Finding dependencies between adversary techniques can allow security teams to better optimize their defenses, according to Mitre Corporation’s Andy Applebaum

If information security teams can understand how adversaries construct their exploit chains, then they can better optimize their defenses.
The questions is: how can defenders gain access to this information in the first place?
At the FIRST annual conference in Edinburgh, UK, last week, Andy Applebaum, a lead cybersecurity engineer at The Mitre Corporation, presented new methodologies that aim to do just that.
ATT&CK: The best form of defense
Adversaries rarely execute their techniques in isolation. Instead, these techniques are used as stepping stones to further execution opportunities.
According to Applebaum, most exploits have fundamental requirements that must be met before execution.
For example, to leverage Microsoft’s remote desktop protocol (RDP), an adversary must first have access to valid credentials.
In an effort to shine fresh light on technique dependencies, the researcher and his colleagues adopted a data-driven approach using ATT&CK – a framework that was developed by Mitre to understand adversary tactics, techniques, and procedures (TTPs).
“ATT&CK is grounded in real data from cyber incidents,” Applebaum said. “All the TTPs are things that we have seen adversaries do in the wild or are common knowledge for red teamers.”
 Andy Applebaum presenting at the FIRST conference last week
Andy Applebaum presenting at the FIRST conference last week
By way of example, Applebaum took Cybereason’s insight into Operation Cobalt Kitty, noting that the report mentions five techniques: propagation via Windows admin shares; pass the hash; pass the ticket; obtaining credentials for credential dumping; and account discovery.
“What’s interesting in looking at these five specific techniques is that they all relate to each other,” Applebaum explained.
“To laterally move via pass the hash, pass the ticket, or Windows admin shares, you need to gain credentials with credential dumping, and also discover admins on the target with account discovery.
“The idea with this data analysis is that if two techniques have some sort of relationship, you should expect to see them all be reported in the same report. There is an intrinsic dependency that makes them linked in a chain.”
Applebaum showed how data from ATT&CK could be presented in a matrix, which then allows defenders to track the frequency of technique pairs.
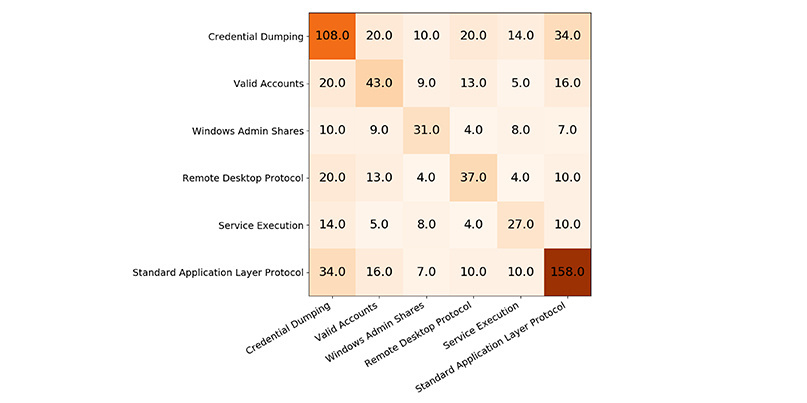 Counting co-occurrences: Shared technique references via ATT&CK framework
Counting co-occurrences: Shared technique references via ATT&CK framework
In the above example, ATT&CK delivers 14 reports that mention both ‘service execution’ and ‘credential dumping’; there were 20 reports between ‘valid accounts’ and ‘credential dumping’; and five reports of ‘valid accounts’ and ‘service execution’.
“This gives us an approximation for what the relative reporting frequency is for each technique pair,” Applebaum said.
Going further, the researcher showed how each row in the matrix could be converted to its relative percentage, which better demonstrates the apparent strength or weakness of a chosen technique pair.
For example, 29% of all reports mentioning ‘windows admin shares’ also mention ‘valid accounts’.
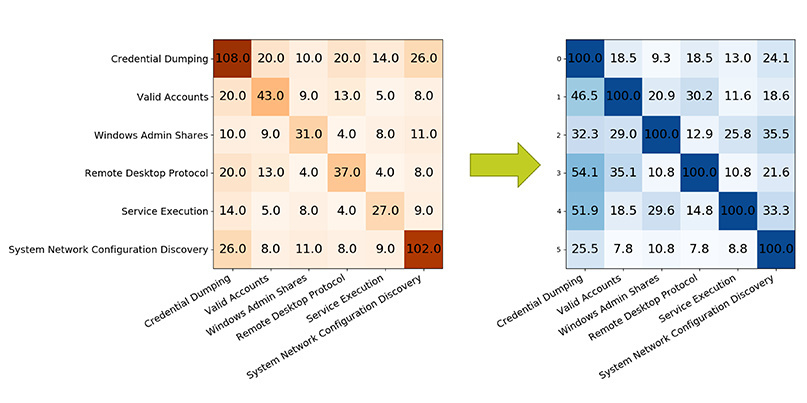 Co-occurrences as a percentage
Co-occurrences as a percentage
Visualizing the data in this manner, Applebaum said, can allow information security teams to start developing hypotheses relating to co-occurrence between techniques.
Semantic analysis
Separately, Applebaum showed how semantic analysis could also be used to gain information about technique relationships.
“The idea is that leveraging pre- and post-conditions will allow us to construct technique chains,” said Applebaum. “Using these chains, we can then identify the technique relationships.”
In order to conduct a semantic analysis of attack techniques, Applebaum utilized CALDERA, open source software that’s designed to automate the adversary emulation process.
“The idea, from a dependency analysis perspective, is that we can connect the actions to objects, based on their pre-conditions and their post-conditions, and then construct a graph showing how the actions relate to each other.
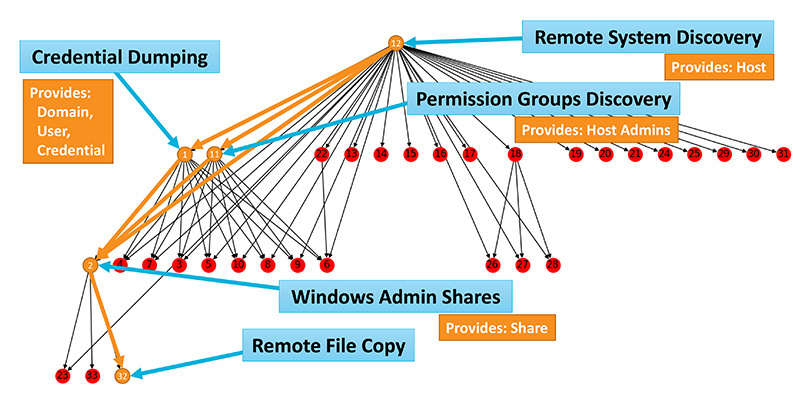 Mandatory dependencies in CALDERA’s logic
Mandatory dependencies in CALDERA’s logic
According to Applebaum, this approach can allow security teams to gain better insight into mandatory dependencies. In other words, which techniques are always required before executing another technique.
“Another thing we can do is technique set enhancement,” he said. “Here the question is: given a set of techniques, can we determine first if that set is self-contained?
Breaking the chain
During the course of his presentation, Applebaum stressed that neither approach was perfect. Shortcomings in the data-driven threat report analysis include subjective bias within reports, while logic bugs in CALDERA that can lead to data loss.
Despite these caveats, the researcher stressed that security teams who can gain insight into attack technique relationships will find themselves in a stronger defensive position – particularly when it comes to threat hunting.
“If I know what techniques are dependent on each other, I can hunt for techniques that enable the one that I’m specifically looking for,” he said.
“If I’m looking for an alternative technique, I might be able to key off from something if my initial hypothesis fails. If I can’t find RDP, maybe I should look for pass the hash.”
RELATED CVE board looks ahead to the next 20 years of vulnerability identification






