Necurs botnet sends 12.5m malicious emails in six hours

The infamous Necurs malspam botnot is being used to spread a major new ransomware campaign that’s already thought to have been sent to more than 12 million email addresses, security researchers have warned.
Last week, two separate reports from Forcepoint Security Labs and F-Secure outlined the proliferation of a “massive malicious email campaign” that comes loaded with a new version of Scarab ransomware.
The malware is being delivered via the Necurs spam botnet, which has previously been linked to the distribution of the Dridex and Trickbot banking trojans, along with the Locky and Jaff ransomware strains.
Forcepoint researchers said the email campaign started at approximately 7:30am UTC on November 23, and had reached more than 12.5 million inboxes by 1:00pm.
The email uses the subject line ‘Scanned from [printer company name]’ – a theme that is known to have been utilized for previous Locky ransomware campaigns distributed via Necurs.
According to Forcepoint, the principal target countries are the US, Australia, UK, France, and Germany. The graph below shows the per-hour volume of Scarab/Necurs emails blocked by the security team between 7:00am and 12:00pm UTC:
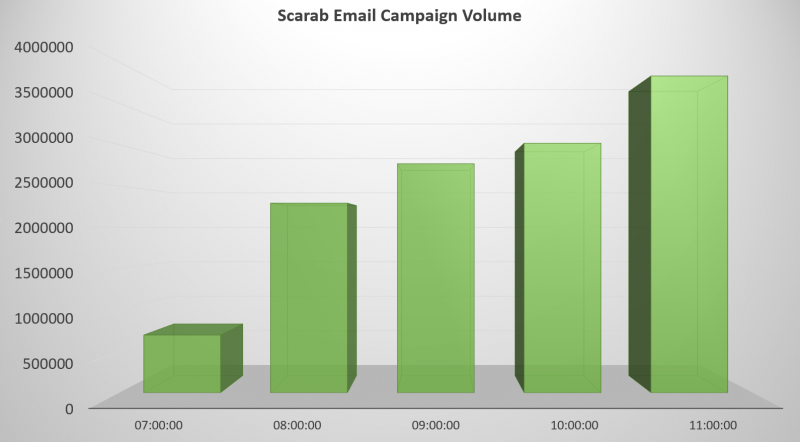
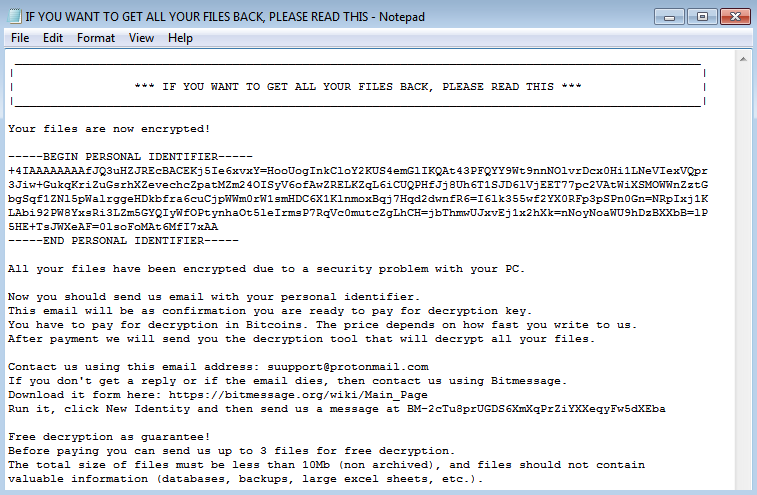
Scarab is a relatively new ransomware variant first observed in June. This latest version is based on the open-source ransomware trojan Hidden Tear, and drops the following ransom note after the encryption:
Discussing the malware’s distribution model, F-Secure researcher Päivi Tynninen said: “The spam campaigns from Necurs are following the same format from campaign to campaign, consisting of social engineering subject line themes… with very minimal text body contents and spiced up, usually with malicious attachments.”
She added: “We’re interested to see the future affiliations of this massive botnet and observe how it’s able to change the trends and popularity of malware types and certain families. In the meanwhile, we’ll keep blocking these threats.”






