More than £8,000 has been raised after UK healthcare foundation allegedly threatened to take legal action

A security researcher has launched a GoFundMe campaign to secure legal representation after a responsible disclosure notice apparently went sour.
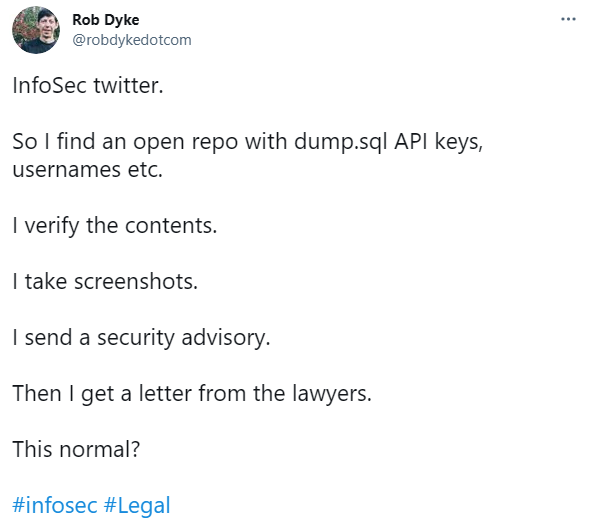
In a tweet dated March 8, Rob Dyke, an open source cybersecurity specialist and platform engineer, said he had discovered open code repositories in late February containing API keys, application code, usernames, passwords, and the URLs of third-party, embedded items.
Two open GitHub repositories were said to have been exposed online for two years, leaving plenty of scope for threat actors to exploit the information posted.
After verifying the contents and taking screenshots, the security researcher sent a private security advisory to the repo author – a common practice in responsible disclosure.
Dyke alerted the author to the public settings of the repositories and also warned that the application code contained within was based on an old PHP framework containing SQL injection and remote code execution (RCE) vulnerabilities.
The researcher added that he would keep the materials, in an encrypted fashion, for 90 days before destroying the records.
At first, the author thanked Dyke and took down the repos. However, some of the embedded elements were still available on public URLs, leading to a second private disclosure.
Dyke, once again, was thanked – but was also hit with a notice to serve from the organization’s legal team in the same breath.
Dyke was accused of committing offenses under the Computer Misuse Act 1990 and the Investigatory Powers Act 2016.
‘Sensible and responsible disclosure’
According to the researcher, an unnamed legal team demanded that he “give commitments that amounted to me acknowledging that I had unlawfully hacked into and penetrated systems and databases”.
“I made a sensible and responsible disclosure; I have not made threats at any time; nor have I intimated harm to the organization’s systems,” Dyke said.
RECOMMENDED Xerox legal threat reportedly silences researcher at Infiltrate security conference
When asked on social media exactly what he was accused of, Dyke said, “clicking links from one public website to another. Then telling the organization that I clicked the links”.
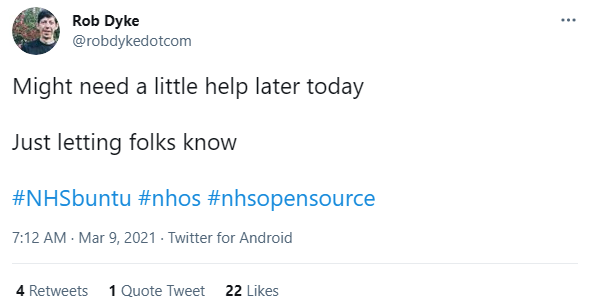
In a follow-up tweet dated March 9, Dyke posted:
“Might need a little help later today. Just letting folks know. #NHSbuntu #nhos #nhsopensource.”
GoFundMe campaign
Dyke did not originally disclose the name of the organization that threatened legal action as private information was still available online. However, the researcher did say, “If you knew who it was you’d be very disappointed”.
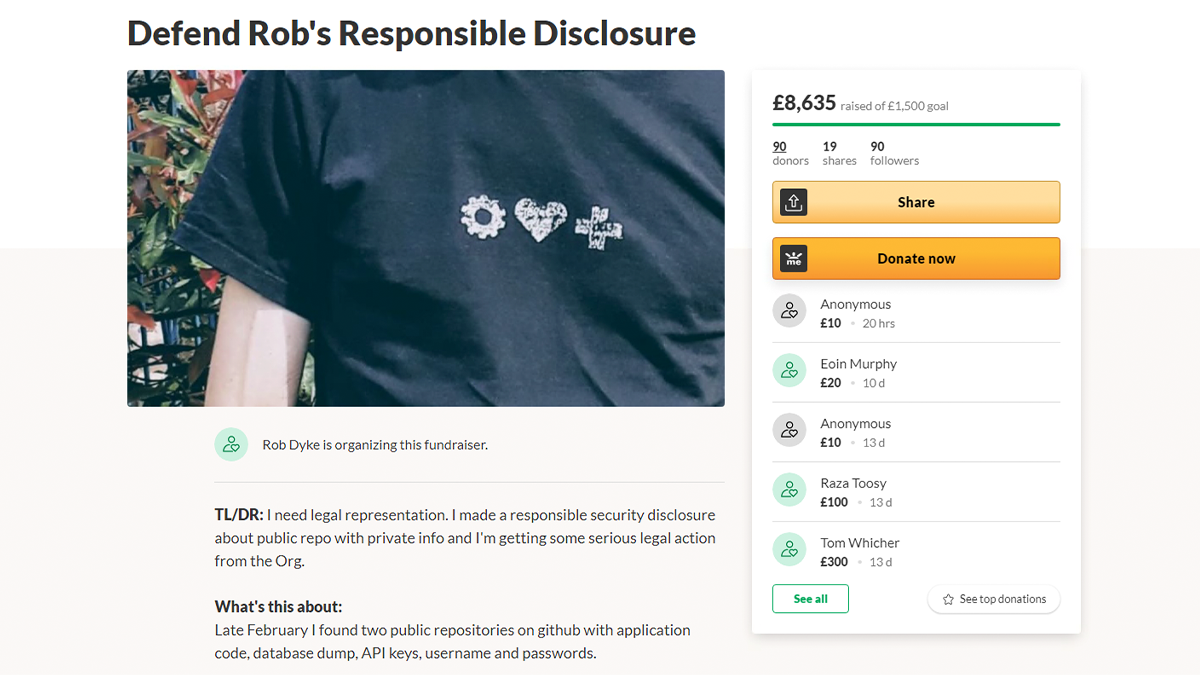
On March 9, Dyke sent out a request for recommendations for a lawyer familiar with technology and able to represent him, as well as roughly £1,500 to pay their fees.
A GoFundMe page was created to help cover these costs, and at the time of writing, £8,625 has been raised. Any donations that are not required for Dyke’s legal defense will be donated to Code Your Future.
The researcher has engaged a legal firm to act on his behalf.
“This is shitty bullying behavior from the organization,” Dyke said on March 9. “I won’t be identifying the organization. Suffice to say that they have a pile of public money that should be spent on doing Good Open Source Things rather than shooting the messenger.”
On March 24, Dyke named and confirmed to The Daily Swig that the organization as the Apperta Foundation, a clinical non-profit funded by the UK National Health Service (NHS).
In an email screenshot shared online, the researcher revealed a message allegedly sent by Northumbria Police who has requested to speak to him. The request for contact cited “a report of Computer Misuse”.
“I told @AppertaUK about passwords/keys/finace db they published on Github,” Dyke commented. “And this is what I get #cyberup”.
In response to a series of queries from The Daily Swig, an Apperta Foundation spokesperson issued the following statement:
On or about 26 February 2021, it is understood that an unauthorised individual or individuals breached a private portal to access financial information related to The Apperta Foundation. After taking professional advice, the Foundation took immediate action to isolate this breach and secure its systems.
The information implicated related purely to The Apperta Foundation’s financial information. We can assure the community that personal data was not targeted or accessed about individuals. The Foundation’s directors have a responsibility to protect its confidential information, including data and intellectual property owned by the Apperta Foundation. Its actions have been entirely proportionate to that responsibility.
The Apperta Foundation’s management is confident that all systems and security have been reviewed and all necessary steps have been taken to ensure the Apperta Foundation is protected and future threats are managed in accordance with best practice.
READ MORE Computer Misuse Act: Most UK cybersecurity pros fear breaking the law by simply doing their jobs