Top infosec trends in the social media spotlight this week

This week has thrown up some interesting discussion points relating to responsible disclosure and how vendors should – or, in this case, should not – respond to vulnerability reports.
June 11 saw developer Michael Lynch pull focus on flaws in the SiaBerry cryptocurrency mining unit, the most serious of which was a command injection vulnerability on the application login page.
While Lynch demonstrated how the “painfully easy” vulnerability could be exploited with just three lines of code, it was SiaBerry developer Kete Tefid’s response to the bug that riled the security community the most.
SiaBerry and Lynch failed to agree on a disclosure timeline of 60 days, with Tefid claiming he would need six months to patch the simple flaws. And despite a quick fix release to address some of the vulnerabilities, the vendor has remained relatively silent since the disclosure.
All this comes amid reports that SiaBerry ignored suggestions that the platform had basic security issues seven months ago.
“SiaBerry’s team does not demonstrate an understanding or commitment to security,” Lynch wrote. “I don’t believe they are trustworthy custodians of your Siacoin, so I recommend against using SiaBerry software to manage your Sia node.”
The relationship between researchers and vendors became strained once again this week, as 2FA hardware specialist Yubico was accused of taking credit for a flaw that was first identified by others.
As summarized by Computer Business Review, security researchers Markus Vervier and Michele Orrù recently demonstrated that U2F tokens could be circumvented using Chrome’s WebUSB API.
Things took a downward turn yesterday, after Yubico vice president and CISO Jesper Johansson published a blog post detailing how his company had been working with Google to fix certain flaws in WebUSB, with the vendor receiving a $5,000 bounty reward in the process.
Although Johansson did mention Vervier and Orrù in his write-up (saying their work led to the discovery of a “broader set of security concerns”), the infosec community was quick to rally around the researchers, amid claims that Yubico had taken credit for work that wasn’t theirs.
While Yubico’s Twitter feed has fallen silent since the allegations, an update to Johansson’s post reads: “We were just made aware that the original researchers reported the… issue to Google around the same time we submitted it to Google.
“We were not aware of this at the time, we independently discovered it while investigating the public CCID issue.”
In legal news, it’s been another week of six-figure fines for organizations who failed to protect their customer’s data.
The UK’s Information Commissioner’s Office (ICO) has been busy, slapping Yahoo with a £250,000 fine for the 2014 cyber-attack that exposed the details of half a million British users, followed by a £100,000 penalty for the Bible Society, after hackers accessed the personal details of 417,000 charity supporters.
These fines, however, took something of a back seat, as European electronics and telecommunications retailer Dixons Carphone announced it had launched an investigation into a data breach involving 5.9 million customer card details and 1.2 million customer data records.
“Our investigation is ongoing and currently indicates that there was an attempt to compromise 5.9 million cards in one of the processing systems of Currys PC World and Dixons Travel stores,” the company said.
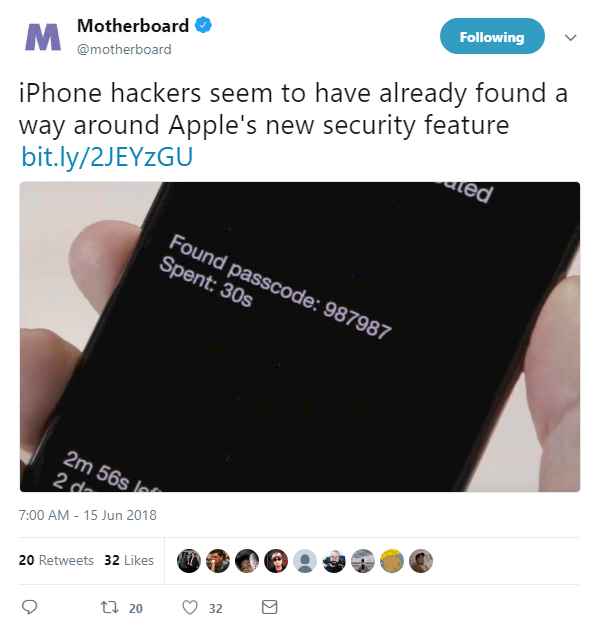
Elsewhere, following a report in Motherboard earlier this month that Apple has been testing a new feature that would render iPhone ‘cracking’ devices useless, it seems the maker of GrayKey – a $15,000 piece of kit used by police and government agencies for this very purpose – has already found a workaround.
According to Motherboard, Apple’s new USB Restricted Mode would turn the iPhone’s lightning cable into a “charge-only interface if someone hasn’t unlocked the device with its passcode within the last hour”, making it significantly harder for law enforcement to gain access.
However, a follow-up article published on the tech site yesterday suggests that Grayshift, the company behind GrayKey, will not go down without a fight.
“Grayshift has gone to great lengths to future proof their technology and stated that they have already defeated this security feature in the beta build,” a forensics expert told reporters at Motherboard.
“They seem very confident in their staying power for the future right now.”
And finally, OpSec enthusiasts shuddered in unison earlier this week, as journalist Harald Doornbos, in attendance at the 2018 North Korea-United States Summit in Singapore, noted that a USB fan was being dished out to press delegates.
While Doornbos said the fan was “handy to stay cool when writing”, security aficionados were quick to discourage anyone from plugging the devices into their laptop, amid fears the fans could carry malware.