‘Belarus Cyber-Partisans’ say they gained access to all entries in and out of the country over the past 15 years

As international tension ratchets up over Belarus’s authoritarian regime, a hacking group claims to have accessed the full database of those crossing the country’s borders, including the alleged movements of KGB officers and president Alexander Lukashenko himself.
Belarus was plunged into crisis last year after the presidential election in August gave Lukashenko a landslide victory. As the opposition cried foul, massive protests broke out across the country, triggering thousands of arrests.
Since then, a group of hackers called the Belarus Cyber-Partisans has carried out a series of attacks on government databases, with the aim of helping to destabilize the regime.
The group is made up of a number of tech professionals, mostly believed to be based outside Belarus itself.
Now, in their latest hack, the Cyber-Partisans say they have gained access to records of all entries into, and exits out of, the country over the past 15 years, through all official border crossings.
The data relates not only to Belarus citizens but also other nationals crossing the Belarusian border either by air, rail, road, or foot.
“This data would enable us to identify fake passports issued for espionage purposes for KGB and other agents who pose risk to Belarusians in other countries,” a Cyber-Partisans spokesperson tells The Daily Swig.
“Data also includes all the trips made by Lukashenko and his… close circle, and would help reveal illegal activities and put sanctions on them.”
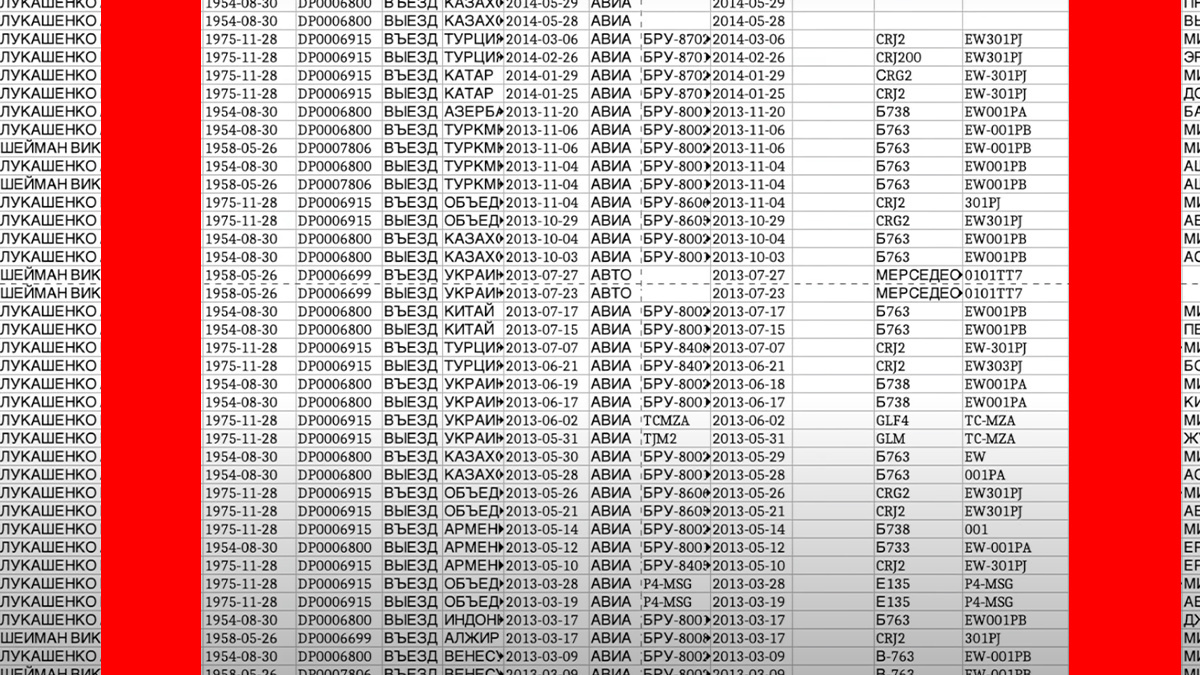 A sample of the purported Belarus border crossing dataset
A sample of the purported Belarus border crossing dataset
Border patrol
The group’s previous leaks have proved instrumental in helping justify international sanctions against the regime.
They included the entire police database, including CCTV footage and the employment history of officers, as well as the tapped phone calls of regime supporters and opponents.
Also accessed were the personal details of every Belarusian citizen, including passport photos, home address, and place of work, along with the last 10 years of emergency calls history, including those made by people reporting their co-workers for opposing the regime.
“We uncovered internal phone calls over which unlawful commands were dispatched to violently crack down on peaceful protests, and beat and torture the people,” the spokesperson says.
Read more of the latest cyber warfare news and analysis
The group also believes that its actions have been acting as a deterrent to even greater human rights abuses by members of the regime.
“The deanonymisation of the regime’s siloviki [strongmen] had variable effects; at first only a small fraction cared about their name being public,” the spokesperson says.
“With time, as our information got more detailed – address, phone, photos, service history, spouses, etc – more and more of them got terrified of the consequences of those leaks. We had many of them contact us and ask us to remove them from the leaked list.”
A YouTube video from the Cyber-Partisans account offers a glimpse into the purported border crossing dataset.
Migrant crisis
The mounting migrant crisis at the Polish border is believed to be the result of a deliberate policy by Lukashenko, who was angered by earlier sanctions.
There are already moves to broaden those sanctions, and Lukas Andriukaitis, associate director at the Atlantic Council’s Digital Forensic Research Lab, believes that the information revealed by the hack could increase the pressure.
“This will be quite a headache for the Belarusian KGB. Not only will their identities be revealed, which will require [them] to reshuffle some of the KGB agents, but also their potential crimes in Europe might be exposed,” he tells The Daily Swig.
‘I think a lot will depend on [whether] any of the revealed names will be associated with operations in Europe, just like it happened with Bellingcat exposing Russian operatives in the West.
“If any of the agents will be associated with crimes outside of Belarus, this might serve as an additional argument to sanction Belarus, which already is walking on thin ice due to the migrant crisis.”
YOU MIGHT ALSO LIKE Exploit-as-a-service: Cybercriminals exploring potential of leasing out zero-day vulnerabilities






