Top infosec trends in the social media spotlight this week

Another fast-moving week in security has been topped off with reports that a former senior employee at NSO Group has been arrested and charged with stealing the organization’s proprietary code and attempting to sell it on the dark web.
NSO is an Israeli hacking organization notorious for peddling malware that enables authorities to break into smartphones.
According to reports, a 38-year-old former employee downloaded NSO’s proprietary malware and attempted to sell it for $50 million in cryptocurrency.
The individual, who is believed to have been fired from NSO in April, is said to have circumvented the group’s data loss protection software before hiding an external hard drive containing the code under a mattress in his home.
It will be interesting to see how this story develops over the coming days. In the meantime, however, many have said the NSO case simply goes to highlight the fact that organizations involved in the proliferation of malware are in no way immune to insider threats.
Over in the UK, the National Health Service (NHS) celebrated its 70th anniversary on Wednesday.
This momentous occasion was, however, dampened by the news that a coding error resulted in 150,000 patients’ data being shared against their will.
Of course, this latest breach follows last year’s devastating WannaCry outbreak, which affected 47 NHS trusts across the UK.
Back in November, NHS Digital, the institution’s information and technology partner, unveiled a £20 million security initiative.
The Department of Health and Social Security later pledged to spend a further £150 million over the next three years, but some have questioned whether this will be enough to safeguard the NHS from the next big malware attack.
In surveillance news, the National Security Agency (NSA) has purged “hundreds of millions” of records logging phone calls and text messages it had gathered since 2015.
According to a statement from the agency last week, the mass-deletion of these records was undertaken after NSA analysts noted “technical irregularities” in some data received from telecommunications service providers.
“These irregularities also resulted in the production to NSA of some call detail records (CDRs) that NSA was not authorized to receive,” the statement read. “Because it was infeasible to identify and isolate properly produced data, NSA concluded that it should not use any of the CDRs.”
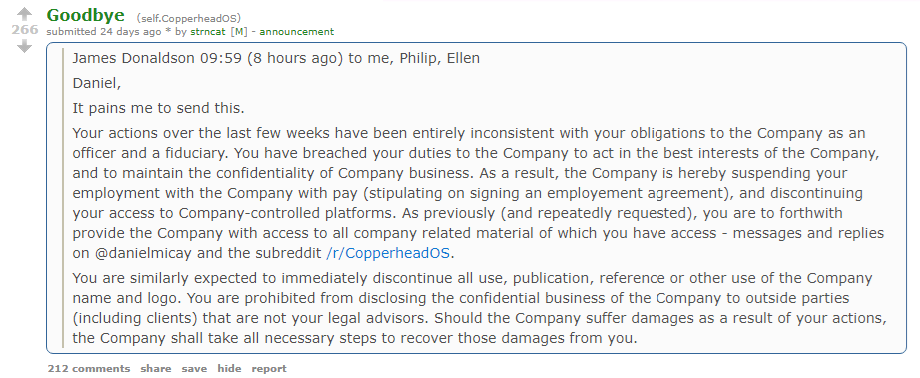
And finally, it appears that CopperheadOS – a security-focused mobile operating system – has been placed on the chopping block, after an internal dispute resulted in three developers being fired.
Copperhead initially launched as an alternative OS for Android devices back in early 2016. According to corporate literature, it features protection against zero-days, a hardened kernel, and stronger sandboxing and isolation for apps and services.
Users received an indication that all was not well in the Copperhead camp last month, when a Reddit user purporting to be a member of the development team published a post outlining his termination.
Last week, the developer came forward with another post (under a different account), which outlined his intention of taking the project forward under a different name.
“It remains to be seen how much of the previous code needs to be dropped to move on, but everything already has to be done over again for Android P and I know how to do it all from scratch if necessary,” he said.
“Only a very tiny fraction of what I want to have implemented in an initial year with a proper development team was already done, so it’s not the end of the world even though it really hurts.”