Move aims to help organizations identify weaknesses in their cloud container infrastructure

Cloud security experts from Microsoft have launched an attack matrix for Kubernetes, the open source cloud orchestration framework.
The move is designed to help organizations identify gaps in their defense against the different security threats that target Kubernetes, which has grown to become one of the world’s most popular open source systems for the management of containerized applications.
As outlined in a blog post earlier this month, the Kubernetes attack matrix takes its inspiration from the Mitre ATT&CK framework – a globally-accessible knowledge base that’s used by those within the security industry for threat modeling.
“While Kubernetes has many advantages, it also brings new security challenges that should be considered,” said Yossi Weizman security research software engineer at Microsoft’s Azure Security Center.
“Therefore, it is crucial to understand the various security risks that exist in containerized environments, and specifically in Kubernetes.”
READ MORE Mitre launches ATT&CK for industrial control systems knowledge base
According to Weizman, when the Azure security team started to map the Kubernetes threat landscape, they noticed that although many of the cloud attack techniques were different from exploits that target, say, Linux or Windows systems, the tactics are similar.
“Therefore, we have created the first Kubernetes attack matrix: an ATT&CK-like matrix comprising the major techniques that are relevant to container orchestration security, with focus on Kubernetes,” Weizman said.
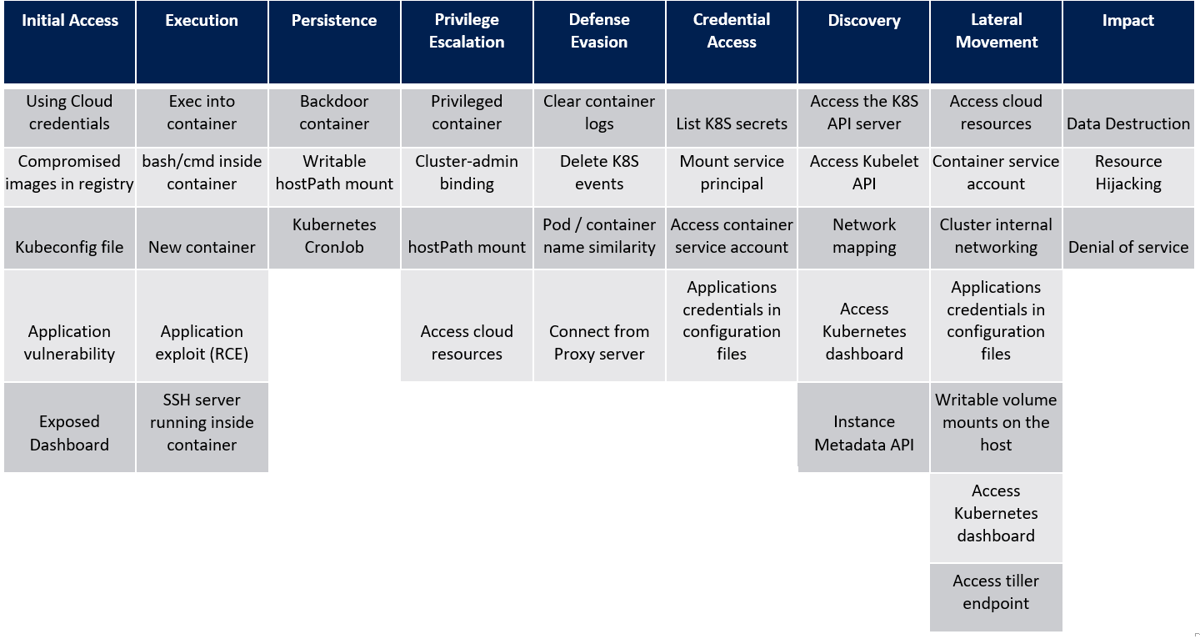 The Kubernetes attack matrix borrows from the Mitre ATT&CK framework
The Kubernetes attack matrix borrows from the Mitre ATT&CK framework
The Kubernetes attack matrix features nine principal tactics:
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Impact
Each one of these tactics contains several techniques that can be used by attackers to achieve different goals.
“Understanding the attack surface of containerized environments is the first step of building security solutions for these environments,” said Weizman.
“The matrix… can help organizations identify the current gaps in their defenses’ coverage against the different threats that target Kubernetes.”
RELATED Using the ATT&CK framework to discover exploit dependency chains






