Phishing risk from rogue pop-ups only partially addressed
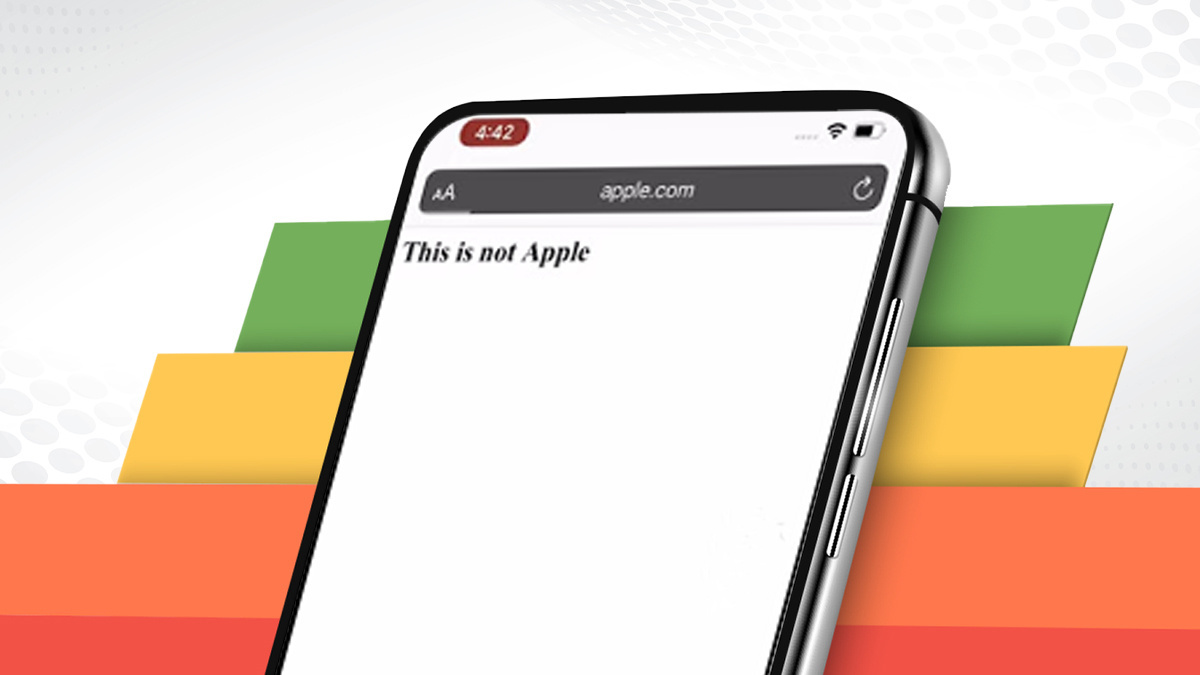
UPDATED A set of address bar spoofing vulnerabilities that affect a number of mobile browsers leave smartphone users at heightened risk from phishing attacks.
Independent security researcher Rafay Baloch and Tod Beardsley, research director at Rapid7, discovered similar flaws in a range of mobile browsers including Apple Safari, Yandex, and Opera Touch.
Less common browsers including the Bolt Browser and RITS Browser were also affected.
Both Android and iOS device users of vulnerable mobile browsers were at risk from what are best described as important rather than critical security flaws.
Patches for iOS browser apps have already been released while, in most cases, Android application fixes are in the works, according to Rapid7.
Pop-up peril
The vulnerabilities discovered all involve JavaScript manipulation.
The vulnerability class is merely 'Address bar spoofing' and it’s an instance of CWE-451, described as “UI Misrepresentation of Critical Information”, according to Rapid7's Beardsley
Beardsley explains in a blog post: “By messing with the timing between page loads and when the browser gets a chance to refresh the address bar, an attacker can cause either a pop-up to appear to come from an arbitrary website or can render content in the browser window that falsely appears to come from an arbitrary website.
“In all cases, the victim would have to visit a website that the attacker can post executable JavaScript,” he added.
Catch up on the latest browser security news
Mainstream, highly trafficked websites such as Facebook, Reddit, Twitter, or other online forums generally do a “pretty good job” in protecting against “JavaScript shenanigans”, according to Beardsley, who said the security flaw is most exposed by hacker-controlled websites.
A victim might be tricked into visiting such websites through a phishing email, a phishing text message, or a post to a popular forum.
The issue is more acute than might otherwise be the case since there are few ways to “validate the source of data” on mobile phones other than the address bar. This, in turn, sets the scene for all manner of malfeasance.
“If your browser tells you that a pop-up notification or a page is from your bank, your healthcare provider, or some other critical service you depend on, you really should have some mechanism of validating that source,” Beardsley writes.
“In mobile browsers, that source begins and ends with the URL as shown in the address bar.”
Beardsley told The Daily Swig: “As far as I can tell, these vulnerabilities haven’t yet been used in the wild – we discovered these vulnerabilities through our own assessments.”
This story has been updated to add comment from Rapid7's Tod Beardsley
RECOMMENDED Microsoft unveils plans for Project Zero-style Chromium research project






