Hacker cites discontent with responsible disclosure

Details of an as-yet unpatched vulnerability in Oracle’s VirtualBox technology have been dropped online.
Rather than attempt to claim a bug bounty, the finder of the flaw dumped details of a vulnerability and an associated exploit on GitHub.
The researcher, who rejoices in the nom de guerre of MorteNoir1, cited discontent about the prevailing fashion of giving bugs their own names and overall disaffection with the responsible disclosure process in explaining their actions.
The vulnerability itself is an unpatched guest-to-host escape from VirtualBox, Oracle’s open-source hypervisor technology.
“I like VirtualBox and it has nothing to do with why I publish a zero-day vulnerability,” MorteNoir1 explains. “The reason is my disagreement with contemporary state of infosec, especially of security research and bug bounty [programs].”
VirtualBox 5.2.20 and prior are vulnerable but only in certain configurations.
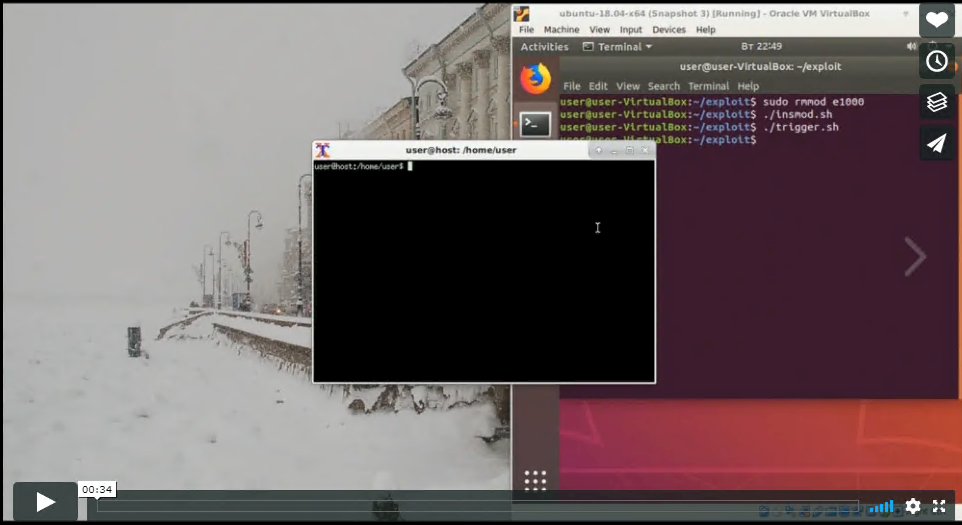
The vulnerability is only effective in set-ups where the network card is an Intel PRO/1000 MT Desktop (82540EM) and the mode is NAT, both default modes. Changing either the network card on a virtual machine or moving onto a Paravirtualized Network would guard against the attack.
“The E1000 has a vulnerability allowing an attacker with root/administrator privileges in a guest to escape to a host ring 3,” MorteNoir1 adds, “then the attacker can use existing techniques to escalate privileges to ring 0 via /dev/vboxdrv.”
A user – Sergey Zelenyuk – posted a video of the exploit in action via Vimeo:
The root cause of the problem is buffer overflow issues in VirtualBox’s networking code.
The researcher who discovered the flaw didn’t bother to report it to Oracle, possibly because the software giant reportedly took a full 15 months to fix a previous, similar issue.
The Daily Swig asked Team VirtualBox for comment on what its response might be via Twitter. We’ll update this story as and when we hear more.