Stop cybercriminals from gobbling up your payment card details

Arguably one of the biggest days in US retailers’ calendars, tomorrow’s Black Friday celebrations will see millions of shoppers eyeing up deals online.
The recent tradition, which began in the US, has since spread to countries worldwide, with many traders in Europe and South America taking part.
But as companies slash prices, the risk of being stung by cybercrime increases – especially at a time when internet shopping fraud is at a high.
In 2017, victims reportedly lost a staggering £16 million during the festive period, up 45% from the year before.
According to a report by ACI Worldwide, this holiday season will see a 14% increase in attempted fraud – with the highest number of instances so far reported for Black Friday and Cyber Monday.
It’s easy to see why, as online shoppers routinely ignoring red flags to get their hands on a bargain during the retail frenzy.
Rusty Carter, vice president of product technologies at Arxan Technologies, told The Daily Swig: “It goes without saying that amongst the excitement of a bargain, cybersecurity is not top of mind for consumers, however, it is this type of distraction that opens shoppers up to multiple risks.
“With many of our high street shops closing down, it is clear that online and mobile shopping is continuing to gain momentum.
“However, the new opportunities associated with the growing range of m-commerce services also entails new risks: business transactions via web and mobile applications – be it payment transactions or the transmission of sensitive personal data – are particularly threatened by cyber manipulations and open up a range of possibilities for fraud and data theft.”
Swapping turkey for trojans
Researchers at Kaspersky have warned that banking trojans are targeting popular e-commerce programs this holiday season with the intent of stealing sensitive data and building botnets for future attacks.
A study released this month discovered that at least 14 malware families are poised to attack online banking users and internet shoppers.
The report reads: “The main ones are Betabot, Panda, Gozi, Zeus, Chthonic, TinyNuke, Gootkit2, IcedID and SpyEye. They are all banking trojans.
“Detections of their e-commerce-related activity has increased steadily over the last few years, from 6.6 million in 2015 to an estimated 12.3 million by the end of 2018 (based on the extrapolation of a detection number of 9.2 million at the end of Q3, 2018), with a 12% increase between 2016 and 2017, and a 10% expected rise between 2017 and 2018.”
When a device is infected, cybercriminals can steal login details, card numbers, and passwords, as well as inject malicious code, record video, and obtain root access to the machine.
The malware can be used to track a user and identify when they are entering information into forms on a website – known as ‘form-grabbing’ – where they can access expiration dates and CVV numbers.
Researchers claim these malware families are targeting at least 67 popular consumer e-commerce websites, including clothing stores, electronics websites, and gaming sites.
David Emm, principal security researcher at Kasperksy Lab, told The Daily Swig: “As our report makes clear, we see plenty of malware designed to steal from individuals indiscriminately – banking trojans, for example.
“However, the benefit of targeting e-commerce sites is that cybercriminals can obtain lots of data through one attack. The difficulty and gains are typically in inverse proportion, for example, attacks on e-commerce sites are harder to launch, but offer bigger rewards for attackers.”
He added: “We only have statistics for the first three quarters of 2018, so we’re not able to compare the years properly. However, it seems likely that the data will show an increase.
“In 2017, Kaspersky Lab technologies detected 11.2 million attacks; we have detected 9.2 million attacks in only the first three quarters of this year. It’s on track to be a bigger number than 2017.”
Consumers are also at risk of hackers injecting card-skimming script into popular websites.
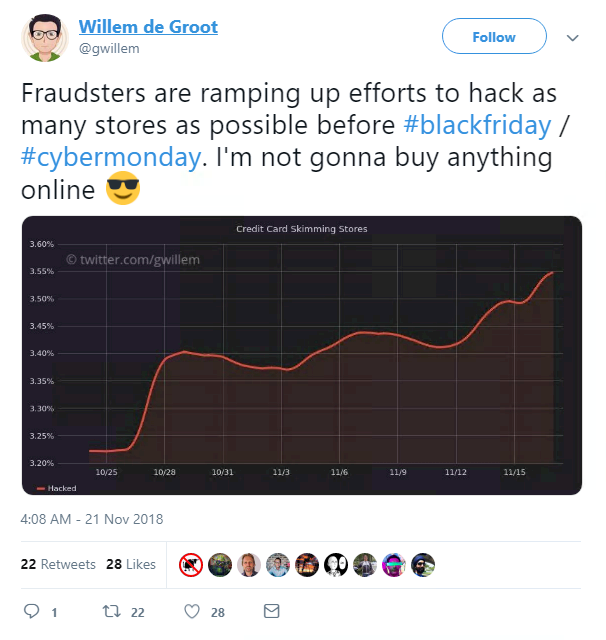
Willem de Groot, security researcher and malware hunter, has been tracking hackers using the Magecart technique since 2015, which exploits the payment system Magento to steal card details and personal information.
Magecart has so far been blamed for more than 6,400 attacks on websites using Magento including Ticketmaster and British Airways.
De Groot’s open source Magneto malware scanner this week showed a steep increase in the number of stores targeted by hackers.
Mobile offers and malicious apps
Consumers should also be on the lookout for simple tricks that hackers can use to pilfer details, such as fake mobile apps carrying malicious risks.
A report from cybersecurity firm RiskIQ, which studied more than 4,000 Black Friday-related apps available to download on mobile, found that 5.5% contained hidden content such as malware.
Each of the top 10 most-trafficked websites during Thanksgiving 2017, which were largely retail outlets, were imitated, on average, by 17 malicious apps.
Once downloaded onto a device, these apps can launch spyware to track a user, or skim their payment card details.
Shoppers are also urged to remain vigilant for SMS phishing, or ‘smishing’, campaigns.
As mobile shopping increases in popularity – last year, 40% of Black Friday sales were made using phones – more and more companies are choosing to communicate with customers via SMS.
In 2017, communications provider Infobip estimated that 40 million people in the UK alone received Black Friday offers via text message.
While email clients have increasingly sophisticated spam filters in place, mobile operating systems don’t offer this kind of protection, making text messaging platforms a prime target for scammers.
A whitepaper (PDF) by IT security company Lookout states that since 2011, instances of mobile phishing attacks have increased by 85% each year.
The paper also suggests that it’s easier to trick users into clicking phishing links in a text message, as researchers claim it’s more difficult to verify hyperlinks on mobile than it is on desktop.
But the threat of email phishing campaigns should not be ignored, and while email clients are increasingly better at blocking spam, they aren’t 100% foolproof.
In the days following Black Friday, it’s worth bearing in mind that cybercriminals will attempt to masquerade as legitimate vendors.
One campaign in the past has seen scammers pose as popular delivery companies, claiming that they need confirmation of payment. Others have posed as major Black Friday vendors, such as Amazon, claiming they need updated payment information.
Ignore any email that may look suspicious. If in doubt, contact the company directly.
Thanksgiving takeaways
Some researchers, such as de Groot, are choosing to boycott online shopping tomorrow.
But if the lure of an offer is too much to keep you away, there are a few things that shoppers can do to help protect themselves:
Firstly, and importantly, ensure your devices are always updated to prevent hackers from exploiting any known vulnerabilities.
Scrutinise any apps you might want to download – does it use the official logo? What data or controls does it ask permission for access to? Also, check user reviews.
Check the site is full HTTPS. Look for the padlock, if that’s easier.
Never enter your card or banking details when using open or insecure WiFi networks.
And finally, don’t open any suspicious-looking emails or click any links in text messages that weren’t sent by someone you trust. If a deal looks too good to be true, it probably is.






