Citrix flags five-month-long breach; Israeli soldiers catfished by fake apps; and a Dever ransomware infection is forensically examined

Citrix’s nightmare start to 2020 continued this week, after the networking giant admitted that intruders roamed its networks for five months between 2018 and 2019.
Attackers – believed to be Iranian-backed – snaffled the personal and financial data of Citrix employees, contractors, interns, and job candidates and their dependents, security journalist Brian Krebs revealed yesterday (February 20).
The infosec community was aghast that Citrix had to be alerted to the breach by the FBI, and that the intrusion succeeded through one of the crudest methods going: password spraying.
Unlike credential stuffing, which can systematically try out millions of credentials pilfered in other data breaches, password spraying probes employee accounts using just a handful of common passwords.
Damningly, this suggests that Citrix mandated neither two-factor authentication (2FA) nor strong passwords among its employees.
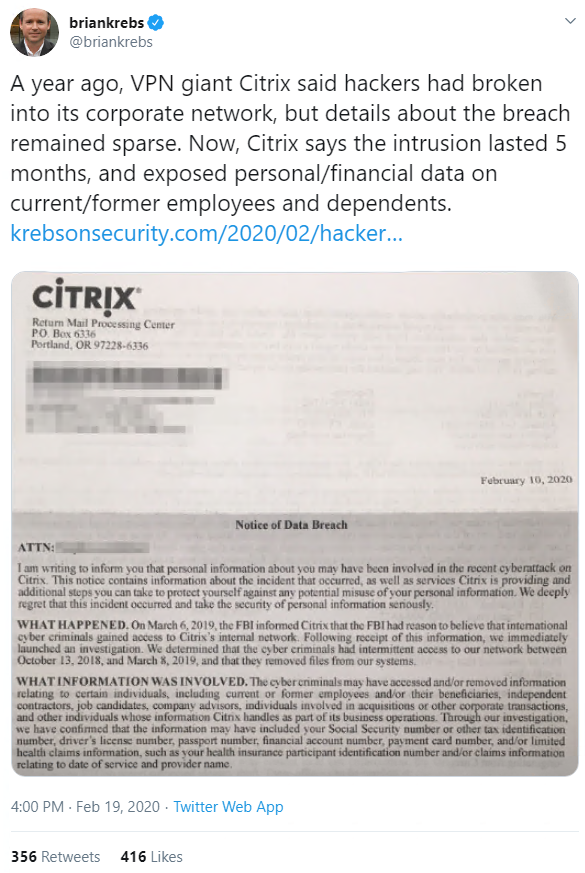
In line with US state laws on notifying victims of data breaches, Citrix alerted affected individuals to the incident in a letter dated February 10, 2020, a copy of which Krebs got hold of.
Citrix, which recently patched a vulnerability so bad it was labelled ‘Shitrix’, said the stolen information may have included Social Security Numbers or other tax identifiers, driver’s license numbers, passport numbers, financial account numbers, payment card numbers, and health claims data.
Hamas honeytrap
In espionage news, Israeli soldiers have been successfully ‘catfished’ by Hamas operatives for the third time in as many years, after similar incidents in 2017 and 2018.
The Israeli Defence Force (IDF) has admitted that dozens of servicemen were duped into downloading spyware disguised as snapchat-style messaging apps by Hamas operatives posing as teenage girls on Facebook, Instagram, and Telegram.
Even the most basic due diligence should have set alarm bells ringing: ‘Catch & See’, ‘ZatuApp’, and ‘GrixyApp’ were absent from major app stores.
Once downloaded the ‘messaging’ apps displayed an installation failure message, but then gave Palestinian militants the ability to take photos remotely, and access SMS messages, address-book information, and the device’s GPS location.
While the IDF claims to have taken down the infrastructure used by Hamas to control the infected devices, images of the teenage girls used in the scam are still floating around the internet, beyond the control of, and perhaps unbeknownst to, their copyright owners.
Dever deconstructed
Elsewhere this week, the infosec community was engrossed by an in-depth incident response report on a Dever ransomware attack posted on Twitter and Reddit on Sunday (February 16).
On his Wilbur Security blog, ‘JW’ recounted his forensic survey of the damage wrought by the attacker using Dever’s SMB scanning and persistence mechanisms, supported by password-pilfering tools Mimikatz and Lazagne, in a 14-minute spell spent inside the network.
His investigation revealed that the ransomware first breached the Utility Workstation, before moving laterally to infect the NAS and utility servers too, with consistent login credentials across the environment smoothing the path.
JW’s recommendations for mitigating ransomware infections, then, naturally included using different privileged passwords on every endpoint, as well as centralizing logs where possible and avoiding machine-to-machine communication over SMB unless essential.
The attackers – who JW was amused to find used AOL email addresses – didn’t get their $5,000 ransom since JW’s friend, who lost all his data, surmised that no decryptor is guaranteed to work.
Rogues gallery
In browser news, Google has purged more than 500 rogue Chrome extensions form its Web Store, after it was discovered that the apps were being used as part of an extensive malvertising campaign.
The security bods at Chrome teamed up with security researchers at Cisco’s Duo Labs to identify the offending extensions, which are believed to have had infected more than 1.7 million users’ browsers.
The takedown was recounted both by the Cisco Duo Lab researchers involved and on Google’s Security Blog.
In a similar vein, The Daily Swig reported on Wednesday (February 19) on the revelation that a popular Chrome extension that streamlines the YouTube interface – Magic Enhancer – has been logging the browsing history of users who click the wrong buttons during installation.
Size isn’t everything
And finally, the personal information of 10.6 million guests who stayed at MGM Resorts hotels landed on an underground hacking forum this week, with the data dump reportedly including those of Twitter CEO Jack Dorsey and pop star Justin Bieber.
Ten million is a big number, for sure, but as far as hospitality security incidents go, the MGM leak is still dwarfed by the roughly 500 million guests impacted by a breach of Marriott Hotels’ Starwood Hotels chain over a four-year period.
Perhaps unsurprisingly, MGM downplayed the impact, saying that the “phonebook information” that was mostly involved – like names, addresses, and telephone numbers – was publicly available anyway.
Nevertheless, around 1,300 former guests were notified by the hotel chain that more sensitive information, including passport numbers, had been exposed by the breach.
The story, which was broken by ZDNet on Wednesday (February 19), apparently started last summer when MGM discovered unauthorized access to a cloud server containing information about previous guests.