Cryptographer Bruce Schneier on the practicalities of encryption
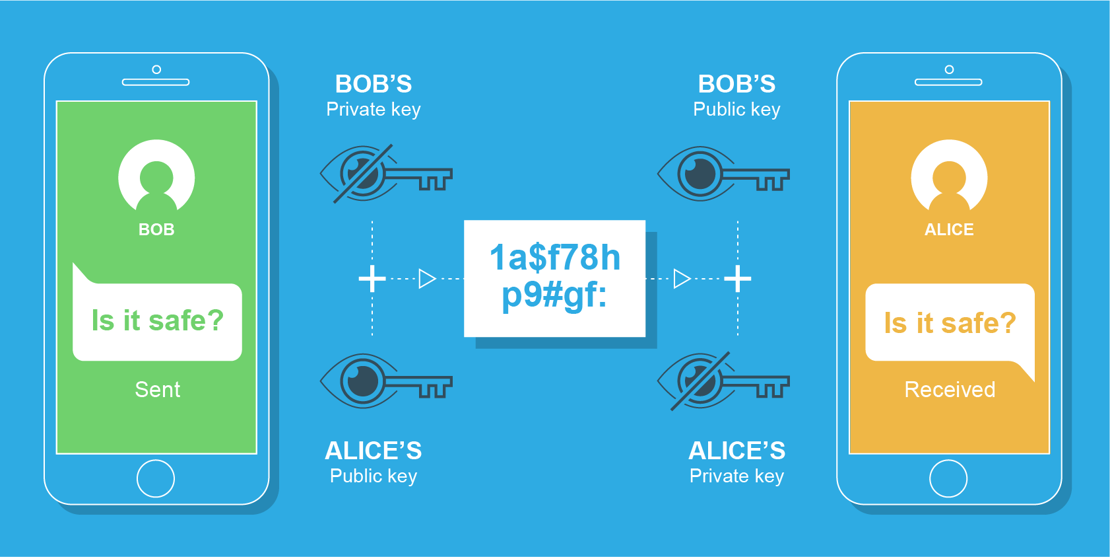
End-to-end encryption – the technology that underpins the privacy offered by mobile messaging apps – has become a point of contention between governments and tech firms.
Australia has already acted by enforcing its anti-encryption legislation, while the Trump administration is now considering banning the technology, arguing that it impedes investigations related to terrorism and other serious crimes.
Computer scientists and cryptographers counter-argue that weakening encryption through backdoors, or other means, is unworkable.
The Daily Swig spoke with famed cryptographer and author Bruce Schneier for the latest episode of SwigCast, as we attempted to dig deeper into the hotly-contested topic.
If you missed Episode 2, click play to listen now. Also available on SoundCloud and all major podcast platforms
So, Bruce, we’re speaking on Skype right now – is this a secure channel to be having this conversation?
Bruce Schneier: Well, we’re doing an interview that is going to be published so that everybody can listen to it, so none of us care if this is private, right?
If we were plotting to overthrow a government, maybe we would make a different choice, but I don’t know, I’m not worried.
Do you think that consumers are aware of the choices there are when it comes to secure communication?
Schneier: I don’t think so. I think consumers and users, in general, use what’s easy and convenient. I don’t think that they think much about phones or texting, and whether they are private or not.
I think that if you’re in a country where that [privacy] matters, you think about it more, but in general, no, I don’t think that people worry about it [secure communication] very much.
Off the back of that answer, Bruce, I wonder if you can explain to our listeners what end-to-end (E2E) encryption is, and shed some light on the technologies behind it.
Schneier: So E2E, basically, means encryption from your device, to the device of the person you’re talking to.
So, for example, if I am using Signal, which is a secure messaging app, the message is encrypted on my phone, sent through the network to the person that I’m talking to, and decrypted on their phone. That’s E2E.
This is different from when, let’s say, I send a Gmail. I’m likely using an encrypted link between my browser and Google, where that message is unencrypted, and then Google probably uses an encrypted link to, I’m going to make this up, Apple Mail, because the recipient is on Apple Mail, and then that message is decrypted. And then the recipient, when he logs in to his email account, that message will be encrypted again.
So that’s encrypted, but [it’s] not E2E.
Now the difference is, for E2E encryption, nobody except the sender and recipient can read the message. It’s encrypted all the way through.
Is that the benefit of having end-to-end encryption?
Schneier: Right, the benefit of E2E is that nobody can read it. And whether it is your government, a rival government, a cybercriminal, or anybody, it cannot be intercepted in transit.
So when you have your lawmakers talking to each other, you want E2E encryption. Nuclear power plant operators want E2E encryption. E2E encryption is how we get security, and when you think of all the important things happening, all the communications, you really want it because it’s important.
If you want Google to basically eliminate spam from your email, it can’t be E2E. Otherwise Google can’t detect the spam. So, yes, there are a lot of trade-offs to E2E [because] primarily, we like other people in the middle of our systems to do work.
We’ve heard a lot from governments about this trade-off, and have slowly seen legislation get passed that seeks to provide backdoor access to secure communication, including Australia’s Assistance and Access Act and GCHQ’s ghost feature proposal. Are we reaching some kind of breaking point in how we create ‘secure’ systems?
Schneier: Yeah, so there are [government] proposals. There are different ways to weaken encryption, and in a sense they don’t matter because how you do it is less important than whether you do it.
Once you weaken cryptography, and whether you weaken the encryption algorithm or the key management system or the update system, it doesn’t matter. Once you weaken the system, you are less secure.
Now the argument from governments is that we don’t care about this [decreased] security because we think it’s important to eavesdrop on the bad guys.
Now that’s an argument that you can make, it’s a kind of argument that doesn’t really hold much water, but that’s it. And you need to make that argument. Governments more likely are making the argument that we can get both – we can get security and we can get eavesdropping.
We can decide as a society that we want less security because eavesdropping on the bad guys is more important.
So we don’t care that the Russians are eavesdropping on our election system; we don’t care if the mob is eavesdropping on the police; we don’t care that foreign governments are eavesdropping on our government officials; we don’t care about our nuclear power plant security. We don’t care about any of that.
All we care about is being able to listen to the bad guys, and what you tend to see more of is ignoring the trade-offs – like, we want to listen to the bad guys full stop, and we’re not going to even think of anything else.
To me, it’s kind of obvious that security is much more important than surveillance, but maybe that’s not true. But it’s either everybody gets a spy, or nobody gets a spy.
SwigCast is a regular podcast that puts a variety of infosec topics under the microscope. Catch up and listen to the first episode
Are you tired of having this conversation about encryption policy?
Schneier: We’ve been doing this since the mid-90s and it hasn’t changed. The actors have changed [but] the argument never changes. Eventually, I think we’ll figure it out.
Eventually, it will be obvious that our infrastructure is so heavily dependent on internet communications that securing it is paramount – and any near-term needs of the police are just secondary to the value of securing our infrastructure. But we’re not there yet, so we’re still having these arguments.
How have we seen things move on from email secured using PGP as the ‘gold standard’ for secure messaging?
Schneier: What we’ve learned from 20 years of trying to implement PGP and email encryption, in general, is that it’s really, really hard to encrypt email. And now when I tell people if they want to have a secure conversation to use an encrypted messaging program – to use Signal, to use WhatsApp – that they are easier to secure and are more reliable, that’s really where we’ve gone. We’ve kind of gone past email encryption and now we’re on securing chat applications.
What about wider technology innovations like 5G – how will this impact encryption and security overall?
Schneier: The importance of 5G, which is the next generation of cell phone protocol, is not so you can watch faster movies or chat with your friends. The importance of 5G is that it makes computer to computer communications easier, and as we move to IoT we’re going to have more instances where computers are talking to computers directly without us.
So, it’s not my phone talking to your phone, but the thermostat talking to the power grid, my car talking to some other car – so things talking to things. And that’s going to be huge, both in promised capability but it’s also a huge security risk, and I don’t think we’re really having a good conversation about 5G security. Encryption is a part of that, but it’s a small part of it, there’s a lot more to 5G security than encryption.
And quantum computing? Are we entering a new phase of encryption here?
Schneier: Quantum encryption is largely irrelevant to security. Nobody in cryptography cares. We don’t have a problem that quantum encryption needs to solve.
Our math problems are well solved. We don’t need better math. We’re worried about things like key escrow, backdoors, software security, users, hardware – we’re worried about supply chains, we’re not worried about the algorithms.
Quantum encryption is kind of neat, and we all like reading about it, but it’s not going to change anything because it actually doesn’t [mean] anything.
What are some of the challenges of implementing E2E encryption and secure messaging everywhere?
Schneier: There’s really no business requirement for a lot of security, most of them [businesses] aren’t secure because the market doesn’t reward security. The market doesn’t demand that systems be secure.
The market at consumer-level may not reward good security, but how about the capabilities of law enforcement and intelligence agencies? Is there more going on here in terms of decryption capabilities, for instance?
Schneier: There’s a lot going on in terms of government capabilities.
You read in the Mueller Report of encrypted messages that were decrypted. My guess is that they got them from the providers, that, in fact, if you have an encrypted chat, and you store a copy of it with Apple or Google, then it is available. There’s a lot to do in traffic analysis. Who people are talking to is incredibly valuable. The encryption debate has gotten more nuanced.
It seems like the NSA is more on the side of security than surveillance because they realize that there are other ways into systems that encryption can’t prevent. I’d like to see the FBI get more sophisticated in how they do forensics and how they do investigations because they don’t need to basically make everybody insecure just to have capabilities, there are other ways they can get at it.
So, yes, I think we are seeing more nuanced debates today but still I think law enforcement still has a long way to go before they are comfortable with the security that society needs.
Right, so there’s plenty to consider. From a practical point of view, if any of our listeners wants some advice on how they can become more secure, where do you recommend that they go to get more information?
Schneier: There are several guides on the internet that talk about digital privacy and helping make choices. EFF [Electronic Frontier Foundation] has one, there’s one from Citizen Lab, there are several others.
Find those, read those, and make decisions carefully. This is not something that you ask for random advice at a cocktail party. So be careful of that.
RELATED ‘Are we building surveillance into systems, or are we building in security?’






