Malicious domains loaded through Google Translate

Researchers have discovered a new phishing technique that loads malicious domains through Google Translate, making it tricky for mobile users to notice they are being duped.
The URL-masking scam was exposed earlier this week by Akamai security researcher Larry Cashdollar, who found that a link contained in a phishing email was being loaded through Google’s popular language translation service.
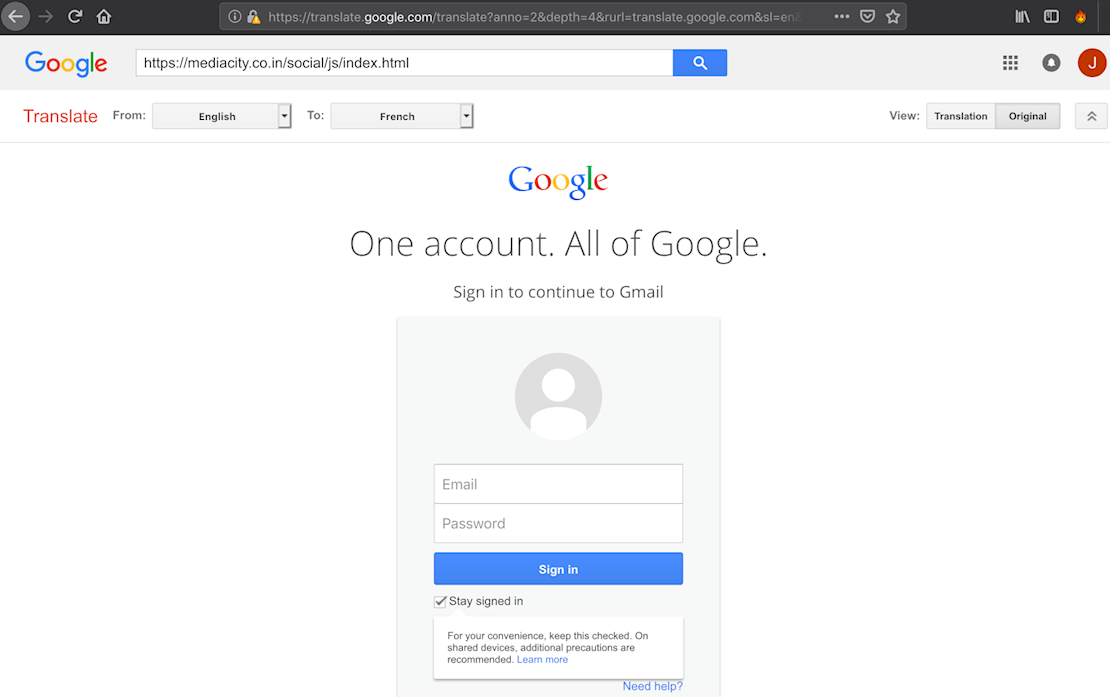
“Once the link is clicked, the page opens up to the form you see in the image above,” Cashdollar said in a blog post.
“Using Google Translate does a number of things: it fills the URL (address) bar with lots of random text, but the most important thing visually is that the victim sees a legitimate Google domain.”
One-two punch
Cashdollar’s discovery once again demonstrates how cybercriminals are going to increasing lengths to trick users into handing over their credentials.
However, although the researcher said this method of obfuscation might enjoy “some success” on mobile devices, the Google Translate technique falls short on desktop, where the malicious URL is much easier to detect.
That being said, those unfortunate enough to fall for the scam were redirected to a second phishing domain, where attackers attempted to get a second bite of the cherry by asking for their Facebook login details.
“It isn’t every day that you see a phishing attack leverage Google Translate as a means of adding legitimacy and obfuscation on a mobile device,” Cashdollar said. “But it’s highly uncommon to see such an attack target two brands in the same session.
“One interesting side note relates to the person driving these attacks, or at the least the author of the Facebook landing page – they linked it to their actual Facebook account, which is where the victim will land should they fall for the scam.”
Ultimately, despite the novel use of Google Translate to obfuscate malicious domains, the initial attack vector here is still a traditional phishing email.
For Cashdollar, the advice to users is clear: “The best defense is a good offense. That means taking your time and examining the message fully before taking any actions.
“Does the from address match what you’re expecting? Does the message create a curious sense of urgency, fear, or authority, almost demanding you do something? If so, those are the messages to be suspicious of, and the ones most likely to result in compromised accounts.”






