ZDI releases full technical details of PHP deserialization vulnerability in Drupal core
The perils of PHP deserialization vulnerabilities were pulled into focus once again this week, as Trend Micro’s Zero Day Initiative (ZDI) released details of a critical exploit chain that was recently addressed by the Drupal security team.
Back in January, Drupal issued a security patch to mitigate the content management framework’s exposure to a remote code execution (RCE) vulnerability that could be exploited via PHP’s built-in phar stream wrapper – a feature that allows developers to access code within a bundle via a URI.
Three months on, zero-day disclosure platform ZDI has published a technical blog post detailing its purchase of this, along with another bug from researcher Sam Thomas, who demonstrated how a chained exploit could allow “one-click to code execution” on target Drupal sites.
In order for the exploit to work, an attacker must upload three malicious image files to the target server and entice a site administrator to follow a crafted link.
As ZDI notes, this multi-stage attack is “not exactly the smoothest exploitation path”. However, if everything works out, the attacker will be able to achieve code execution as the web server:
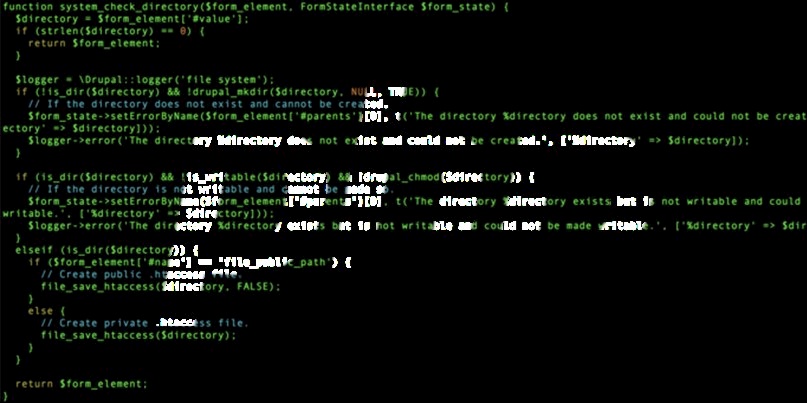
[The] unserialization bug [is] triggered through the file_temporary_path request parameter located at the /admin/config/media/file-system endpoint.An attacker may specify the phar:// stream wrapper to point the file_temporary_path parameter to a malicious phar archive uploaded to the Drupal server prior to the attack.
From Thomas’ presentation, the file operation !is_dir($directory) is sufficient to cause PHP to trigger unserialization of the metadata stored in the phar archive
Through the POP chain exploit technique, an attacker may use a crafted phar archive to execute arbitrary code in the context of the web server.
One to watch
Thomas, director of research at UK-based Pentest Limited, has been shining fresh light on PHP deserialization over recent months.
The Drupal exploit was based on research (PDF) he presented at Black Hat USA last year, and his work also featured in PortSwigger Web Security’s Top 10 Web Hacking Techniques of 2018.
Drupal has now fixed the vulnerability in its CMS framework, but ZDI said Thomas has demonstrated how exploits based around PHP deserialization are a growing concern.
“Unless PHP decides to modify the phar archive processing behavior, programmers will need to be extra vigilant when passing user-controlled data through file operators,” the company said.
Thomas agrees that PHP deserialization bugs will not be going anywhere soon.
“I definitely think it’s one to watch,” he told The Daily Swig. “It has been really rewarding to see others find examples since I gave the talk.”
Indeed, since his presentation in Las Vegas and elsewhere, researchers including Steven Seeley and the RIPS Tech team have picked up the mantle to demonstrate their own exploits based on PHP deserialization techniques.
Those who are interested in learning more should check out Thomas’ presentation at BSides Manchester last year.
RELATED Fresh exploit takes the shackles off disabled PHP functions






