‘If you report a security issue, at least update your Linux distribution’

Widespread reports of a ‘critical security issue’ that supposedly impacted users of VLC media player have been debunked as “completely bogus” by developers.
Earlier this week, German computer emergency response team CERT-Bund – part of the Federal Office for Information Security (BSI) – pushed out an advisory warning network administrators and other users of a high-impact vulnerability in VLC.
It seems that this advisory can be traced back to a ticket that was opened on VLC owner VideoLAN’s public bug tracker more than four weeks ago.
The alleged heap-based buffer overflow flaw was disclosed by a user named ‘topsec(zhangwy)’, who stated that a malicious .mp4 file could be leveraged by an attacker to take control of VLC media player users’ devices.
The issue was flagged as high-risk on the CERT-Bund site, and the vulnerability was assigned a CVE entry (CVE-2019-13615).
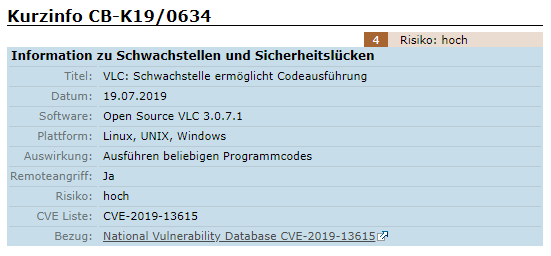
A screengrab taken from the CERT-Bund website yesterday
‘The guy never contacted us’
Over the past couple of days, multiple press reports have been published, warning users of a “critical” security issue in VLC – a popular open source media player with more than three billion downloads.
However, according to VideoLAN president Jean-Baptiste Kempf, the exploit does not work on the latest VLC build. In fact, any potential issues relating to the vulnerability were patched more than a year ago.
“There is no security issue in VLC,” Kempf told The Daily Swig in a phone conversation this morning. “There is a security issue in a third-party library, and a fix was pushed [out] 18 months ago.”
When asked how or why this oversight generated so much attention, Kempf noted that the reporter of the supposed vulnerability did not approach VideoLAN through its security reporting email address.
“The guy never contacted us,” said Kempf, who remains a lead developer at the VLC project. “This is why you don’t report security issues on a public bug tracker.”
Regardless of the means of disclosure, Kempf and his team at VLC were unable to replicate the issue in the latest version of the media player (3.0.7.1).
In fact, the earliest version of VLC that is potentially vulnerable to this exploit is 3.0.2, which was superseded in April 2018, leading to suspicions that the bug reporter was working on a computer running an outdated version of Ubuntu.
“If you report a security issue, at least update your Linux distribution,” Kempf said.
Moreover, says Kempf, it would be very difficult to develop a reliable exploit that worked on older systems, and out of the question to develop a hack against an up-to-date version of the software.
“The issue was there two years ago, but it’s absolutely not possible to take control [of someone’s device now],” he said.
“You need to send a file. The person needs to open it on a vulnerable version of VLC and then you need to disable the security of your machine [in particular, address space layout randomization] to exploit the heap buffer overflow.
“That was patched more than a year ago, in April 2018.”
Bug downgraded
Responding to questions from The Daily Swig via email yesterday, a CERT-Bund spokesperson said: “As far as we know, initial attribution to us was by Softpedia, who wrongly referenced the German Winfuture [link since removed].
“We will downgrade the criticality of our advisory as a result.”
At the time of writing, CERT-Bund has downgraded the vulnerability to ‘low’, although the advisory still says the issue impacts the latest version of VLC.
“It’s completely bogus,” Kempf said. “[On the advisory] they are still claiming [it impacts] 3.0.7.1, which is not the case.”
Discussing the press reports that emerged as a result of the misclassification, Kempf said: “It’s insane. People are saying, ‘You need to uninstall VLC’. It’s the usual people who don’t check their facts.”
A thread published on the VideoLAN Twitter account today provides further technical details.
RELATED VLC patches critical flaws through EU open source bug bounty program






