Twitter CEO hit by apparent SIM-swap attack, data leak impacts 400 million Facebook users, and the ‘dumbest’ password policies revealed

Text 2 tweet
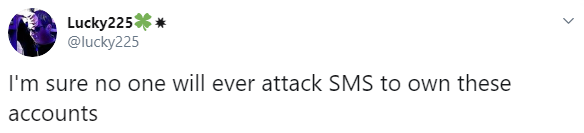
One of the biggest security news stories trending on social media this week actually involved a social media company, as Twitter announced it has temporarily revoked the tweet-via-SMS feature from its platform.
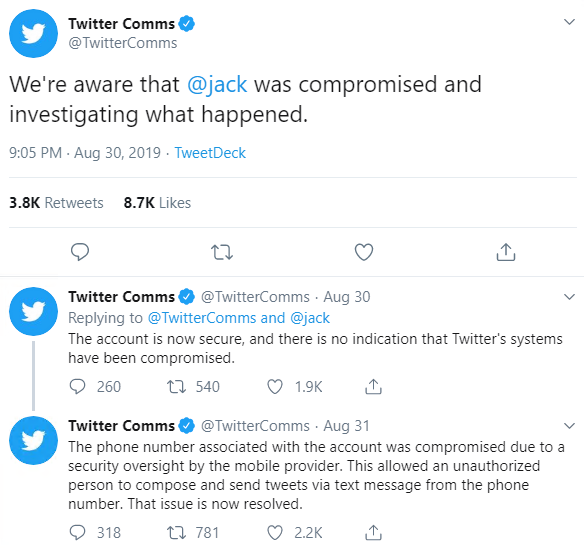
News of the rollback came after Twitter CEO Jack Dorsey’s account (@jack) was hijacked last Friday, with miscreants posting a slew of profanities and racist tweets.
Interestingly, it appears that this wasn’t a straightforward account takeover, but stemmed from a so-called SIM-swap attack, in which attackers persuade mobile carriers to switch a phone number to a new device.
“The phone number associated with the account was compromised due to a security oversight by the mobile provider,” Twitter said. “This allowed an unauthorized person to compose and send tweets via text message from the phone number.”
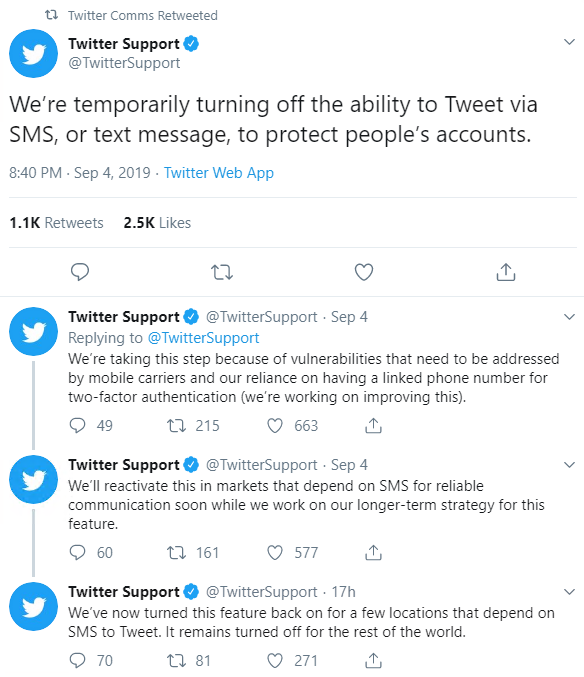
In the wake of the compromise, Twitter announced it was temporarily turning off the ability to tweet via SMS.
Some expressed concerns that the rollback would negatively impact users in nations that rely on SMS for reliable communication.
Mobile pwn
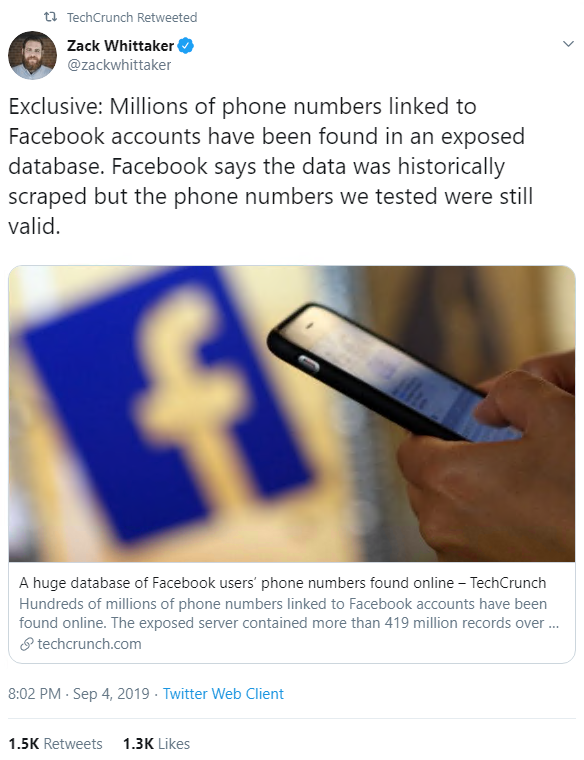
From one social media giant to another, Facebook was embroiled in a massive data leak that exposed the phone numbers of “hundreds of millions” of users.
According to TechCrunch, an internet-facing server containing more than 419 million records was discovered with no password protection, meaning “anyone could find and access the database”. Yikes.
Unsurprisingly, Facebook’s history of security missteps meant that many didn’t take kindly to the news:
Crash course
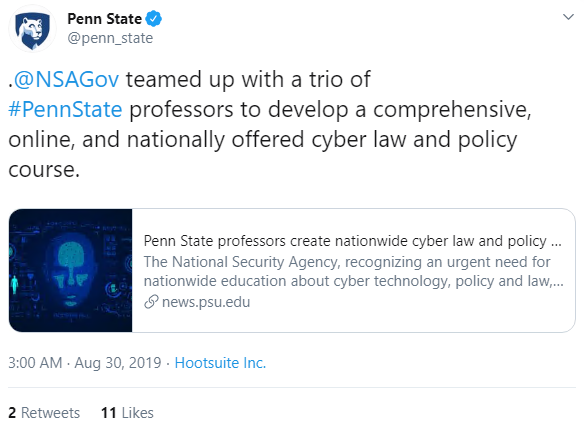
Staying in the US, anyone interested in brushing up on their cybersecurity policy and legislation now has access to dozens of NSA-approved online education modules.
The free-to-access ‘Principles of Cyber Law and Policy’ program has been developed by three professors from Penn State University. Areas covered in the syllabus include, cyber governance, domestic cyber law, and cyber operations.
Poor passwords
First there was ‘Plain Text Offenders’, and now we have ‘Dumb Password Rules’, as one apparently disgruntled netizen has taken it upon themselves to curate a list of company websites that take a… shall we say ‘idiosyncratic’ approach to password policy.
The Dumb Password Rules GitHub repo was created last year, but caught our attention this week after it appeared on the front page of Y Combinator’s The Hacker News.
More than 80 companies have been named and shamed for their slapdash approach to password policy.
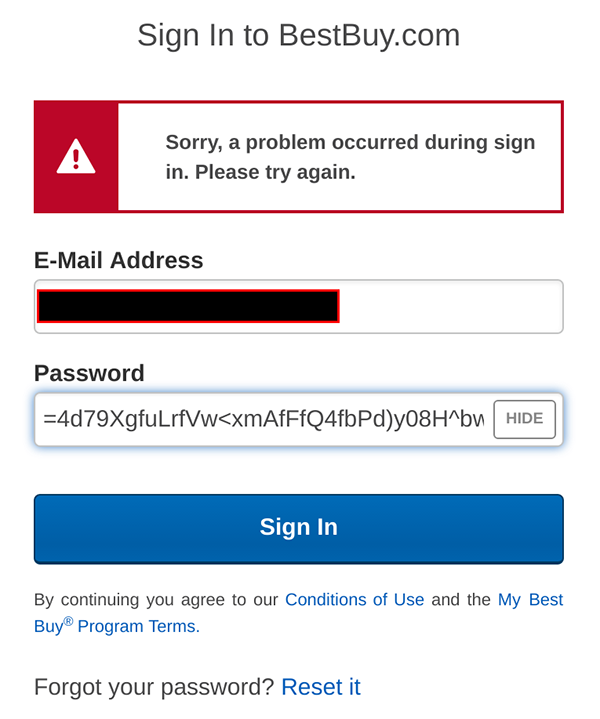
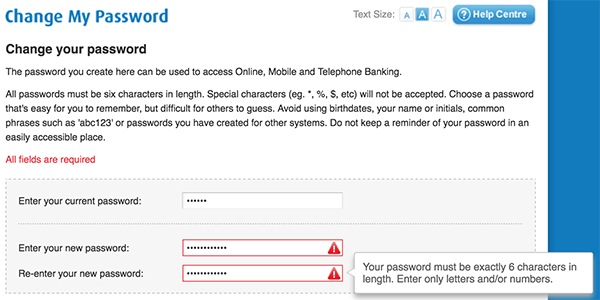
You’ll have to take a look through the list and decide for yourself which company takes the poor password prize, although BMO Bank of Montreal certainly seems to be a strong (or should that be ‘weak’) contender, as a screenshot indicates users’ passwords must be exactly six characters long and include no special characters…
… that’s not even enough letters to spell ‘B-R-U-T-E F-O-R-C-E’.