Twist and shout
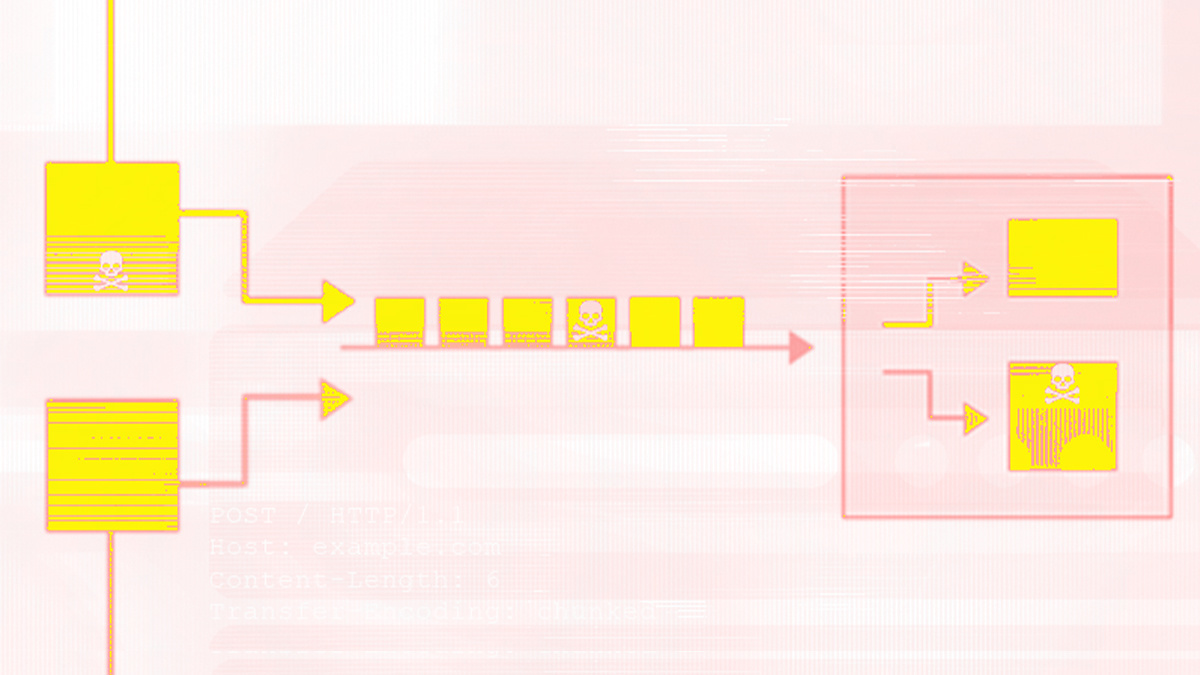
Security researchers have published details of two recently resolved HTTP request smuggling vulnerabilities in the Twisted programming framework.
HTTP request smuggling is a class of web security vulnerability that can lead to a variety of problems, including cache poisoning, session hijacking, and the circumvention of security filters.
Twisted is an event-driven networking engine written in Python and developed by Twisted Matrix Labs.
BACKGROUND HTTP request smuggling: Ancient technique tears a hole through modern web stacks
The causes of request smuggling can vary, but both vulnerabilities in Twisted involve improper input validation. Both bugs were discovered by Jake Miller, a security researcher at Bishop Fox.
The first vulnerability (CVE-2020-10108) meant that “when presented with two content-length headers, it [vulnerable versions of Twisted] ignored the first header,” an advisory posted on GitHub explains.
“When the second content-length value was set to zero, the request body was interpreted as a pipelined request.”
In the case of the second bug (CVE-2020-10109), the advisory explains how, when presented with a content-length and a chunked encoding header, the content-length “took precedence and the remainder of the request body was interpreted as a pipelined request”.
Patch release
Both vulnerabilities affect Twisted version 19.10.0, and each can be resolved by upgrading to version 20.3.0.
Miller discovered and reported the issues to Twisted last December before liaising with the team in developing patches, which were released in early March.
An advisory published by Bishop Fox offers more detail, alongside proof-of-concept code that shows how “smuggled requests were interpreted by the Twisted server”.
“The impact of these vulnerabilities can vary depending on the surrounding infrastructure and the purpose of the service implemented with Twisted,” Bishop Fox’s advisory states.
Miller told The Daily Swig that his work was inspired by research into HTTP request smuggling by web security pros James Kettle and @regilero.
“I started looking for these vulnerabilities in popular libraries and found one in the Python Twisted framework,” Miller explained.
Miller went on to offer general advice to web server or web framework developers on how to defend against and remediate HTTP request smuggling issues.
“These flaws often emerge from deviations of the original RFC 7230 HTTP 1.1 specification,” Miller explained.
“Although there can still be risks outside of the spec, many flaws I encounter are simply not following the message parsing procedures outlined in the original RFC.
He added: “Ensuring an RFC compliant server is a great first step to securing against these attacks.
“Devs should focus on implementing unit tests and can use James Kettle’s HTTP request Smuggler Burp extension or @regilero’s HTTPWookie for automating testing or getting inspiration for test cases,” he concluded.
READ MORE Web cache deception named top web hacking technique of 2019






