Open source web hacking utility scrapes site parameters using the Internet Archive API
ParamSpider, a new open source tool, automates the discovery of parameters in URL addresses, a key step in probing websites and applications for vulnerabilities.
Developed by indie security researcher Devansh Batham (aka Asm0d3us), the tool scrapes the parameters of a target website using the Internet Archive API.
Bug bounty hunters and security researchers can then feed this data to a fuzzer to find potential vulnerabilities.
“Last month, as I was working on a private [bug bounty] program, I ran a query on the Web Archive CDX API, and I noticed that there are a lot of URLs with parameters present in the data returned by the API,” Batham told The Daily Swig in written comments.
As Batham was going through the results, a ?file_url parameter caught his attention. It turned out that the parameter was vulnerable to server-side request forgery (SSRF) and he was able to access many private files on the servers.
“Going through the data thrown by CDX API was a tedious task, so I thought of automating this process and I made ParamSpider,” Batham says.
Raining XSS
The India-based security researcher initially used ParamSpider for personal use to parse and clean URL data.
“In just two days, I found 20+ XSS vulnerabilities and some open redirect issues from the parameters ParamSpider found,” he said.
READ MORE Latest hacking tools – Q1 2020
After that, Batham decided to make ParamSpider public and released it on GitHub so that bug bounty hunters can use it in their research.
According to Batham, ParamSpider is the only tool that scans web archives.
ParamMiner is another tool that helps in the discovery of URL parameters using wordlists and guessing techniques.
How does ParamSpider work?
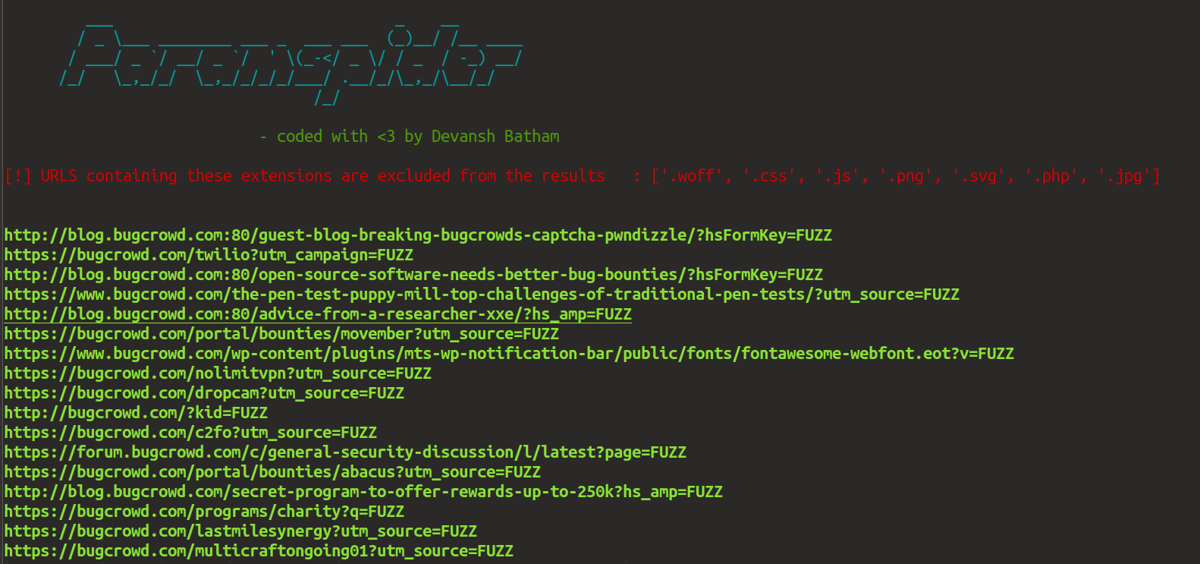
First, the user runs ParamSpider against the target domain. The tool can be configured to exclude URLs with specific extensions – such as .jpg or .svg – and generates a text file with the results.
ParamSpider also supports nested parameters, which can sometimes crop up secret tokens not profiled in the web archive.
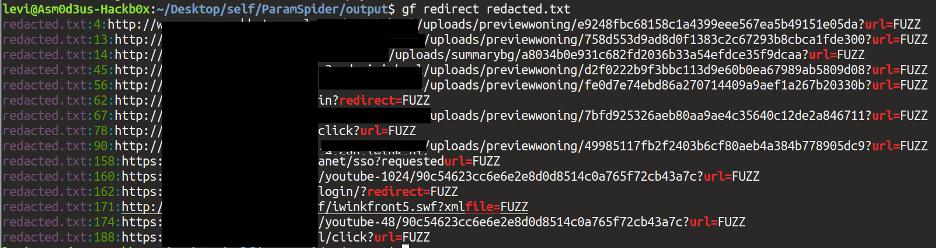
Next, using GF, a wrapper that creates shortcuts to long grep commands, the user can query the results for potential vulnerabilities.
Batham has released several custom .json extensions for GF that discover vulnerability patterns such as XSS and open redirect.
Finally, the user can employ a fuzzing tool to check for vulnerabilities in the discovered URLs. Batham has released OpenRedireX, a fuzzing tool to discover open redirect vulnerabilities.
He will soon release other fuzzers for LFI, CRLF, and SQL injection.
Overall, the tool has received positive feedback from the community. Some researchers have been able to apply it to find critical bugs.
However, the tool does have occasional glitches, as users have pointed out on Twitter, and Batham is addressing them.
Batham is working on improving the hacking tool. He will be releasing more GF profiles in the future to cover other types of vulnerabilities.
The researcher is also working on extending the ParamSpider’s reach to go beyond scraping web archives and is developing additional modules that will find parameters through active scanning.
RECOMMENDED Brim network forensics tool makes juggling large traffic logs easy






