New web interface brings password-probing utility to the masses

Shhgit has been made available through a public web interface, drastically simplifying the process of finding sensitive material that’s inadvertently been published on code repository GitHub.
Earlier versions of the tool, which debuted last month, required those using it to have the technical chops to use a command-line interface.
The utility was therefore more or less restricted to serious bug hunters or security researchers, who remain the main target audience.
A web-based interface now opens up the Shhgit tool to the masses, while offering what amounts to a live feed of leaked secrets.
Potential users no longer need any technical knowledge to use the tool, which searches for secrets in GitHub and BitBucket.
Spy on the wire
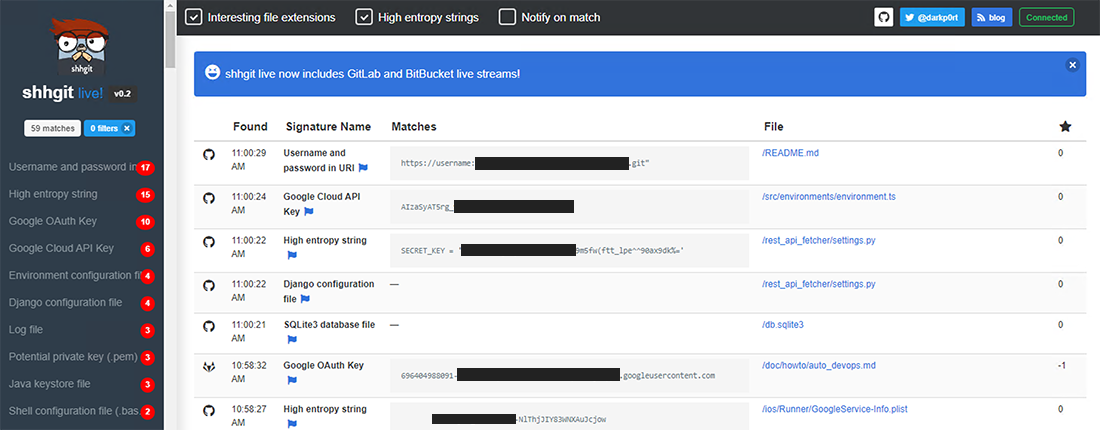
Shhgit, put together by developer Paul Price, listens to the GitHub Events API in order to find secrets and sensitive files that might appear across the repository’s code base.
As previously reported by The Daily Swig, secrets such as passwords and connection strings end up being published on GitHub because users fail to sanitize app setting and config files within their code, among other errors.
Similar tools such as Gitrob, for example, create a ready means for security researchers to comb through commit histories to find secret tokens from specified repositories, users, or organizations.
Shhgit, which takes portions of its code from Gitrob, does away with the need to specify targets, instead plugging itself directly into the GitHub firehose in order to generate a live feed of leaked secrets.
YOU MIGHT ALSO LIKE GitHub platform improvements are helping orgs keep their dependencies in check
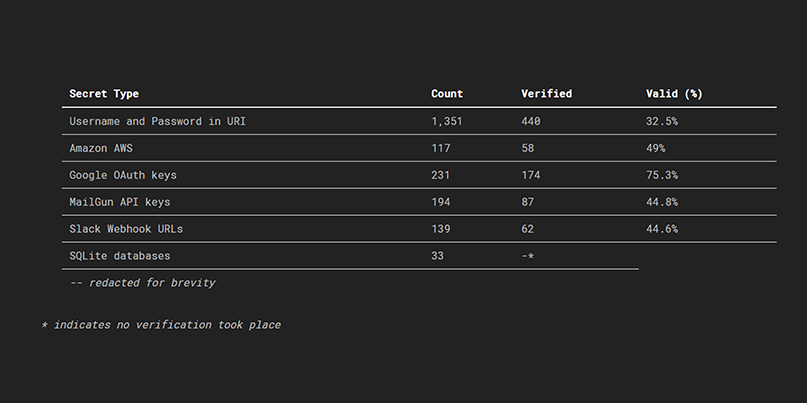
In a blog post this week, Price reports that the tool allowed him to quickly identify hundreds of secrets – half of which could be verified within seven minutes of them being committed.
The secrets included username and password in URI, Amazon AWS credentials, Google OAuth keys, and still yet more sensitive information.
“What I wasn’t expecting to find was valid package manager API keys, i.e., npm for Node.js; PyPi for Python; and NuGet for C#,” Price reports.
“The total number of downloads for these packages is in the millions. And the majority of these keys had publishing permissions. Meaning a bad actor could theoretically embed malicious code into the packages, reupload them without detection, and potentially infect millions of devices.”
Race condition
GitHub is actively scanning for secrets through its Token Scanning project.
The scheme means that, at least in theory, if any AWS secret keys are committed to GitHub, Amazon will be notified allow it to automatically revoke compromised credentials.
Recent academic research (PDF) found that many of the secrets accidentally committed to GitHub are cleaned up within 24 hours.
Shhgit, which is capable of flagging up leaked secrets within minutes rather than hours, features a button for reporting to users or organizations that they have inadvertently shared secrets.
The Shhgit utility has reached the stage of its development where it’s now akin to something like Shodan (where you can click on people’s insecure web cams) or VNC roulette, which famously allowed users to view unsuspecting users’ computer who had screen sharing).
RELATED Open source tool for bug hunters searches for leaked secrets in GitHub commits






