Facebook Messenger users are being duped into downloading spyware disguised as Kik Messenger app

Honey trap spyware that can steal phone users’ data, track their location, and listen to their conversations is targeting Facebook Messenger users, Avast has warned.
Scammers are using Facebook to trick users into downloading malware disguised as the Kik Messenger app and orchestrating an advanced persistent threat (APT) to access their data.
The scam sees attractive women contact users, often young men, and strike up conversation before encouraging them to download Kik so that they can enjoy an “intimate” chat.
But the link is actually malicious spyware disguised as the app download, which then steals messages, contact details, photos, and other data from the victim’s phone.
Undressed
The scam was uncovered by Avast Threat Labs after a customer reported that they had been targeted.
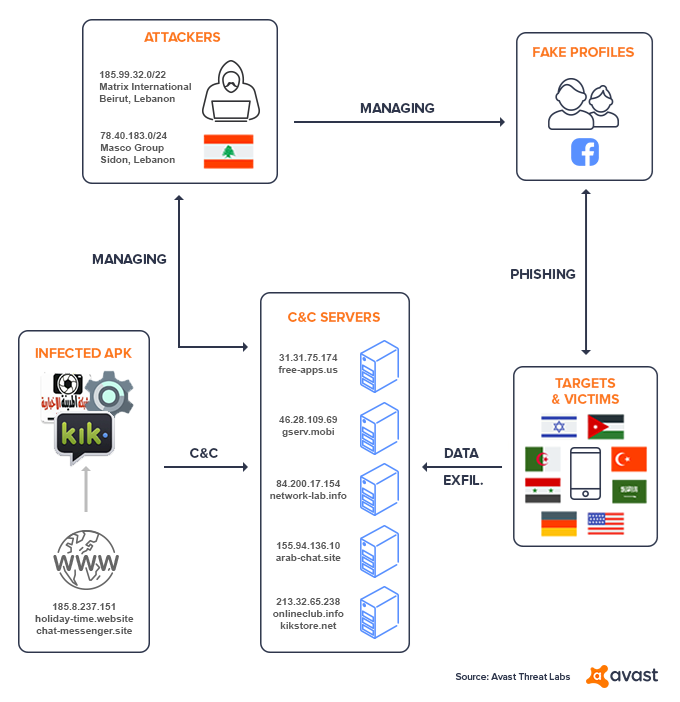
Avast researchers investigated the APT – which they named ‘Tempting Cedar Spyware’ – and found that it likely originated in Lebanon and has been running since 2015.
Worryingly, the malware can also record noise and conversations within the handset’s surrounding area and can access the victim’s geolocation, allowing the hackers to live track their phones.
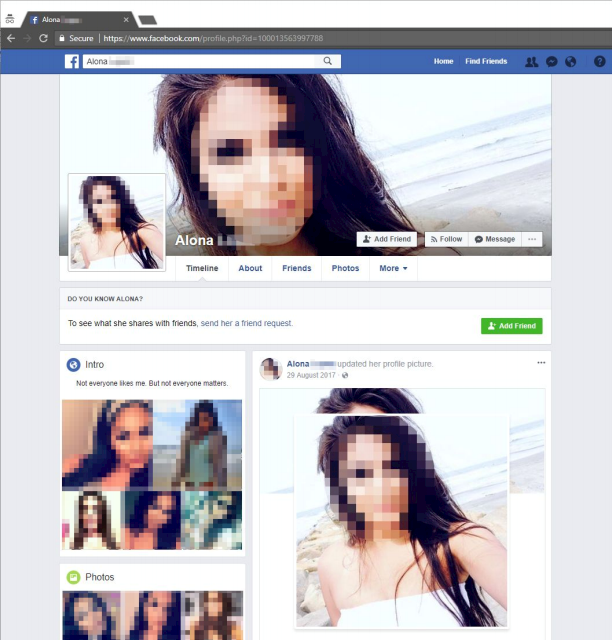
In a report released today, Avast noted that the spyware was spread by at least three fake Facebook profiles, all of which used real women’s pictures to dupe their targets.
Researchers at the security firm said they had contacted the relevant law enforcement agencies in relation to their discovery.
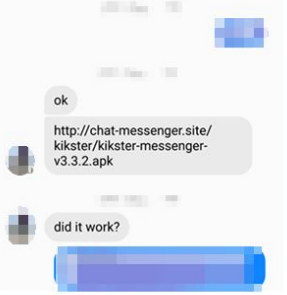
The report read: “The attackers sent a link to the victims that lead to a phishing website, which hosted a downloadable and malicious version of the Kik Messenger app.
“The victims had to adjust their device settings to install apps from unknown sources, before installing the fake messaging app.
“This should raise red flags for users, however, sometimes temptation trumps security.
“Once the malware was installed, it immediately connected to a command and control server.”
Avast is now one of only a handful of mobile antivirus providers blocking the threat.
Three of the fake Facebook profiles discovered by Avast – ‘Alona’, ‘Rita’ and ‘Christina’ – interacted with each other online, seemingly to make their profiles appear legitimate.
Many of the victims were based in the Middle East and Israel and a minority in Europe, including victims in the Czech Republic and Denmark.
Two IP addresses connected to the attack were based in Lebanon, Avast confirmed, adding that one of the Facebook profiles had ’liked’ pages linked to the Lebanese military.
Offering advice to social media users in the wake of the spyware discovery, an Avast spokesperson said: “Download from the source. Whenever possible, visit the homepage of an established company directly – by typing in the URL yourself – as they often promote their mobile apps on their websites and download the app straight from the source.
“Had the victims done this, they would have avoided the fake and malicious Kik app. The ‘girls‘ probably would have stopped talking to them, but that would have been for their own good!”






