as the implementation of weak cryptographic algorithms, poor or lax key generation, a failure to implement encryption or to verify certificates, and the transmission of data in cleartext.
3.A03:2021-Injection: 33 CWEs. Common injections impact SQL, NoSQL, OS command, and LDAP, and may be caused by sanitization failures, XSS vulnerabilities, and a lack of protection for file paths.
4.A04:2021-Insecure Design: 40 CWEs. Insecure design elements vary widely, but are generally described by OWASP as “missing or ineffective control design”. Areas of concern include a lack of protection for stored data, logic programming problems, and displaying content that reveals sensitive information.
5.A05:2021-Security Misconfiguration: 20 CWEs. Applications may be considered vulnerable if they lack security hardening, if there are unnecessary features – such as a too-open hand when it comes to privileges – if default accounts are kept active, and if security features are not configured correctly.
6.A06:2021-Vulnerable and Outdated Components: Three CWEs. This category focuses on client and server-side components, failures to maintain components, out-of-date support systems – such as an OS, web servers, or libraries – as well as component misconfiguration.
7.A07:2021-Identification and Authentication Failures: 22 CWEs. Security issues include improper authentication, session fixation, certificate mismatches, permitting weak credentials, and a lack of protection against brute-force attacks.
8.A08:2021-Software and Data Integrity Failures: 10 CWEs. Integrity is the focal point of this category, and any failure to do so properly – such as the deserialization of untrusted data, or not checking code and updates when pulled from a remote source – may be in scope.
9.A09:2021-Security Logging and Monitoring Failures: Four CWEs. Issues that can hamper the analysis of a data breach or other form of attack, including logging problems, failing to record security-relevant information feeds, or only logging data locally come under this category.
10.A10:2021-Server-Side Request Forgery: One CWE. SSRF vulnerabilities occur when a server does not validate user-submitted URLs when they fetch remote resources. OWASP says that the adoption of cloud services and increasingly complex architectures have ramped up the severity of SSRF attacks.
Analysis: OWASP shifts left
“The additions of ‘Insecure Design’ and ‘Software and Data Integrity Failures’ show how the entire software industry is continuing to ‘shift left’ by putting more focus on secure design and architecture as well as threat modeling,” Tom Eston, practice director of application security at Bishop Fox told The Daily Swig.
“Often, secure design and threat modeling get overlooked because of the speed of modern development. It’s also great to finally see OWASP calling out software integrity and the security of CI/CD pipelines as another focus area.”
RELATED Google and Mozilla lay the groundwork for a ‘post-XSS world’
OWASP has also updated the methodology employed in generating the Top 10 list. Eight out of 10 categories are data-driven, and two have been selected based on responses from industry surveys.
“AppSec researchers take time to find new vulnerabilities and new ways to test for them,” the organization says. “It takes time to integrate these tests into tools and processes.
“By the time we can reliably test a weakness at scale, years have likely passed. To balance that view, we use an industry survey to ask people on the front lines what they see as essential weaknesses that the data may not show yet.”
It should be noted that once cybersecurity experts and peers have provided feedback, this list may be subject to change.
Positive responses
Brain Glas, co-lead for the OWASP Top 10, told us that the draft has initially received a lot of positive responses, although he expects “a small number of vocal people that disagree with the current draft.
“This is a complex industry and a complex topic, people can have a wide range of experiences and backgrounds. For some, the draft Top 10 will align with their experience and perceptions, for others it won't and I expect there [will] likely [be] some minor changes as we process feedback and polish the draft” – although this is not yet set in stone.
Andrew van der Stock, executive director of OWASP, added: “In this version, we are attempting to give guidance on how folks actually use it. In the 2007 and 2017 versions, I wrote that it’s an awareness document and no more. But that’s not how folks use it.
“If the OWASP Top 10 was a game, the majority of uses would be considered emergent gameplay unintended but welcomed by the authors. So this time around, we chose to say how best to use it as an informal standard and as the very start of an AppSec program.”
OWASP has also thanked organizations including AppSec Labs, GitLab, Cobalt.io, HackerOne, and Veracode, among others, for contributing data connected to over 500,000 applications.
The non-profit says that these contributions have amassed to “the largest and most comprehensive application security data set” so far.
Alongside the draft report, a “surprise extra” will be released on September 24. OWASP hopes the next instalment will be earlier than the four years required for this release, delayed further due to Covid-19.
YOU MIGHT ALSO LIKE Machine learning technique detects phishing sites based on markup visualization






