‘Silhouette’ side-channel attack measures response time of blocked and unblocked accounts

A flaw in the ‘user blocking’ function that’s been widely adopted by social media sites can be leveraged to deanonymize users’ account information, researchers have discovered.
Found on popular social media services such as Twitter, the ‘block’ feature was designed to provide legitimate account holders with a means of controlling who can view their pages.
While the feature aims to protect users from online harassment, spam, or other undesirable activities, researchers at Nippon Telegraph and Telephone Corporation (NTT) found it could be exploited by another site to expose visitors’ social media identities.
Silhouette threat
According to NTT, the condition for such account identification to take place is that a user who is currently logged into a social media service that is vulnerable to this threat visits a malicious website.
Prior to executing the attack – dubbed ‘Silhouette’ – the malicious third party creates personal accounts within the target social media service, and uses these accounts to systematically block some users on the same service.
These ‘signaling accounts’ are used to construct a combination of non-blocked/blocked users. This pattern can then be used as information for uniquely identifying user accounts.
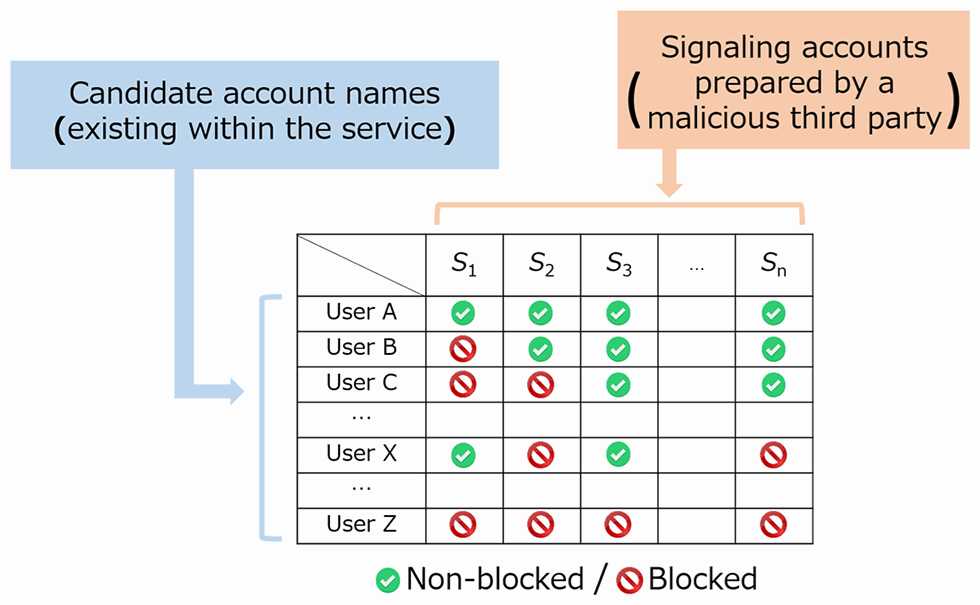
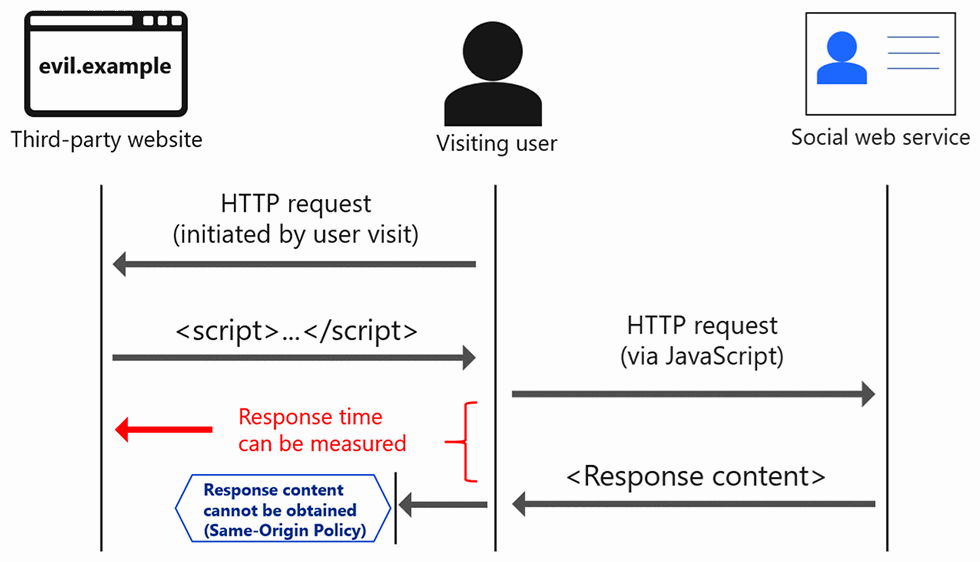
NTT noted that if a user visits a malicious site on which a script for identifying account names has been installed, communication with the pages of each of those signaling accounts will be protected by same-origin policy.
However, the researchers discovered that communication response time is statistically different depending on whether the content is visible or invisible.
“The malicious third party can use this difference to infer whether a visiting user is blocked or non-blocked from each of the signaling accounts, and finally, to compare the results of this inference with the previously constructed pattern,” they said.
“In this way, the malicious third party can identify account names in the social web services of those users.”
NTT, whose findings were presented at the IEEE Symposium on Security and Privacy in London earlier this year, said it is cooperating with service providers, browser vendors, and other parties to develop countermeasures to this privacy threat.
“To counter this type of attack, the social web service can apply techniques such as checking Referer to assess the validity of an HTTP request or assigning the SameSite attribute to cookies,” the researchers said.
“In addition, users of a social web service vulnerable to this threat can use the private browsing function when visiting a third-party site or make sure to log out when finished with the service thereby avoiding account name identification.”
While NTT said it has discovered a “novel” privacy threat in Silhouette, it should be noted that cross-origin timing attacks are by no means a new phenomenon, as this post, dating back to 2009, confirms.
RELATED: A dangerous blend: Side-channel attack exploits CSS vulnerability






