HTTP Desync Guardian released to help prevent user accounts from being hijacked
Amazon Web Services (AWS) has launched a new tool to further protect against HTTP desynchronization attacks.
The tool – dubbed HTTP Desync Guardian – is designed to “analyze HTTP requests to prevent HTTP desync attacks, balancing security and availability”, AWS explains in its GitHub project notes.
HTTP Desync attacks, also known as HTTP request smuggling attacks, were first discovered in 2005 but have been brought back to the fore in recent years.
At Black Hat USA 2019, PortSwigger Web Security’s director of research James Kettle demonstrated how the somewhat forgotten hacking technique could be leveraged to poison web caches and desynchronize entire systems.
“HTTP desync attacks (aka HTTP request smuggling) cause a complete breakdown in request/response matching, which can enable attackers to mass-hijack other user’s accounts, persistently compromise pages via cache poisoning, and break into internal systems,” Kettle told The Daily Swig.
RELATED Ancient technique tears a hole through modern web stacks at Black Hat 2019
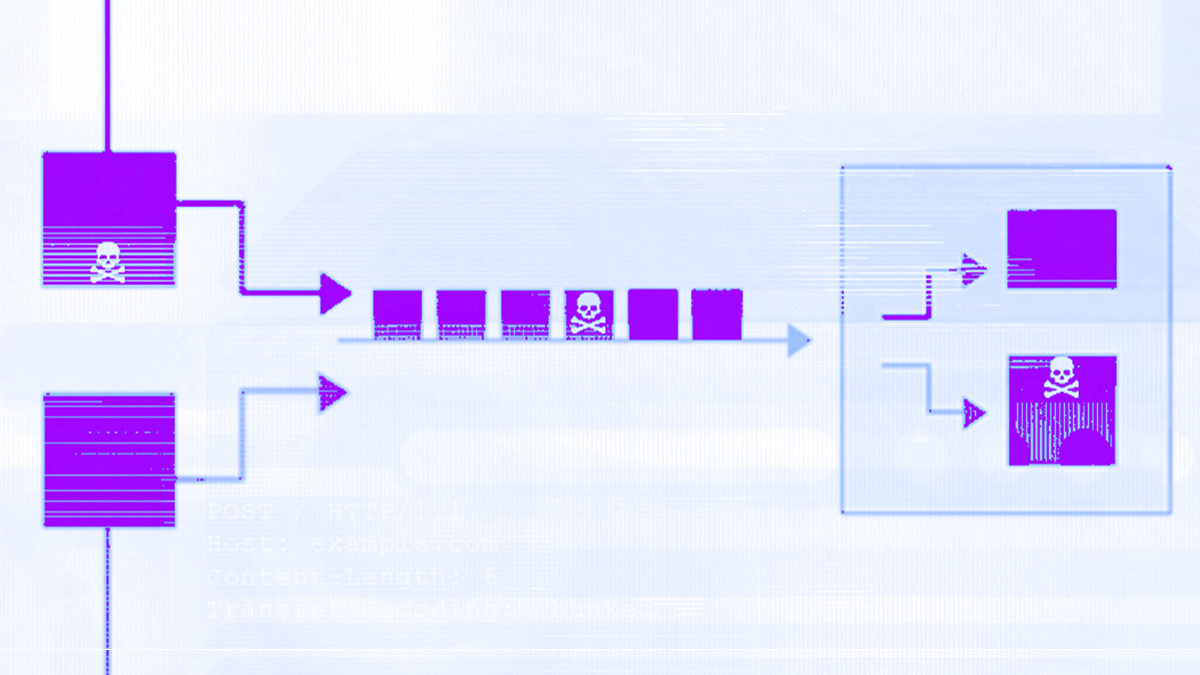
HTTP requests are understood based on the agreement between front and back end servers, which together decide how long they are.
HTTP request smuggling attacks can enable an attacker to exploit this agreement and gain access to a target system.
If an attacker sends an ambiguous message that is interpreted as being different lengths by the front and back end servers, some of this message could spill over and allow system access.
AWS’ new tool prevents this by categorizing HTTP requests into those which are RFC compliant and those which could risk deserialization, flagging potential security issues to users.
“Preventing desync attacks has always required a trade-off between security and compatibility, and HTTP Desync Guardian’s default configuration looks like a good balance,” Kettle said.
“The approach looks sound, but as for whether it goes far enough to prevent all attacks... I’d need to take a closer look to answer that.”
“It certainly shouldn’t be seen as a substitute for applying security patches to your back-end server.”
READ MORE Black Hat 2020: Web cache poisoning offers fresh ways to smash through the web stack






