Mind the gap

Moves to make it easier to use contactless payments on public transport systems have eroded the security of mobile wallets, security researchers have discovered.
Before 2019, Apple Pay and Samsung Pay did not allow payments unless the mobile device was first unlocked by a fingerprint, Face ID, or PIN.
But to make contactless payments easier during the pandemic, ‘public transport schemes’ were introduced by train and metro systems in many cities worldwide that made it possible for travellers to pass through a barrier without unlocking their phones.
Transport cards
To this end, ‘transport cards’ were made available by Visa, MasterCard, and Amex to travellers in Japan, the UK, the US, and China.
Once a traveller has enrolled and added a transport card to their wallet, they can enter, for example, a metro station, passing through the gates without unlocking their phone.
As a result of extensive research, a security research team from Positive Technologies found inconsistencies in contactless payments for public transport schemes that lead to potential fraud when mobile phones are lost or stolen.
Catch up with the latest mobile security news
The researchers discovered purported vulnerabilities in Apple Pay, Samsung Pay, and Google Pay that allow attackers to hack the Transport Card credentials connected to stolen mobile devices on which public transport schemes are activated.
They subsequently demonstrated how these compromised credentials might be used to make fraudulent purchases on other terminals and not only those limited to public transport. Such attacks would work up to the point a victim reports a theft and compromised card credentials are cancelled by their bank.
Cryptogram confusion
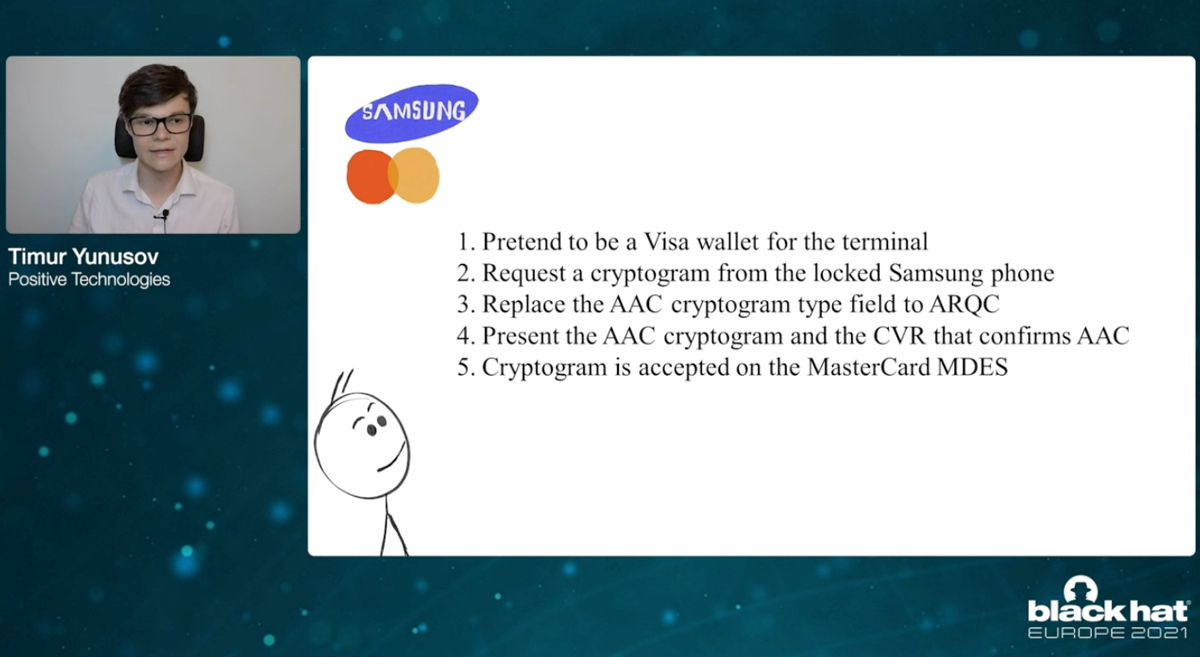
One of the attacks discovered is the so-called cryptogram confusion attack, which relies on “different views on the cryptogram type from mobile wallets and cards from one side and authorisation hosts from another”.
Results from attacks were dependant on both the card type (whether Visa, MasterCard or AMEX) and payment method (Apple Pay, Google Pay or Samsung Pay), and in many cases required the use of modified or compromised terminals.
However, since many fraudsters use compromised terminals for card attacks this in itself is not a major hurdle, and this fraud tactic is prevalent in Latin America, in particular.
The research was presented in a talk entitled ‘Hand in Your Pocket Without You Noticing: Current State of Mobile Wallet Security’ and delivered to the Black Hat Europe conference last week.
 Positive Technologies reported their findings to payment providers prior to their Black Hat presentation
Positive Technologies reported their findings to payment providers prior to their Black Hat presentation
Opaque disclosure
Timur Yunusov, a senior security researcher at Positive Technologies, said that the researchers had reported their findings to payment service providers prior to going public.
The vulnerable software is created and reviewed by Visa and MasterCard, so these financial services firms are more integral to the issue than either Apple or Samsung. Transport providers are the least involved and weren’t contacted by the three researchers – Yunusov, his PT colleague Artem Ivachev, and independent researcher Aleksei Stennikov.
The subsequent disclosure and remediation process was somewhat opaque.
Yunusov explained that at “some point between April and October 2021, the cryptogram confusion attack was fixed by MasterCard. Visa’s reaction was silence. But after similar research was published by the University of Birmingham they have responded with their traditional ‘as long as we don't see these attacks in the wild, we are not planning to change anything, we are sufficient, our risk-based business model works’,” said the researcher.
Worst-case scenarios
He went on to outline the worst-case scenarios of what might be possible through a successful fraudulent attack.
“{In the] worst-case scenario – attackers use stolen phones and they could use these stolen mobile wallets to pay in supermarkets, stores, anywhere in the world, presuming that these cards were not blocked by the card/phone owners,” Yunusov told The Daily Swig.
“MasterCard closed this possibility for Samsung Pay as I explained previously. Visa didn’t. So it’s still possible with the pair Apple/Visa and GPay/MasterCard.”
“For other pairs such as Apple/MC and Samsung Pay (currently after all fixes) hackers need special equipment for that – modified POS like the one we used in our last research.”
In response to queries from The Daily Swig, Visa said the research covered something that fell short of posing a ‘real world’ risk, adding that it was comfortable with its current security controls.
Visa cards connected to mobile wallets with transit features are secure and cardholders should continue to use them with confidence. Variations of contactless fraud schemes have been studied in laboratory settings for more than a decade and have proven to be impractical to execute at scale in the real world.
Multiple layers of security are used to protect payments and consumers benefit from Visa’s zero liability guarantee. Visa takes all security threats seriously and continuously evolves its payment security capabilities to protect cardholders from the latest real-world threats.
Mastercard is yet to respond to our request for comment.
More details on the research, including a rundown on how the payment technology works, descriptions of attacks, and suggestions for remediations can be found in a white paper. The research is the latest in a series that previously covered potential point-of-sale (POS) authentication control hacks and cheating the then contactless limit.
YOU MAY ALSO LIKE Laws and regulations need to change to secure world’s digital infrastructure






