Spider ransomware demands payment within four days – and offers a handy tutorial video for its victims

A new ransomware strain targeting victims in the Balkans is being spread through malicious attachments and demanding payment within 96 hours, after which time the victim’s files will be permanently deleted.
The Spider campaign, identified by Netskope researchers on December 10, uses decoy Office documents written in the Bosnian language.
The attachment contains an obfuscated macro code, which launches Windows PowerShell to download a malicious payload that encrypts all important user files.
While attacks of this nature have become all too familiar over the past year, Spider marks a interesting new step in the evolution of ransom-demanding malware.
Not only does the campaign require payment within four days, it also includes a detailed ‘help’ section that contains links and references to the resources needed to decrypt the files:
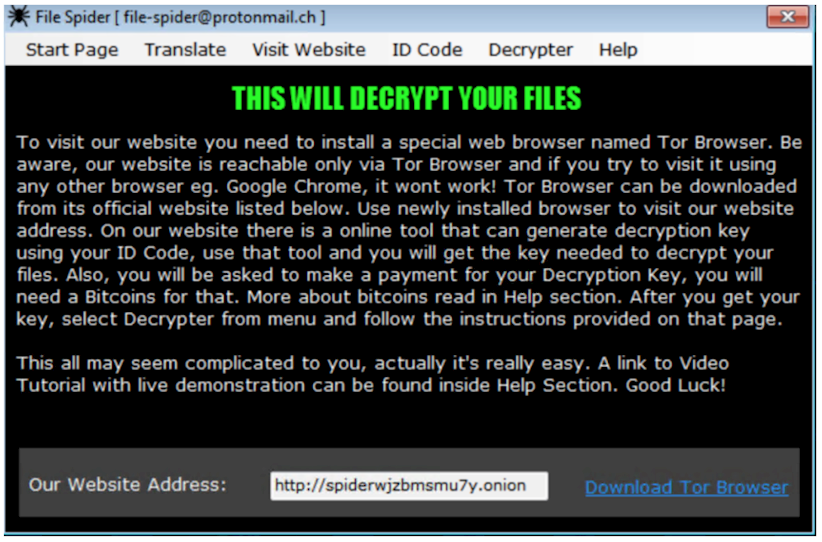
During their investigation, the researchers also uncovered a tutorial video that provides a step-by-step guide to payment and decryption.
“Ransomware continues to evolve and prevail as a top threat to all verticals in many organizations,” said Netskope researcher, Amit Malik. “The addition of Spider ransomware as a new cob in the increasing ransomware web is a classic example.
“As ransomware continues to evolve, administrators should educate employees about the impact of ransomware and ensure the protection of the organization’s data by making a regular backup of critical data.”
Malik added: “In addition to disabling macros by default, users must also be cautious of documents that only contain a message to enable macros to view the contents and also not to execute unsigned macros and macros from untrusted sources.”






