Network operations team stops data-stealing malware in its tracks

A would-be attack that threatened to deploy ransomware on the Black Hat Asia network was thwarted last week by a team tasked with protecting the event’s digital infrastructure.
The Network Operations Center (NOC) is responsible for keeping the conference’s networks and delegates safe from malicious actors – no easy task during one of the biggest hacker events of the year.
At Black Hat Asia, which took place last week in Singapore, NOC operatives spotted an attack attempting to steal attendees’ personal details, mine Monero, and deploy ransomware on the internal network.
Bart Stump, NOC team lead and solutions architect at Red Sky, explained: “We saw what was looked to be a pretty serious attack from the internet towards the registration servers, so they were trying to run a ‘red shell’ that didn’t exist and from there PowerShell a command that downloaded and ran malware.”
Stump added: “So basically this malware was sending out spam, it was then going to start Monero mining, it was then going to – well it did – run an entire port scan across the entire 10/8, then connect to 10,000-plus external hosts. Then in the secondary stage… credential theft, and then it threw ransomware in there as well.”
Luckily, the team spotted the malware and halted it before it was able to cause any harm.
“They were trying all this on the register… that’s what we’re trying to avoid – that would definitely be a bad day for all of us,” said Stump.
“I feel in my heart of hearts that if you get this malware and you don’t notice all of these things, you deserve it,” joked Neil Wyler, another NOC team leader and threat hunter at RSA. “This is not a quiet piece of malware.”
Wyler and Stump are part of the dozen-or-so-strong Black Hat Events NOC team, which features security representatives from several vendors, including RSA, Palo Alto Networks, Gigimon, MyRepublic, Cisco, and Ruckus.
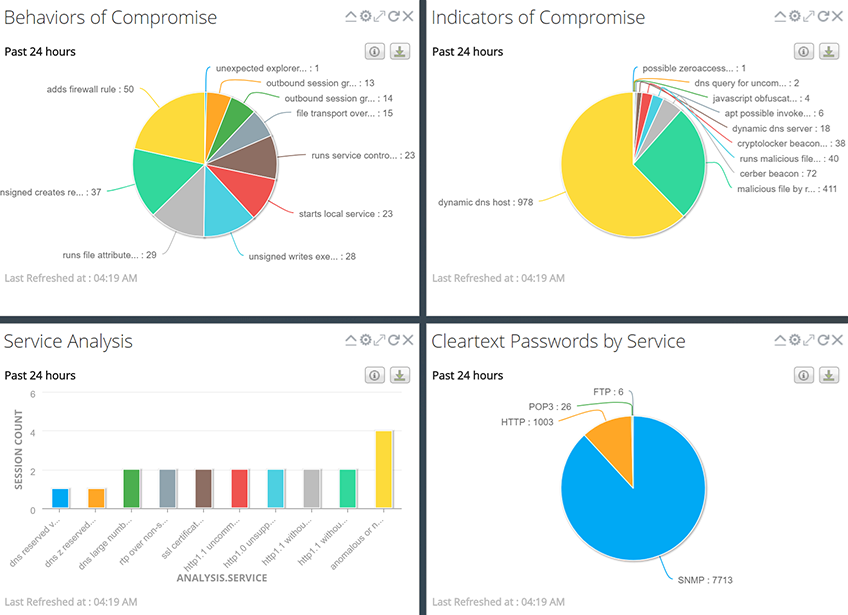 Black Hat Asia NOC dashboard (Image: RSA)
Black Hat Asia NOC dashboard (Image: RSA)
At each Black Hat show, the companies partner to share their ideas, skills, and experience in the hopes of stopping malicious attacks against the organizers and attendees.
Part of their arsenal used to detect cyber-attacks is a customized dashboard, affectionately known as ‘Dashy McDashface’.
The dashboard, built using a tool from Demisto, which was recently acquired by Palo Alto, pulls together metadata from across the partnering vendors and displays it in real time.
Using this tool, the NOC operators can keep an eye on the networks and monitor traffic, looking for potential threats as well as bad opsec practices.
Interestingly, the team doesn’t block malware. Instead, it sends a captive portal message warning a victim that they have been compromised – a feature unveiled at Black Hat Asia this year.
Wyler said NOC staff are on hand to help users who have been compromised, rather than block malicious traffic altogether.
He told attendees: “Most of the traffic that we’re seeing that might be consider to be bad, we just allow to continue on the network.
“We don’t want to be responsible for someone’s demo failing [during training or briefing sessions], so we let that traffic go by.
“But if we see something which is targeted towards the core infrastructure or the registration network, that’s when we know there’s no reason someone should be hitting those things and we need to take action.”
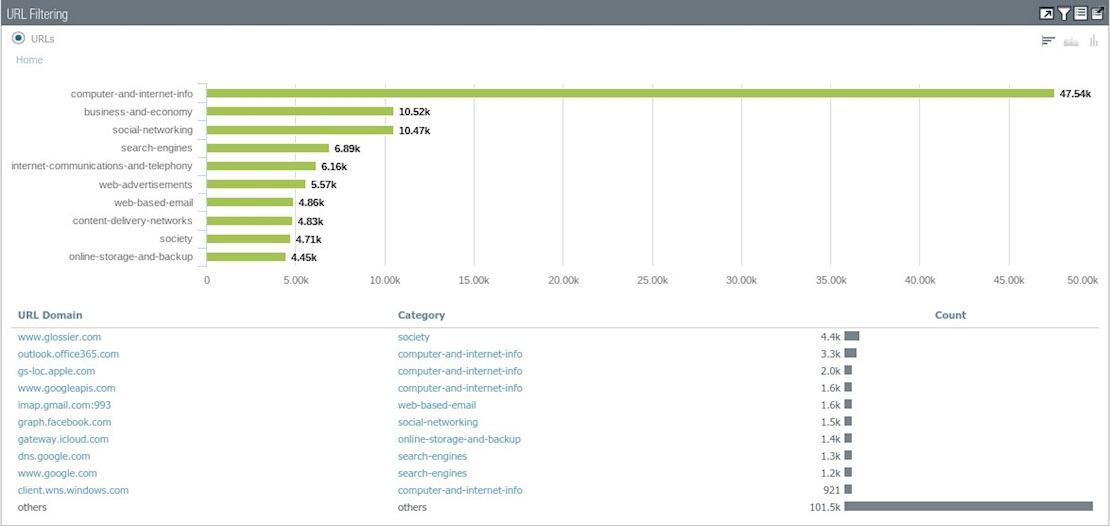 Black Hat Asia NOC dashboard (Image: Palo Alto Networks)
Black Hat Asia NOC dashboard (Image: Palo Alto Networks)
Attendees at Black Hat Asia are known to take encryption seriously.
The number of secure devices seen on the networks has been as high as 95% – a stark contrast to the 60% seen at the show in Las Vegas, US.
Delegates are also less trusting of the conferences WiFi networks. Figures showed that there were 962 unique devices logged on during the two-day conference, which saw more than 2,500 delegates.
“The one major thing that stands out, and actually gets better every show, is the amount of encrypted traffic that we’re seeing,” Sandra Wenzel, consulting engineer at Palo Alto Networks told The Daily Swig.
“We were seeing a lot of things in cleartext come through like credentials, emails, all of that. That’s gotten a lot better with each show.”
Wenzel, who has been a partner in the NOC for seven shows, said the main issue they see at Black Hat Asia is people not protecting their own privacy.
“Cleartext credentials, people doing sending texts in the clear and not really covering their assets or what they’re doing, people just not realizing where they are,” Wenzel added.
“I mean, you’re in a hacker conference and you’re doing these things, and we’re able to see these things. So it [the main issue] is not really covering your tracks very well.”






