Cisco Talos investigation shines new light on Russia-linked exploit kit

UPDATED VPNFilter, the multi-stage modular framework that’s thought to have infected hundreds of thousands of network devices around the world, is now known to possess even greater capabilities, after researchers discovered several new modules that add “significant functionality” to the malware.
First reported by Cisco Talos in May, VPNFilter was found to have been attacking routers and other network devices manufactured by Linksys, MikroTik, Netgear, and TP-Link.
The malware, which allows for theft of website credentials and also includes a destructive capability that can render an infected device unusable, was reported by US authorities to be under the control of Russian-backed nation state actors known as Sofacy Group, or Fancy Bear.
Issuing an update in June, Talos expanded the list of target vendors to include ASUS, D-Link, Huawei, Ubiquiti, UPVEL, and ZTE, and noted the addition of new exploitation, packet sniffer, and device destruction modules.
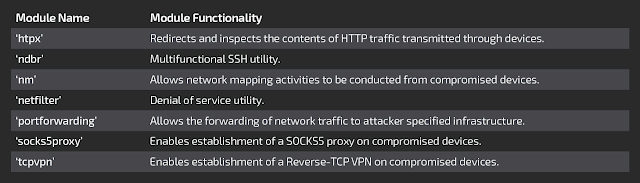
Now, four months after the researchers’ initial report, Talos – in cooperation with the Cyber Threat Alliance and other security partners – said it has discovered seven additional modules that underline the advanced capabilities of the malware’s architects.
“Cisco Talos recently discovered seven additional third-stage VPNFilter modules that add significant functionality to the malware, including an expanded ability to exploit endpoint devices from footholds on compromised network devices,” said Talos threat researcher Edmund Brumaghin.
“The new functions also include data filtering and multiple encrypted tunneling capabilities to mask command and control (C2) and data exfiltration traffic.”
Although Brumaghin said collaboration between Talos and security industry stakeholders around the world has “mostly neutralized” the threat from VPNFilter (adding that most of the C2 control channels for the malware have been mitigated), he admitted that it can still be difficult to detect in the wild if any devices remain unpatched.
Moreover, while Brumaghin said there has been no indication of the threat actor attempting to reconnect with infected devices, he was quick to note that there are still many unanswered questions surrounding VPNFilter and those who developed it.
“Does this mean the actor has abandoned this expansive foothold into the small and home office (SOHO) network device space?” Brumaghin asked. “Are they instead reconstituting their access by starting over, re-exploiting and dropping new unknown malware? Have they given up on having broad worldwide SOHO access in favor of a more tailored approach only going after specific key targets?”
He added: “Whatever the answers may be, we know that the actor behind VPNFilter is extremely capable and driven by their mission priorities to continually maneuver to achieve their goals.”
Offering guidance to anyone who might be impacted by VPNFilter, Craig Williams, director of Talos Outreach, told The Daily Swig: “If a device is believed to be compromised it needs to be completely reimaged firmware wise.
“It’s important that people verify their network devices are still being updated from a security perspective by the manufacture, if the device is no longer being updated it should be replaced.”
This article has been updated to include comments from Craig Williams.






