Top infosec trends in the social media spotlight this week

In the words of every journalist, intelligence operative, and political pundit that has been engaging on social media: what a week!
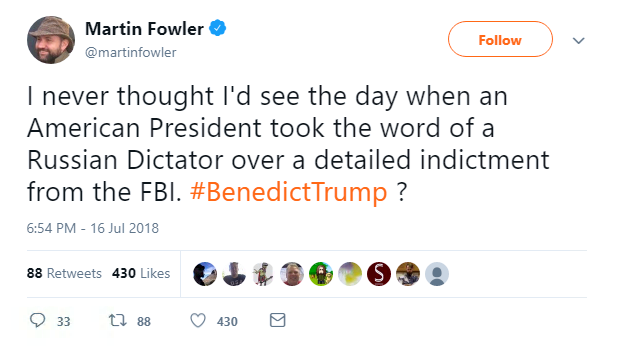
Once again, the geopolitical circus that we’ve seen of late fused itself with the unsuspecting world of infosec, when the US Department of Justice (DOJ) indicted 12 Russian spies for conducting cyber-attacks on the Democratic National Committee (DNC) during the 2016 Presidential campaign. Sound familiar?
The Russian intelligence officers, which the Kremlin denied have any ties to its military operations, stand accused of stealing DNC data through spear-phishing emails and malware, then publishing the hijacked information through online personas like DCLeaks and Guccifer 2.0.
The DOJ investigation, led under special counsel Robert Mueller, released full details of the findings, which provide a significant amount of technical evidence of a sophisticated covert hacking campaign – and indeed the ability of the US government to probe cyber-attacks, as The Intercept pointed out.
Others dismissed the corroborating cues that Russia had held at least some influence over the square off two years ago between Democratic candidate Hillary Clinton and then Republican nominee Donald Trump.
Moscow maintained that the DOJ indictment were a “heap of conspiracy schemes,” while others remained steadfast in their rejection of Mueller’s verdict.
And that was only the beginning.
Yes, news of the charges came days before President Trump was due to meet Russian President Vladimir Putin in Helsinki for high-level talks surrounding Ukraine, Syria, and nuclear proliferation, but generally, improving US-Russia relations, which have deteriorated to the lowest of levels following the annexation of Crimea in 2014.
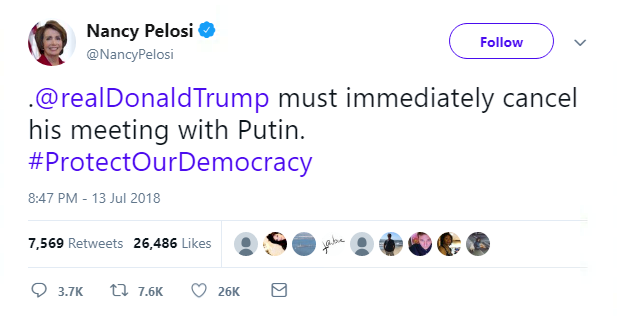
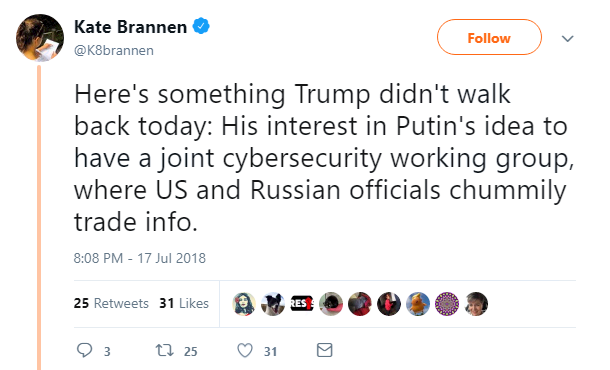
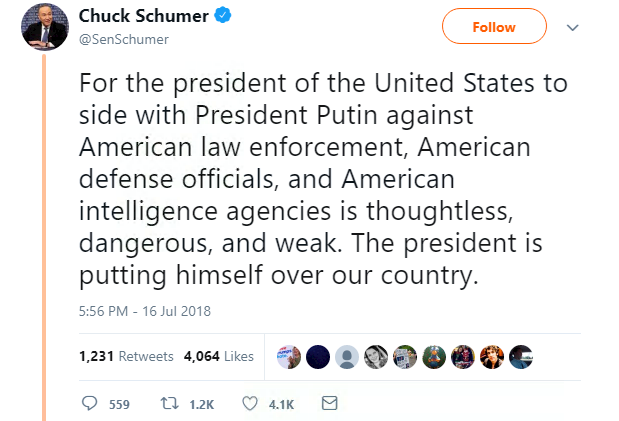
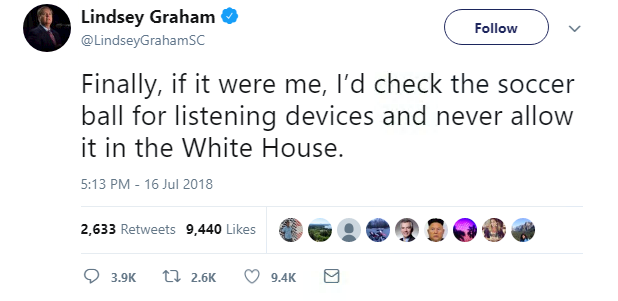
And while progress at the summit may have been made, it was overshadowed by the uproar that occurred when Trump decided to agree with Putin – Russia did not meddle in the US election, and Moscow and Washington should join forces with a joint cybersecurity group.
Although a CBS poll found that nearly 70% of Republicans – less than a third of Americans – approve of how Trump handled his meeting with Putin, social media was, overall, not so impressed.
Trump has since backtracked on his criticism of the DOJ report and support for taking on an ally like Putin – at least he left the Finnish capital with a memento of his fair-weather friend.
Keeping with election security, a top voting machine vendor used in the US admitted this week that remote-access software had been installed on a number of election management systems between 2000 and 2006.
Reported by Motherboard, the election management systems in questions – ones sold by ES&S – raised security concerns due to the possibility that remote access software could allow entry to the voting machines by system administrator and attackers alike.
US Senator Ron Wyden told the publication that using this software was “the worst decision for security short of leaving ballot boxes on a Moscow street corner”.
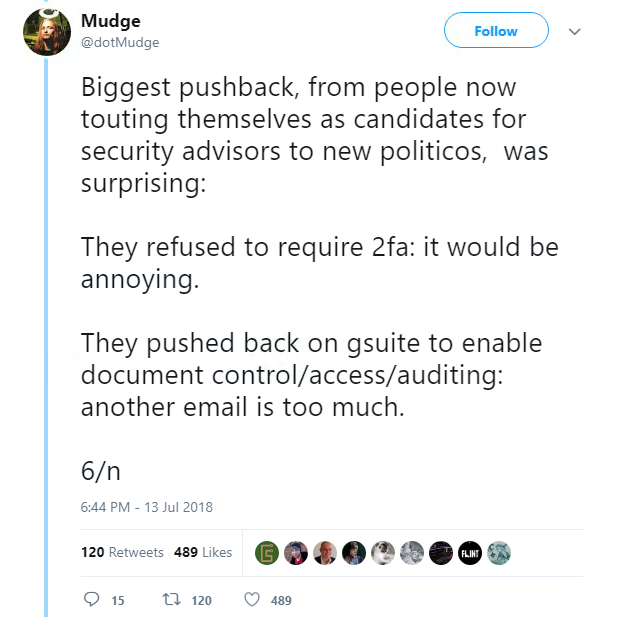
And as if 2016 was a year we couldn’t escape, opinions on election hacking continued to flow online, which included a detailed thread from Mudge, or Peter Zatko, member of the notorious US hacking group L0pht.
Mudge’s 17-part tweet, a must-read really, explains how the DNC had reached out to him for infosec assistance – advice, he said, which the Democrats ignored.
Another thing that people seem to be ignoring, is the sheer number of devices lost by people every year – 26,000, in fact, on London transport alone.
Research by think tank Parliament Street said that commuters had lost over 26,000 electronic devices between April 2017 and April 2018 while travelling in the British capital.
iPhones were the devices that travellers tended to lose the most, at 7,394, and Samsung didn’t much better at 6,091 gone missing in the year.
Security businesses like Centrify were horrified at what this could mean for fraud, with Barrty Scott, the company’s CTO, saying: “Businesses need to adopt a zero-trust approach to all users, verifying users, their devices and limiting access to the volume of data they can access. Failure to take action acts as an open invitation to cyber criminals and hackers who see lost devices as an easy way into a corporate enterprise.”