Top infosec trends in the social media spotlight this week

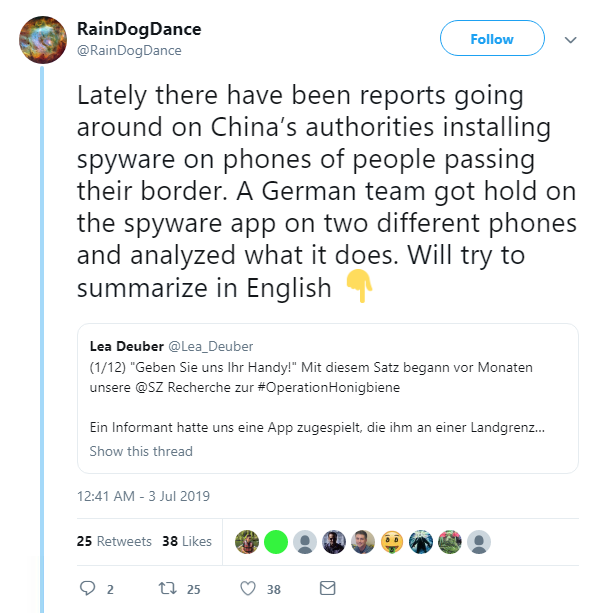
Explosive reports from China this week revealed that authorities are allegedly installing spyware onto tourists’ mobile devices.
Chinese border agents are accused of downloading the software onto Android phones belonging to travelers in the Xinjiang region, where the state is known to be conducting intense surveillance on the largely Muslim population.
The app, called BXAQ or Fēng cǎi, extracts data such as text messages, call logs, phone contacts, and usernames, then uploads it to a server.
Agents are also accused of demanding passcodes in order to go through the apps and other content on smartphones.
China is not the only country whose border guards are snooping on smartphones – a few weeks ago, war correspondent Seth Harp was stopped by guards while passing into Texas from Mexico, where they demanded access to his phone, too.
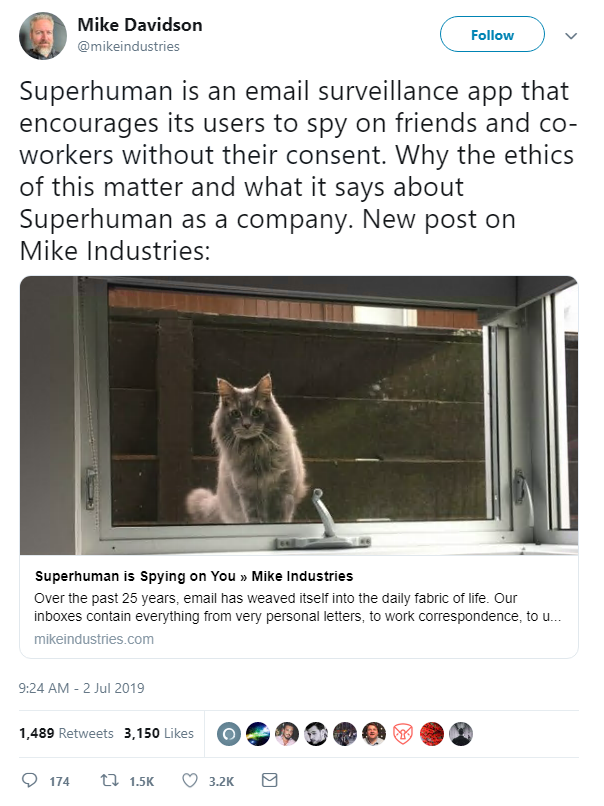
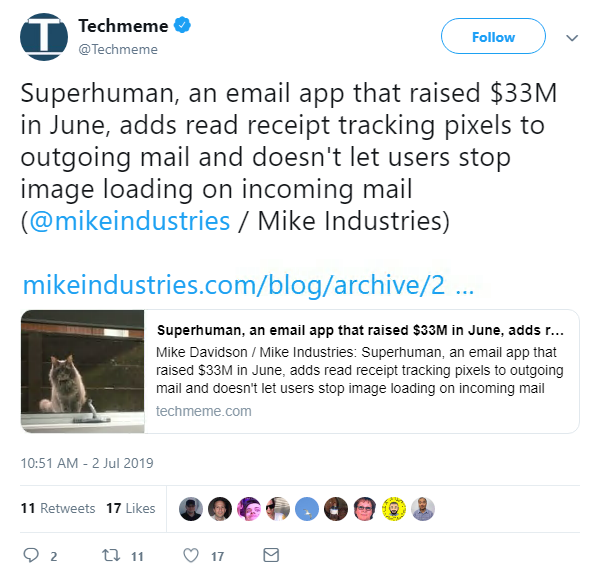
An email client heralded as tech’s trendiest new app was in hot water this week, after it was found to be tracking recipient’s real-time locations.
The Superhuman app, which costs $30 a month to subscribe, was praised as a hype-worthy startup just last week by publications including The New York Times.
Buzz surrounding the app, however, was quickly diminished this week after it was revealed to be using tracking pixels in outgoing emails.
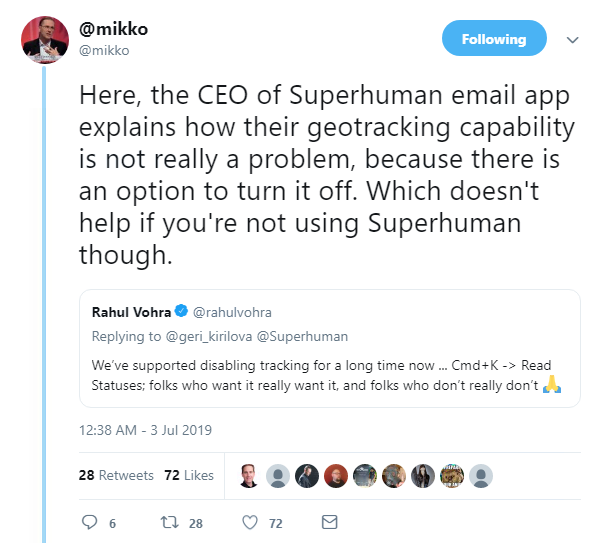
This allowed users to see when a recipient opened mail, when they viewed images, and where recipients were when they opened emails.
Obviously, this was a huge red flag for the security-conscious among the tech community.
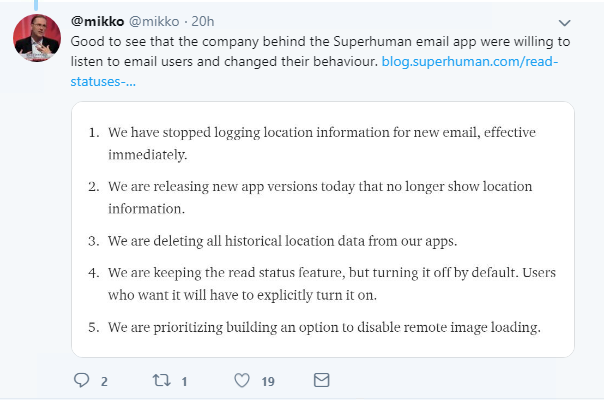
Superhuman CEO Rahul Vohra responded quickly by disabling location logging, deleting historical data, and turning off the read status feature by default.
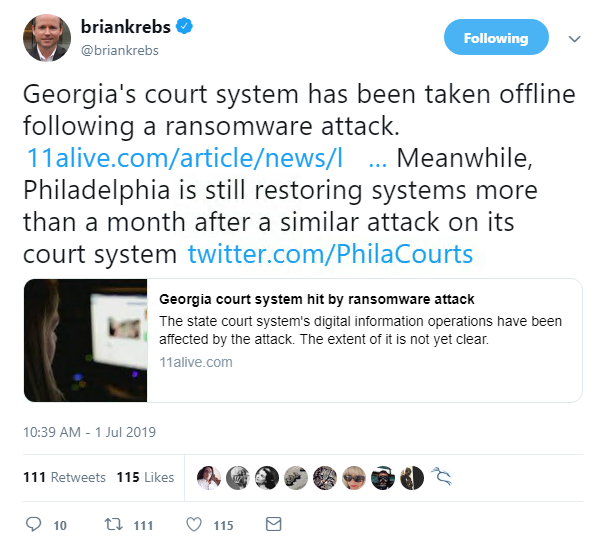
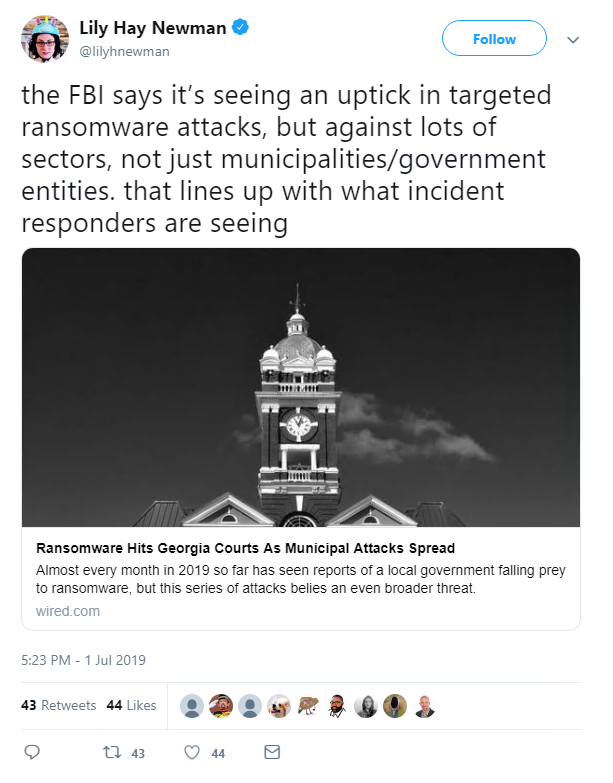
Another week, another ransomware attack – this time, the US state of Georgia’s court systems.
Georgia’s Judicial Council and Administrative Office of the Courts became the latest victim of what’s believed to be Ryuk ransomware this week.
Interestingly, contact details for the ransomware slingers were discovered on systems, but no specific ransom was demanded.
This was just the latest attack in a host of ransomware campaigns targeting various US government systems.
Notably, the city of Atlanta, Georgia, was hit by a huge ransomware attack last year which crippled systems and could cost up to $17 million to recover from.
It’s worth pointing out, though, that it’s not just governments that are being targeted, but every industry across the US, as Wired’s Lily Hay Newman reports.
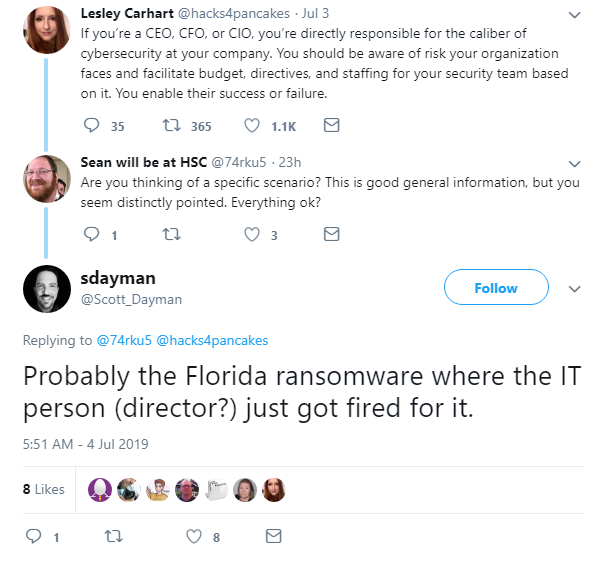
In other ransomware news, Lake City, Florida, fired its IT director after he paid a $460,000 ransom to attackers last month.
The city suffered a ransomware attack on June 10, disrupting email services and landline phones.
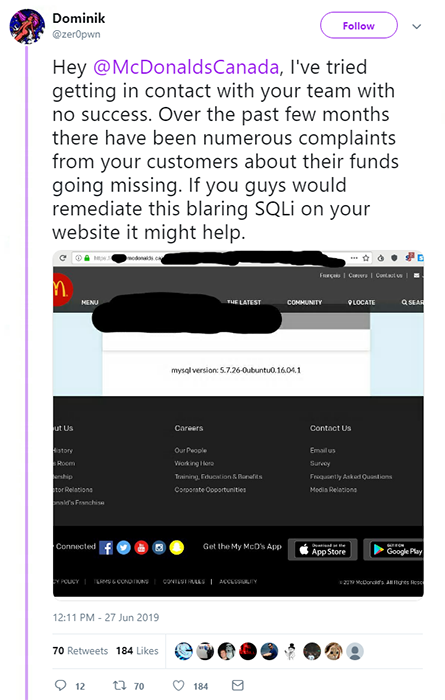
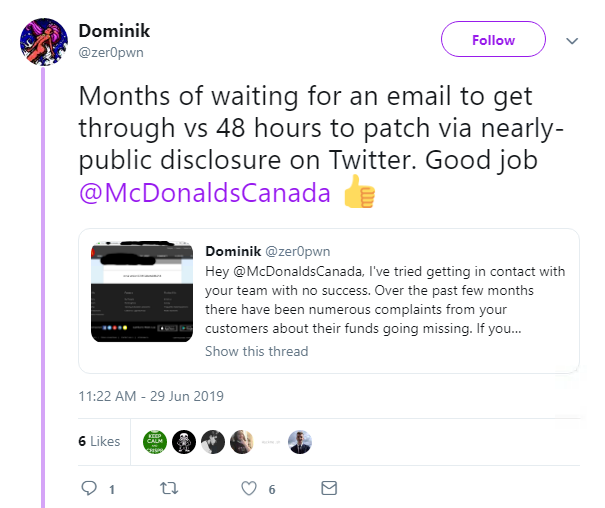
Finally, a researcher who exposed a gaping hole in McDonald’s Canada’s website was brushed off by the fast food franchise online, after it insinuated that recent security incidents were users’ fault.
@zer0pwn, aka 21-year-old white hat Dominik from Canada, tried to alert the company to an SQL Injection vulnerability on its website via Twitter after claiming he had hit a brick wall in attempts to contact the fast food chain directly.
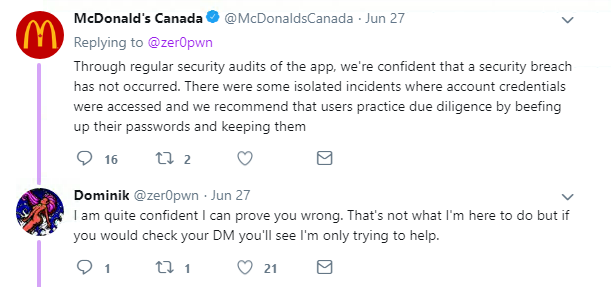
But he was told by McDonald’s that recent reports of customer funds disappearing were users’ fault.
Dominik tweeted that the issue was patched within 48 hours, but only after months of trying to disclose it privately.