WordPress and Apache Struts take lion’s share of weaponized security bugs

Exploits exist for a growing proportion of security vulnerabilities found in web and application frameworks, even as the overall volume of flaws is falling, a study has revealed.
In an analysis of vulnerabilities in leading frameworks and their underlying languages, the RiskSense Spotlight Report found that 105 vulnerabilities were found in 2019, compared to 185 in 2018.
However, the proportion of security bugs that were weaponized – referring to the development of exploit code that leverages the weakness – jumped to 8.6%, more than double the 3.9% logged in the National Vulnerability Database (NVD), which tracks security flaws across the entire technology stack.
The only previous year in which weaponization rates for frameworks and their underlying languages eclipsed NVD rates was nearly a decade ago, back in 2011.
Researchers from RiskSense, a vulnerability management platform, blamed the increase on particularly sharp rises in flaws impacting Ruby on Rails, WordPress, and Java.
Weaponization rates have broadly declined for both frameworks and the NVD database across the 10-year period studied.
WordPress and Apache Struts
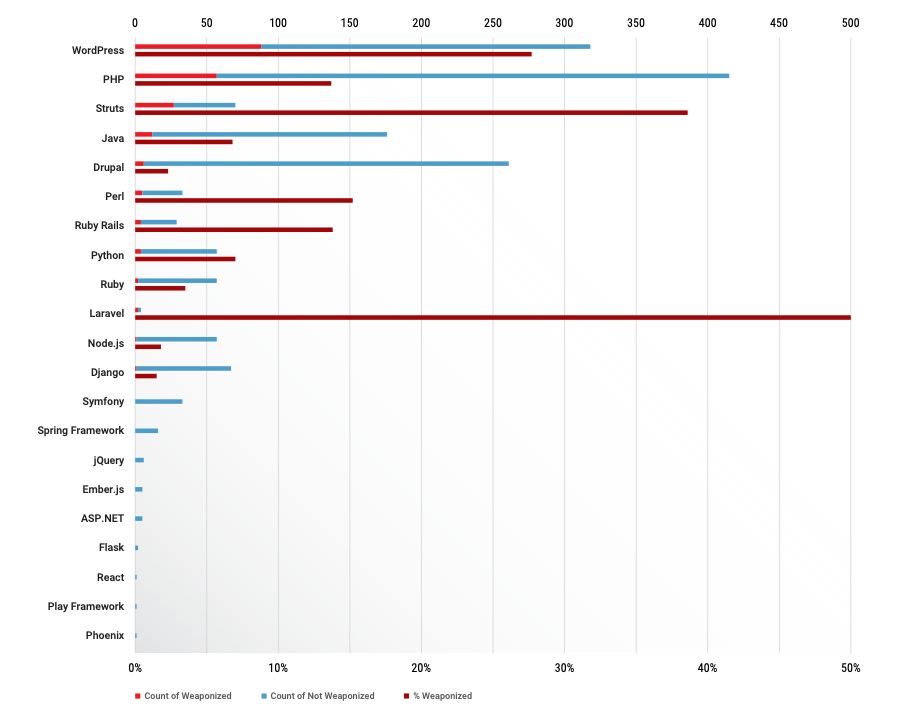
WordPress and Apache Struts together accounted for 55% of all weaponized vulnerabilities in web and application frameworks, RiskSense said.
At 38.6%, Apache Struts also had the highest meaningful weaponization rate (Laravel had 50% but from a statistically insignificant four flaws) – something that can’t necessarily be attributed to the platform’s popularity alone, according to John Dasher, vice president of products and marketing for RiskSense.
“[Apache] Struts probably isn’t as popular as you might think,” he told The Daily Swig, citing a 2019 Stack Overflow survey in which Struts failed to make the top 15 frameworks being used by developers.
“So, it would seem that Struts in particular seems to punch above its weight in terms of attracting weaponization.”
WordPress, however, “draws attacker attention because it is so common”, said Dasher.
“It is also the choice of many do-it-yourself and smaller organizations where web development talent might be lacking,” he added, concluding that vulnerability data suggests its “reputation for security issues continues to be well earned.”
Programming languages
The underlying languages of WordPress (PHP) and Apache Struts (Java) were also the two most weaponized languages.
Dasher urged developers to choose their frameworks carefully.
“When you look at frameworks like Struts that have consistently had problems and also drawn attention from attackers, that should factor into one’s decision,” he said, adding that developers will also have to live with those decisions “for a relatively long time”.
 Most vulnerable web development frameworks and underlying languages (2010-2019)
Most vulnerable web development frameworks and underlying languages (2010-2019)
XSS decline
RiskSense’s researchers also observed a sharp decline in the prevalence and threat posed by cross-site scripting (XSS) issues when comparing the two five-year periods covered in the study.
XSS flaws were the most common and weaponized vulnerability between 2010-2014, but dropped to fourth and fifth respectively between 2015-2019.
The weaponization rate of XSS bugs fell dramatically from 27% to 5.5%.
“This is likely due to the heavy focus on XSS testing during development,” said Dasher, noting that XSS bugs were the most lucrative vulnerability class in a recent HackerOne analysis.
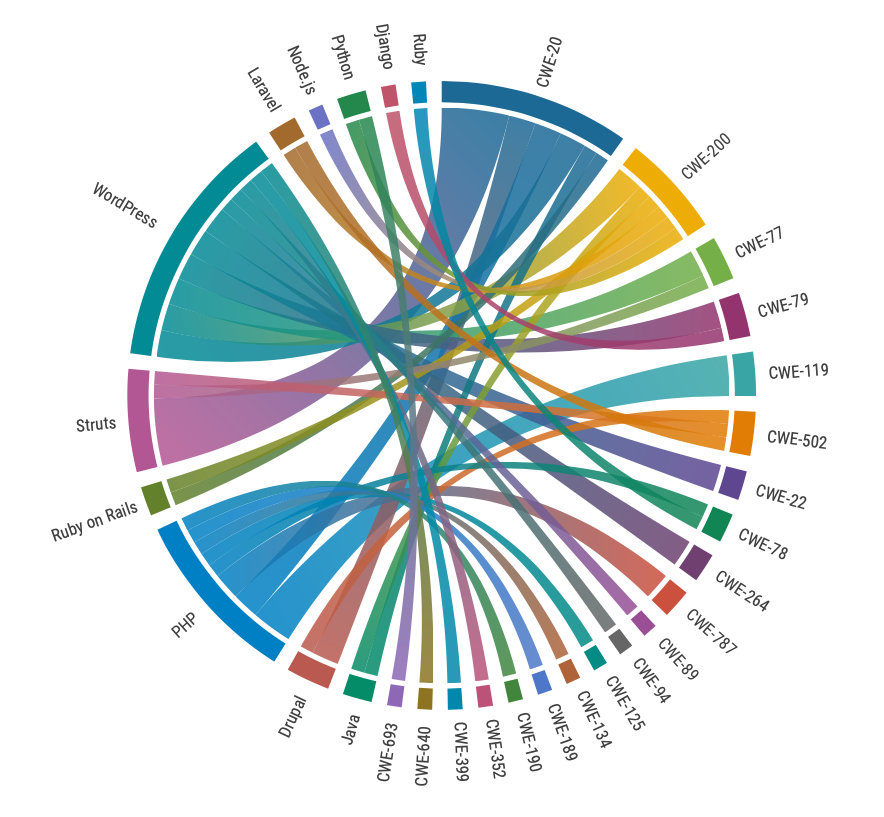
Accounting for 24% of all weaponized vulnerabilities over the past five years, input validation bugs supplanted XSS as the most weaponized bug class. However, the researchers noted that this category covered a wide array – totaling 53 – of attack techniques.
RECOMMENDED WordPress Terror: Researchers discover a massive 5,000 security flaws in buggy plugins
Access control issues, which were mostly attributable to Java, jumped to becoming the most prolific source of flaws in the last five years, but with a weaponization rate of only 2.8%.
Command injection attacks, which top the OWASP top 10, remain comparatively rare, yet accounted for the top three weaknesses by weaponization rate: command injection (60%), OS command injection (50%), and code injection (39%).
The number of SQL injection flaws fell by 74% in volume and from 26% to 10% in terms of weaponization rate.
All 60 remote code execution and all nine privilege escalation flaws covered in the study were weaponized.
 Relationship Between CWEs and languages/frameworks (2015-2019)
Relationship Between CWEs and languages/frameworks (2015-2019)
“Vulnerabilities in frameworks are particularly valuable to attackers, because it means that the application can be abused even when developers are doing everything right from a security perspective,” said Dasher.
“A vulnerability in a framework can allow an attacker to gain control over the app and either steal data from the application directly, or alternatively, to host malicious content to infect visitors.
“This makes them highly strategic both as a method of direct attack, but also supporting the broader lifecycle of malware and cybercrime campaigns.”
CVSS shortcomings
In addition to their insight into framework vulnerabilities, the researchers also said that CVSS, the industry standard for rating the severity of security vulnerabilities, was not particularly efficient at predicting vulnerability weaponization.
Only 12.4% of ‘high-risk’ vulnerabilities under CVSS v2 and 9% of ‘critical’ CVSS v3 flaws were weaponized.
In stark contrast, 95% of flaws flagged as ‘critical’ by threat models that include intelligence from the wild were weaponized, RiskSense reports.
Overall, of the 1,622 CVE entries analyzed across 10 years, 209 were weaponized (12.9%).
The ‘Cracks in the Foundation: Web and Application Framework Vulnerabilities’ study can be accessed for free via the RiskSense website.
RELATED Jenkins security: Latest advisory highlights more than 20 vulnerable plugins






