Greater protection for users wanting to obscure their virtual encrypted disks

Steganography – concealing an image or document within another file – has been elevated to another level, as new research shows how it might be possible to hide an encrypted partition on a hard drive.
The contents of virtual encrypted disks remains opaque, although their very presence can create problems for human rights activists, journalists, and others that use the technology.
The possession of disk encryption software (for example VeraCrypt) is itself easily detected, and would tip-off authorities that a target has concealed presumably sensitive information.
This risks the user being subject to coercion or “rubber-hose cryptoanalysis and aggressive password disclosure statutes”, says Dominic Schaub, head of research and development at Discrete Integration Corp.
Discrete is therefore developing a technology to conceal the presence of a hidden encrypted drive on a machine.
Perfectly deniable steganographic disk encryption offers a means to “safeguard sensitive information against forced password disclosure by concealing its very existence”, according to Schaub.
Potential users of the technology include business travellers looking to safeguard commercially sensitive information from inspection at border crossing posts, as well as agents working undercover.
During a presentation at Black Hat Europe last week, Schaub demonstrated a self-concealing encryption/steganography suite.
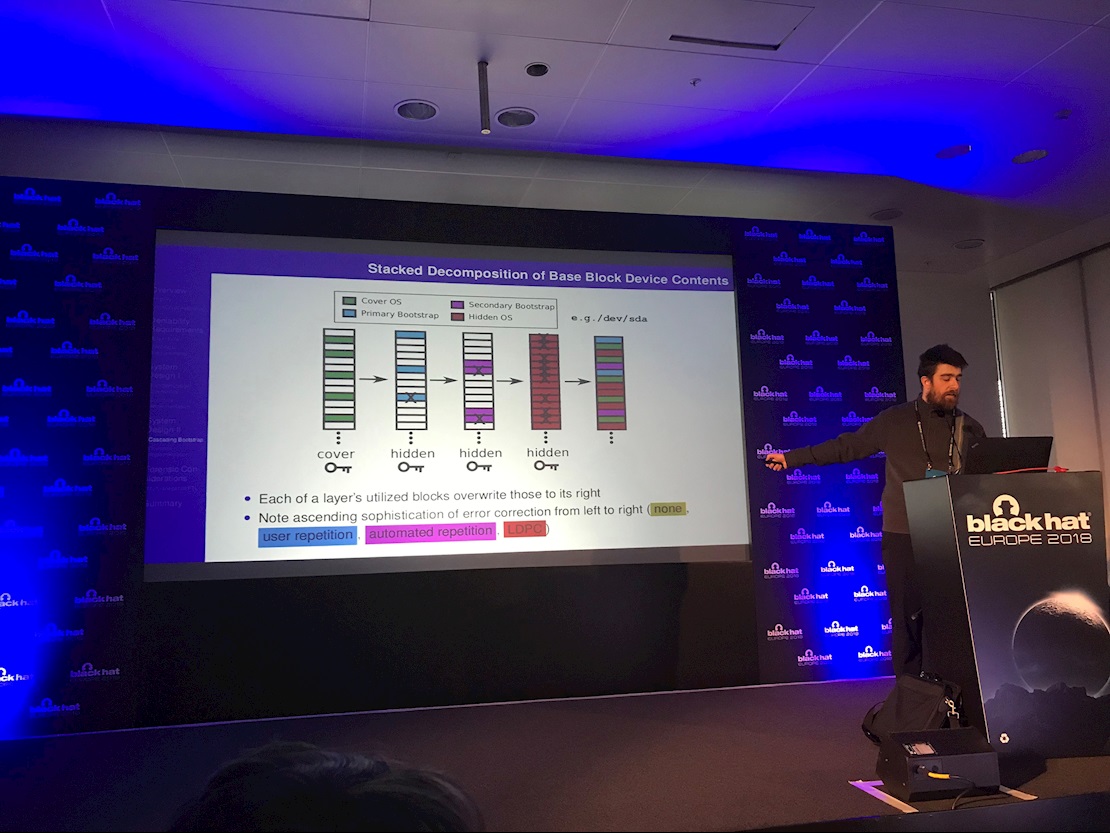
These steganographic tools “hide themselves in a self-recursive manner that renders them forensically invisible”, he explained.
The hidden, encrypted volume is contained on a system that presents as a default installation of Ubuntu, the decoy operating system (OS).
This decoy system can be used to access innocuous content such as weather reports or a decoy webmail account. The machine can also be used to store and access sensitive content using the hidden encryption/steganography suite.
Use of the hidden tools developed by Schaub is deniable because they are designed to bootstrap themselves into existence without generating any incriminating artifacts.
By design, the tool can only be activated by an authorized user. Once activated, it fires up a “hidden, fully functional OS” through a process that “generates no forensic evidence and requires no outside binaries”.
The suite works in much the same way as VeraCrypt’s hidden volume/OS feature but comes with added benefits, as Schaub explained.
Unlike VeraCrypt, the decoy system employs Linux’s customary disk encryption (cryptsetup/dm-crypt) and requires no additional binaries, peculiar partition schemes (or inexplicable unallocated disk space), restrictions on cover-system write operations, or modification to TRIM settings.
In fact, the decoy appears bit-for-bit like a normal Linux system configured with only default parameters (e.g. repeatedly clicking ‘next’ during Ubuntu installation).
The working system is “fast, stable, and functional”, Schaub told delegates during his well-received presentation (PDF) on Thursday.
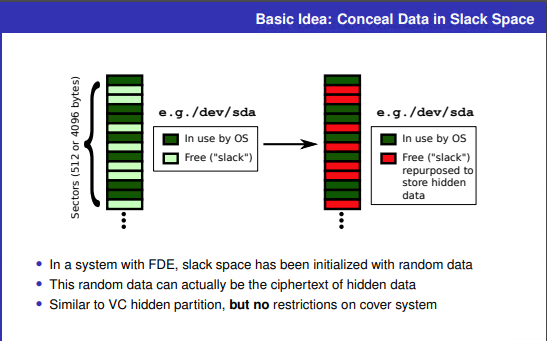
Information in the hidden virtual volume is secreted in unused disk space, encrypted hidden data masquerades as random data, and the hidden system itself is isolated from the cover system, he said.
For a large volume system, most slack space may never be overwritten. Schaub has developed a utility used in conjunction with his steganography suite that can be used to check the health of the hidden virtual volume.
Error correction and caching technologies mean that volume information and files can be recovered even if some data on the hidden volume is overwritten by the decoy system.
Conversely, the hidden system must reliably detect sectors used by the cover OS and avoid them.
Forensic analysis of a computer system suspected of steganographic activities is still possible, and for that reason users need a cover story. The system developed by Schaub offers protection at a technical level but even that might be undermined if a volume is imaged twice.
The suite developed by Schaub comes in at around 30,000 lines of code spanning the main kernel module, user space utilities (for installation and diagnostics), and various components of the bootstrapping system.
Development is still ongoing, but after Schaub tested it with both Arch and Ubuntu, no instability or data corruption was observed, and he confirmed that VirtualBox/Windows works “very well” on the hidden system.






