‘Beautifully simple’ flaw allows attackers to impersonate trusted sites

A serious vulnerability in the latest version of Microsoft Edge enables attackers to spoof URLs with just five lines of code.
The flaw, discovered by Argentinian researcher Manuel Caballero, can make a malicious website appear to be legitimate through the use of the Stop() JavaScript command, which interrupts the page loading process.
With the target URL still appearing in the address bar, the document.write() command can then be used to overwrite the contents of the page.
In his interactive proof of concept, Caballero demonstrates how the PayPal.com URL can easily be spoofed – throwing up major security concerns for Edge users:
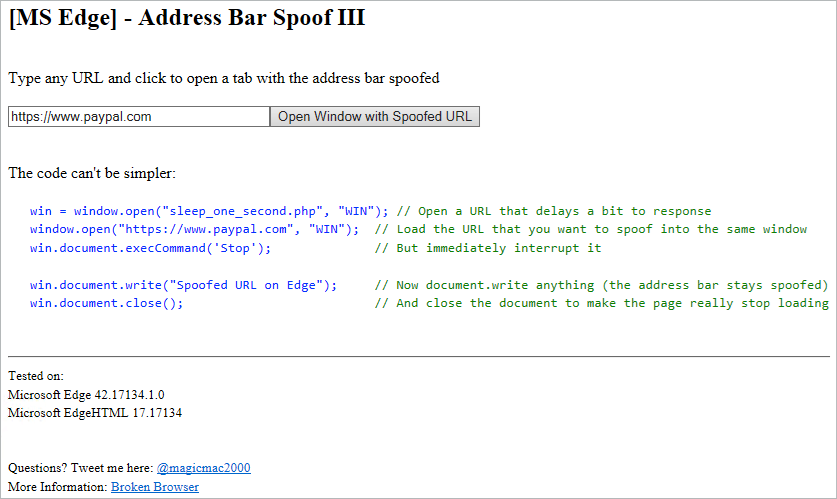
Discussing the implications of the vulnerability in the Windows 10 default browser, Gareth Heyes, researcher at PortSwigger Web Security, told The Daily Swig: “It’s a beautifully simple bug.
“An attacker just needs to create a page that takes a little longer to respond and open it using the open() function in JavaScript, which opens a new tab. It then loads the spoofed URL in the same window before using the document.executeCommand("Stop") command while it’s still loading. They are then able to write to the page.”
“The result is that an attacker can control the contents of a site, which still appears to have a legitimate URL.”
According to Heyes, the zero-day raises serious concerns for Edge users, as it leaves them wide open to inadvertently sharing sensitive data.
“If someone was doing a phishing attack, they could spoof the address bar so it looks, for example, like PayPal.com, but the attacker can control the page and then steal the credentials.”
James Kettle, another researcher at PortSwigger, added: “With this bug, probably the only truly safe way reach any website using Edge is to open a new tab and type the URL by hand, or access it through your bookmarks.”
“Notably, it seems to only work on the latest version of Edge (42.17134.1.0) – suggesting that the Windows security update may have in fact made Edge users less secure.”
Jun Kokatsu, security software engineer at Microsoft, responded to Caballero’s tweet. With the developers aware of the issue, it will hopefully be patched soon.






