Industry rocked by APT-linked attacks leveraging zero-day browser and OS vulnerabilities

Security researchers are being targeted in a widespread hacking campaign attributed to North Korea state-sponsored threat actors.
Yesterday (January 25), Google’s Threat Analysis Group (TAG) disclosed details of the operation which it said was conducted by North Korean government-backed assailants.
Over the past several months, Google says, the group has targeted security vulnerability researchers with the intent to infect their machines with malware.
The malware opened up a backdoor that served to facilitate communication between compromised machines and the attacker-controlled command and control server.
Google said that the attack was successful even on computers running up-to-date versions of the Chrome browser and Windows 10, fueling concerns that the malicious hackers are exploiting zero-day vulnerabilities.
The malware contained techniques previously seen used by APT38, or Lazarus Group, which has ties to North Korea.
Behind the veil
Google detailed how the threat actors, using aliases including ‘James Willy’, ‘Zhang Guo’, and ‘Billy Brown’, used various tactics to lure potential victims.
The group hid behind a fake vulnerability research team, ‘BrownSec3 Labs’, and an accompanying technical blog containing write-ups and analysis of publicly disclosed vulnerabilities.
The blog also featured guest posts from legitimate researchers, who had seemingly been duped into submitting content in order to give the blog more credibility.
“In order to build credibility and connect with security researchers, the actors established a research blog and multiple Twitter profiles to interact with potential targets,” Google’s TAG researchers explained..
“They’ve used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits, and for amplifying and retweeting posts from other accounts that they control.”
Read more of the latest news about malware and attacks
It was through this channel that the group was able to push malware onto devices owned by numerous unknowing members of the cybersecurity community.
A post detailed ‘DOS2RCE: A New Technique to Exploit V8 NULL Pointer Dereference Bug’ was uploaded onto the popular /netsec subreddit, which is well known for sharing credible exploits and original security content.
A victim would simply have to click a link to the blog, and “shortly thereafter, a malicious service was installed on the researcher’s system and an in-memory backdoor would begin beaconing to an actor-owned command and control server”, said Google.
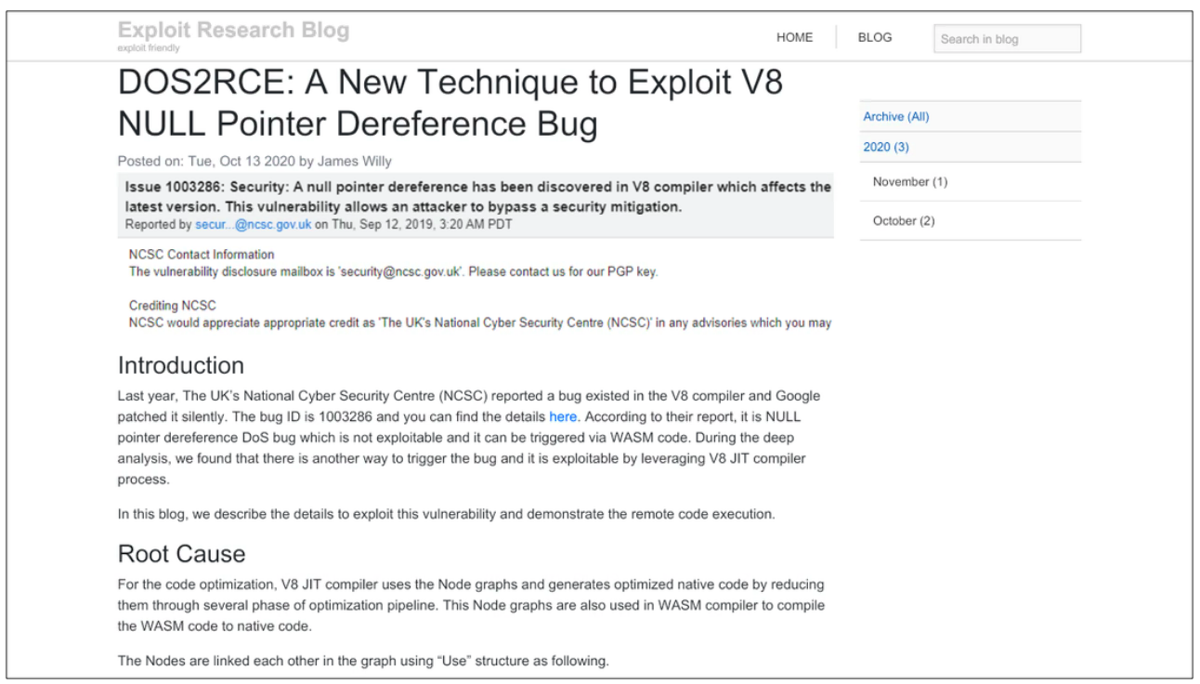 A screenshot of the malicious blog shared on /netsec that contained the malware
A screenshot of the malicious blog shared on /netsec that contained the malware
Unsociable network
Another route to compromise saw the attackers reach out to security researchers on social media sites including Twitter, LinkedIn, Telegram, Discord, and Keybase, asking to collaborate on exploits.
The malicious actor would then send them a Visual Studio project file which contained the malware.
One such victim, researcher Alejandro Caceres, was contacted by ‘James Willy’ on Twitter, who approached him to help with a fake zero-day vulnerability.
Caceres wrote: “After providing a writeup on root cause analysis I realized the visual studio project he gave me was backdoored.”
He added: “Anyway, yes I was hacked. No, no customer information was leaked, this was on a private VM [virtual machine] for this exact reason.”
YOU MAY ALSO LIKE Critical zero-day RCE in Microsoft Office 365 awaits third security patch
Security researcher Richard Johnson was also hit in the widespread attack. He tweeted: “The vulnerability was real and complex to trigger. Fortunately, I only ran it in VM.”
Johnson added that in the end that the VM disk he was using was corrupted, and so the file “self-imploded”.
Elsewhere, researcher @BushidoToken was targeted by a Twitter user with the alias ‘z0x55g’. He wrote: “I can confirm I was targeted by ‘z0x55g’ via Twitter DMs asking about browser and Windows kernel 0day vulnerability research.
“I guess it was because I had commented about the Defender RCE and used to have #0day in my bio. But yikes! Stay vigilant.”
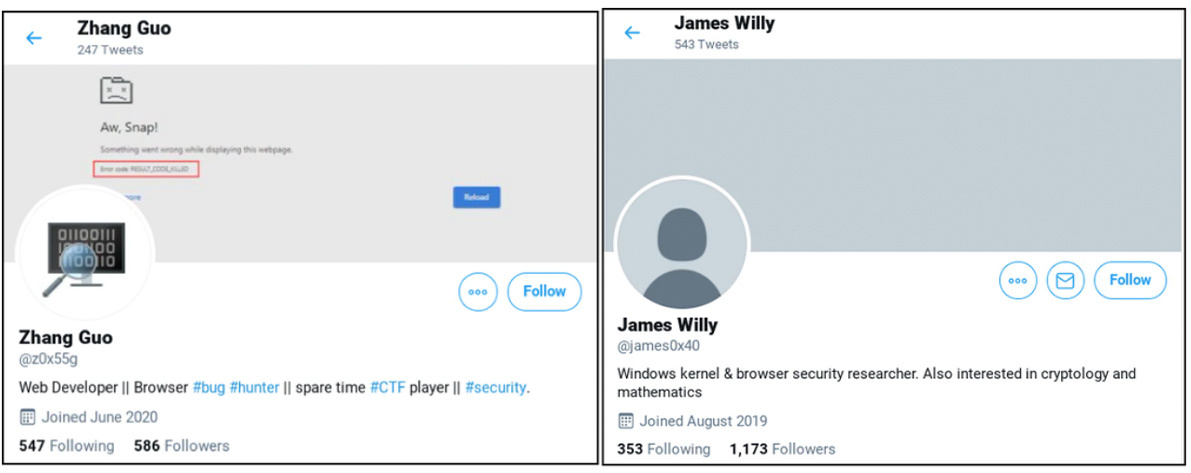 Screenshots of two of the accounts controlled by the malicious hackers
Screenshots of two of the accounts controlled by the malicious hackers
Multiple targets
Unsurprisingly, news of the brazen and far-reaching campaign has rocked the cybersecurity industry. The /netsec subreddit in which the malicious blog was posted has 399,000 members, and this doesn’t account for anyone who might have stumbled upon blog post via another channel.
“This is your regular reminder that to security researchers that you too are a target for APTs,” Eva Galperin, director of cybersecurity at the Electronic Freedom Foundation, wrote on Twitter.
Google has included a full list of the actor-controlled sites and accounts in the blog post, as well as details about the host IOCs.
“If you are concerned that you are being targeted, we recommend that you compartmentalize your research activities using separate physical or virtual machines for general web browsing, interacting with others in the research community, accepting files from third parties, and your own security research,” advised Google.
Since the malware potentially exploits zero-days in Google Chrome, the search engine giant reiterated that it offers cash rewards for vulnerabilities being exploited in the wild under its bug bounty program.
Google said: “We encourage anyone who discovers a Chrome vulnerability to report that activity via the Chrome [Vulnerability Rewards Program] submission process.”
YOU MAY ALSO LIKE SonicWall updates users after ‘highly sophisticated’ cyber-attack leverages zero-day vulnerabilities






