In the second episode of SwigCast, we talk all things encryption with guest Bruce Schneier

Click play to listen now. Also available on SoundCloud and all major podcast platforms
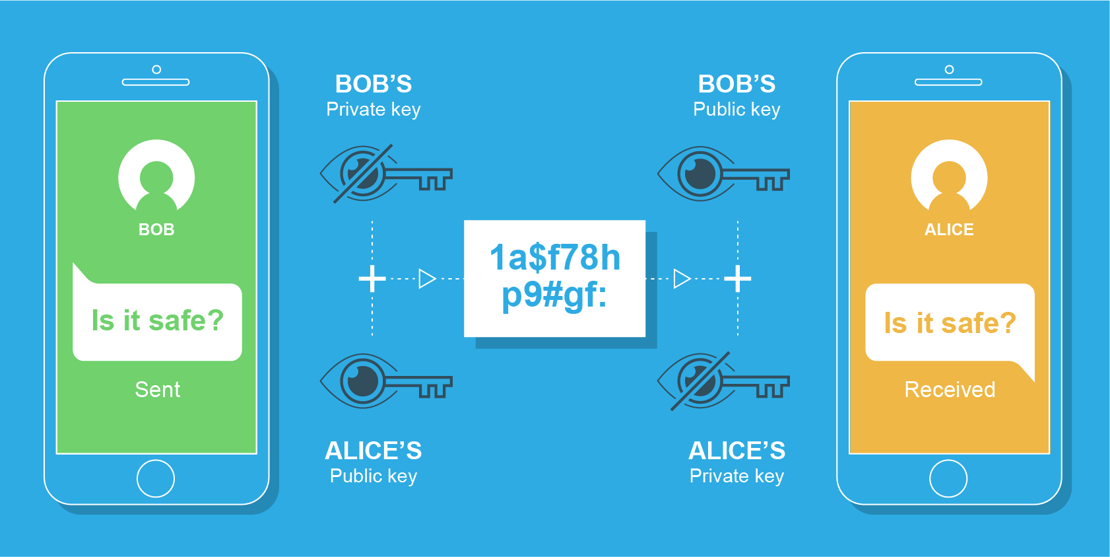
Encryption underpins the security of everything from digital purchases to private chats, and is a technology that has existed in one form or another for as long as human beings have shared secrets.
Having initially started out as a means for rulers and armies to pass on confidential messages, the technology has evolved into an everyday necessity to protect the credit card details of online shoppers and conversations of smartphone users.
But even though its daily presence has made encryption a topic that’s rarely out of the news, an ongoing conflict between law enforcement and techies has left the general public with little understanding of its actual importance.
In the second episode of SwigCast, we explore both the practicalities and the politics of encryption with the cryptographer and author, Bruce Schneier.
Schneier argues strongly against attempts by governments or others to weaken encryption, however well-intentioned they may be.
“Whether you weaken the encryption algorithm or the key management system or the update system, it doesn’t matter,” Schneier said.
“Once you weaken the system, you are less secure.”
Governments, whether in Australia, India, or the UK, typically argue that we can have secure messaging and still allow them to eavesdrop at the same time, but Schneier says this concept is simply not possible.
“Either everyone gets to spy or nobody gets to spy,” he said. “And once you accept that, then you decide, do you want everybody or nobody?”
Schneier added: “To me, it’s kind of obvious that security is much more important than surveillance, but maybe that’s not true.”
RELATED Electronic Frontier Foundation Surveillance Self-Defense Guide
The noted author has been making the same argument for more than 30 years, he explained, since around the time the US government put forward the quickly discredited Clipper Chip proposal, subsequently withdrawn from public discussion.
“We’ve been doing this since the mid-90s, but it hasn’t changed,” Schneier said. “The actors have changed [but] the argument never changes.”
Despite weariness over policy discussions that appear stuck in a regurgitated rut, Schneier expressed some optimism for the future.
“Eventually it will be obvious that our infrastructure is so heavily dependent on internet communications that securing it is paramount,” he said.
“And [that] any near-term needs of the police are just secondary to the value of securing our infrastructure. But we’re not there yet, so we’re still having these arguments.”
Post-quantum
Research into post-quantum encryption is a hot topic in security circles, but Schneier reckons we’ve already developed the technology we need, speaking in practical terms.
The main priority is to implement encryption on a wider scale rather than worry about the theoretical threat posed by quantum computers, he said.
“We don’t have a problem that quantum encryption needs to solve,” Schneier said.
“Our math problems are well-solved. We don’t need better math. We’re worried about things like keys escrow, backdoors, software security, users, hardware, we’re worried about supply chains – we’re not worried about the algorithms.”
He added: “Quantum encryption is kind of neat and we all like reading about it, but it’s not going to change anything because it actually doesn’t matter for anything.”
This episode also features public sentiment surrounding encryption, as we ask the Average Joe their thoughts on the debate.
SwigCast is a regular podcast that puts a variety of infosec topics under the microscope. Catch up and listen to the first episode






