Top infosec trends in the social media spotlight this week.

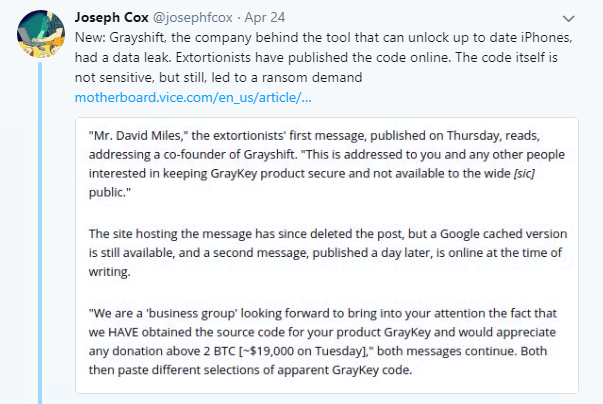
The company that promises to hack any iPhone passcode was embarrassed this week when it was hacked itself.
Grayshift, which manufactures the GrayKey box, was compromised by unknown attackers who leaked data from a unit’s UI.
They demanded two bitcoin (around $18,500 at the time of writing) under the threat of more leaks.
But Grayshift claimed no sensitive data was accessed, and apparently refused to pay the ransom.
The company said in a statement: “Due [to] a network misconfiguration at a customer site, a GrayKey unit’s UI was exposed to the internet for a brief period of time earlier this month.”
“During this time, someone accessed the HTML/Javascript that makes up our UI. No sensitive IP or data was exposed, as the GrayKey was being validation tested at the time.”
As you may know, the GrayKey box is popular with law enforcement agencies, given it can crack iPhone access within days, if not hours.
Grayshift later said “changes” have been made to the security of the boxes, and reassured customers their devices were secure.
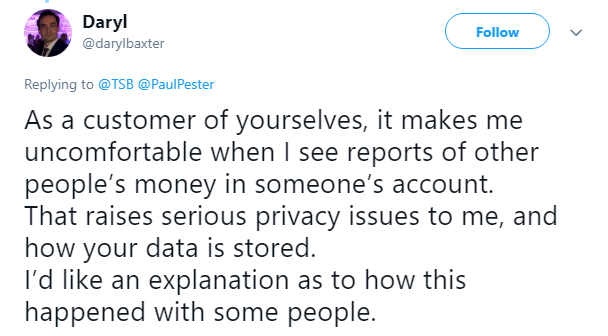
In the UK, TSB customers were also concerned this week after an apparent data breach at the bank.System outages prevented account holders from accessing their funds – and in some cases, presented them with the data of other customers.One man claimed he was able to view a business account with £2.8 million in funds, while another said he had access to someone else’s £35,000 savings.
TSB has so far dodged claims of a data breach and hasn’t confirmed whether personal information was leaked or shared.
But the bank – which was owned by Lloyds until 2013 – is now being investigated by the Financial Conduct Authority and the Information Commissioner’s Office.
If found to have suffered a leak, it could face a huge fine.
The alleged breach happened during a switch over from Lloyds IT systems to the new TSB networks.
A TSB spokesman claimed the incident “lasted only about 20 minutes and impacted just a tiny fraction of our customer base”.
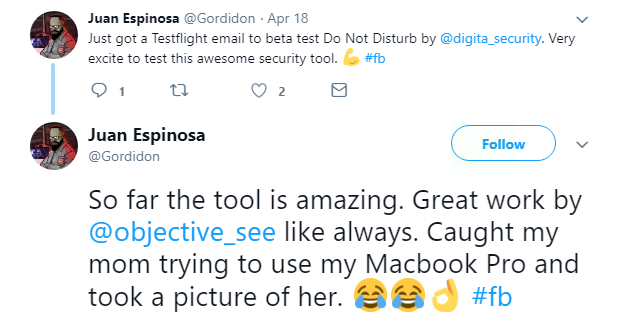
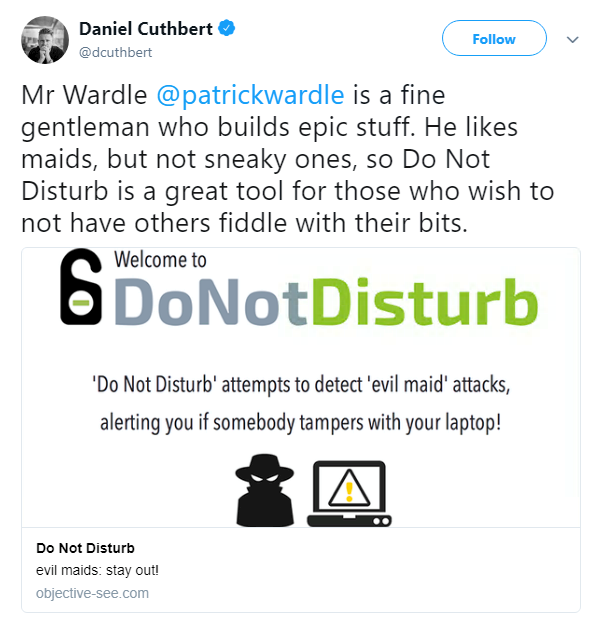
In product news, security-minded folk can now leave their devices unattended with a little more confidence, following the development of a new tool that protects against ‘evil maid’ attacks.The Do Not Disturb (DND) app logs when an unattended laptop lid is opened, and takes a picture of the possible attacker, to help identify when a device has been tampered with.Evil maid attacks are so-called because they are the result of a physical compromise, such as an unauthorized person breaking into a hotel room and downloading malware onto a device.
When the laptop lid is opened, DND can also send an alert to the owner on another device, execute an action, for example running script, and logs actions.
It was the brainchild of ex-NSA staffer Patrick Wardle, who thought of the app when he became paranoid about leaving his laptop during a Tinder date in Moscow.
And it has proved a hit with the infosec community, too:
They may not have been crowned Masters of Pwn, but two researchers from MWR Labs have release details on the Huawei Mate9 Pro hack unveiled at Mobile Pwn2Own last year.Alex Plaskett and James Loureiro finally revealed their technique this week after successfully executing code on the browser of the mobile device back in November 2017.
They received $25,000 and 10 Master of Pwn points for the hack, which they have detailed in a new document.
The team posted the write-up online after the Chinese company patched the bugs:
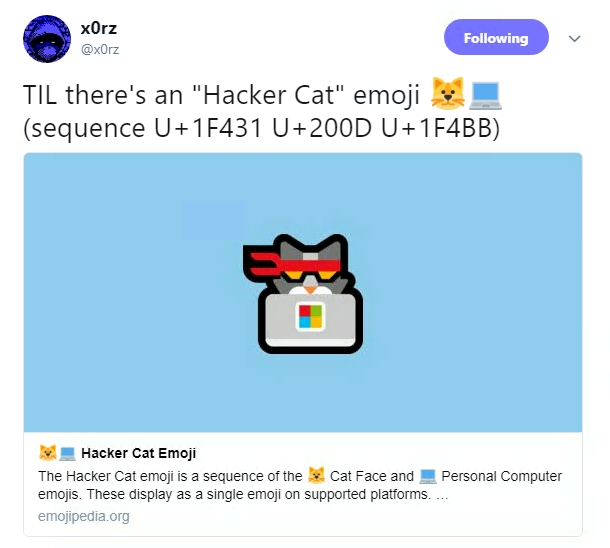
And finally, infosec banter collided with one of the internet’s greatest loves when the hacker cat emoji surfaced on Twitter.
The symbol – a cat sat at a Windows laptop with a red tie around his head – is available to lucky Microsoft users with a penchant for our feline friends.
It isn’t a new addition and has been around for a while, but the emoji erupted this week when it was posted online.
Non-Windows users, though, were quite rightly jealous of the emoji, since there’s no current plan for it to be rolled out across other operating systems.