Modular malware now demanding more than $1,200 for decryption

Hackers behind the Anatova ransomware strain have released a new version of the malware that demands twice as much to unlock files as they demanded only last month.
Anatova hit the security headlines two weeks ago, when McAfee analyst Alexandre Mundo came forward with details of a new ransomware strain that was being distributed via a private peer-to-peer (p2p) network.
According to the McAfee threat report, Anatova uses the icon of a game or application to try and dupe prospective marks into downloading it.
Once installed, the ransomware encrypts all the files on a victim’s computer before demanding 10 DASH coins – currently valued at around $660 – for the data to be decrypted.
Following the publication of McAfee’s warning about Anatova, many within the security community said the p2p infection method served to highlight the risks associated with downloading pirated games or software.
Of equal importance, however, was the discovery that the ransomware comes with support for additional modules that could extend its functionality.
“The developers/actors behind Anatova are, according our assessment, skilled malware authors,” said Mundo. “We believe that Anatova can become a serious threat since the code is prepared for modular extension.”
Anatova’s modular architecture means that new functionalities can easily be added – a factor that makes it potentially even more dangerous than other ransomware strains.
Christiaan Beek, lead scientist and principal engineer at McAfee, commented: “Anatova has the potential to become very dangerous with its modular architecture which means that new functionalities can easily be added.
“The malware is written by experienced authors that have embedded enough functionalities to be sure that typical methods to overcome ransomware will be ineffective, for instance data can’t be restored without payment and a generic decryption-tool cannot be created.”
Double fault
With less than 350 confirmed global infections, Anatova has a long was to go before it reaches GandCrab-level notoriety. And when it comes to the ransomware’s modular functionality, security researchers can only speculate about the developer’s future intentions due to a lack of hard evidence.
Despite this mystery, it appears that this malware is still in active development, as Malwarebytes researchers last week informed The Daily Swig that they have been tracking a new version – a variant which demands double the original ransom fee.
“We have been tracking the development of Anatova ransomware since it appeared on the scene earlier this year, and we have already [discovered] a second version of this modular ransomware, which now asks for 20 DASH instead of 10 DASH as it did [with] the first version reported by McAfee,” said Marcelo Rivero, malware intelligence analyst at Malwarebytes.
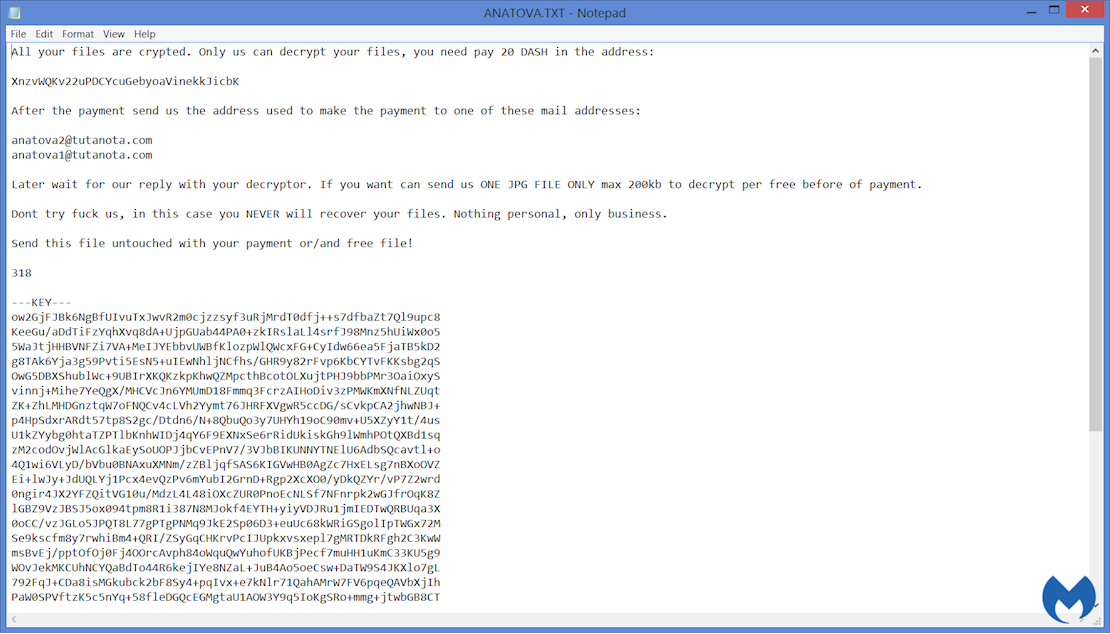
A screenshot of a new Anatova ransom note, as discovered by Malwarebytes, demanding 20 DASH payment
Advantage: Anatova
After draining an estimated $5 billion from the global economy in 2017, ransomware continues to be listed among the biggest malware threats facing consumers and businesses today.
Although it remains to be seen whether Anatova will ascend to the ranks of other more lucrative and prolific ransomware families, Liviu Arsene, senior cybersecurity researcher at Bitdefender, said this could change if major distribution campaigns start using it as a payload.
“Every well-written piece of ransomware has the potential to become a nuisance, and judging by the way Anatova was built, it’s entirely possible that it’s not the last we’ve heard of it,” Arsene told The Daily Swig.
“The fact that it’s modular and may support additional modules suggests that it could be under development. Ransomware-as-a-Service is a highly lucrative business model and perhaps Anatova is built to support additional features based on client demands.”
John Fokker, head of cyber investigations at McAfee, added: “We won’t be surprised if Anatova, because of its modular structure, will come packed with other malware add-ons. This synergistic approach can become a challenge to defend.”






