Vulnerability in IP-masking browser revealed on social media

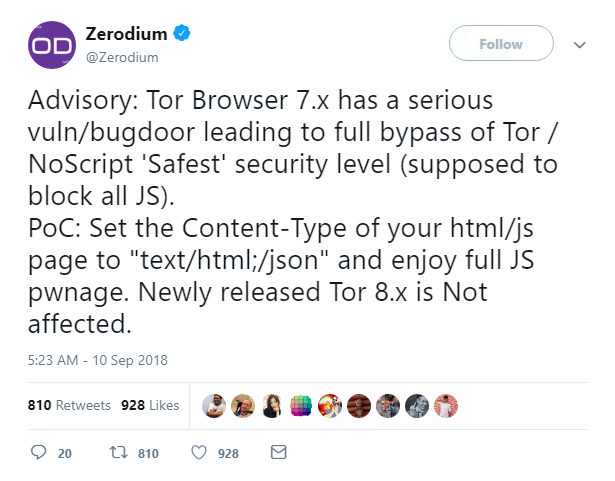
A zero-day vulnerability which bypassed a script-blocking add-on in the Tor browser to inject malicious code was revealed on Twitter yesterday.
It was first announced by Zerodium, when the vendor posted details of the bug on its Twitter page.
The vulnerability existed in the Firefox extension NoScript, which blocks web pages from executing JavaScript, Java, Flash, or Silverlight.
It allowed an attacker to suppress NoScript – which is built in to the Tor browser but not enabled by default – and give JavaScript permission to run on the page.
The bug even worked when a user selected NoScript’s highest safety option, but was only able to be exploited in Tor Browser 7.x.
Users are once again urged to update to the latest version, Tor Browser 8, and if not, to at least install NoScript 5.1.8.7, which was rewritten within two hours of the exploit going public.
Zerodium is known to have offered up to $1 million for exploits in the Tor browser and knew about the flaw for “many months”.
It also confirmed that the vulnerability was shared with its “government customers” – a worrying prospect for Tor’s privacy-conscious users.
The author of the NoScript extension, Giorgio Maone, however, told ZDNet that he only knew about the bug after it had been posted online.
Maone also ‘thanked’ Zerodium in his release notes for its “unresponsible disclosure”.
This latest release has also led some to question whether the vendor also has details on a vulnerability in Tor Browser 8.