EU study warns of growing trend where one attack can leave countless organizations vulnerable

The European Union has forecast there will be four times more software supply chain attacks in 2021 than there were in 2020, as cybercriminals shift to larger, cross-border targets.
The European Union Agency for Cybersecurity – also known as ENISA – has published a new study analyzing the anatomy of a supply chain attack following a number of high-profile incidents in recent months.
The report (PDF), titled ‘Threat Landscape for Supply Chain Attacks’, looked at 24 such incidents that have occurred between January 2020 and July 2021.
One for all, all for one
Among the findings, ENISA revealed that around 50% of the supply chain attacks studied were attributed to know APT groups, while 42% were not attributed to a particular source.
The study also determined that the attackers’ main motivations lay in gaining access to source code and customer data.
Read more of the latest news and analysis about supply chain attacks
The EU-funded study came in the wake of two major cyber-attacks that have made headline news in the past 12 months.
Firstly, the SolarWinds incident saw attackers exploit known vulnerabilities in IT software Orion, which was used to manage servers at organizations including various arms of the US government, threat response firm FireEye, and Microsoft.
The attacks – which may have begun as early as March 2020 but were only detected in December that year – have been linked to Russian state-sponsored threat group APT29 (AKA ‘Cozy Bear’).
MUST READ Kaseya denies ransomware payment as it hails ‘100% effective’ decryption tool
More recently, the notorious REvil ransomware gang exploited known vulnerabilities in IT management platform Kaseya VSA, compromising an estimated 1,000 organizations that use the software.
The group demanded a $70 million ransomware payment, which Kaseya denied it has paid.
The ENISA report reads: “Unfortunately, these two examples are not isolated cases and the number of supply chain attacks has been steadily increasing over the last year.
“This trend further stresses the need for policymakers and the security community to devise and introduce novel protective measures to address potential supply chain attacks in the future and to mitigate their impact.”
Known incidents
A timeline of the events in the study details the level of impact from these incidents and identifies those thought to have been behind the attacks.
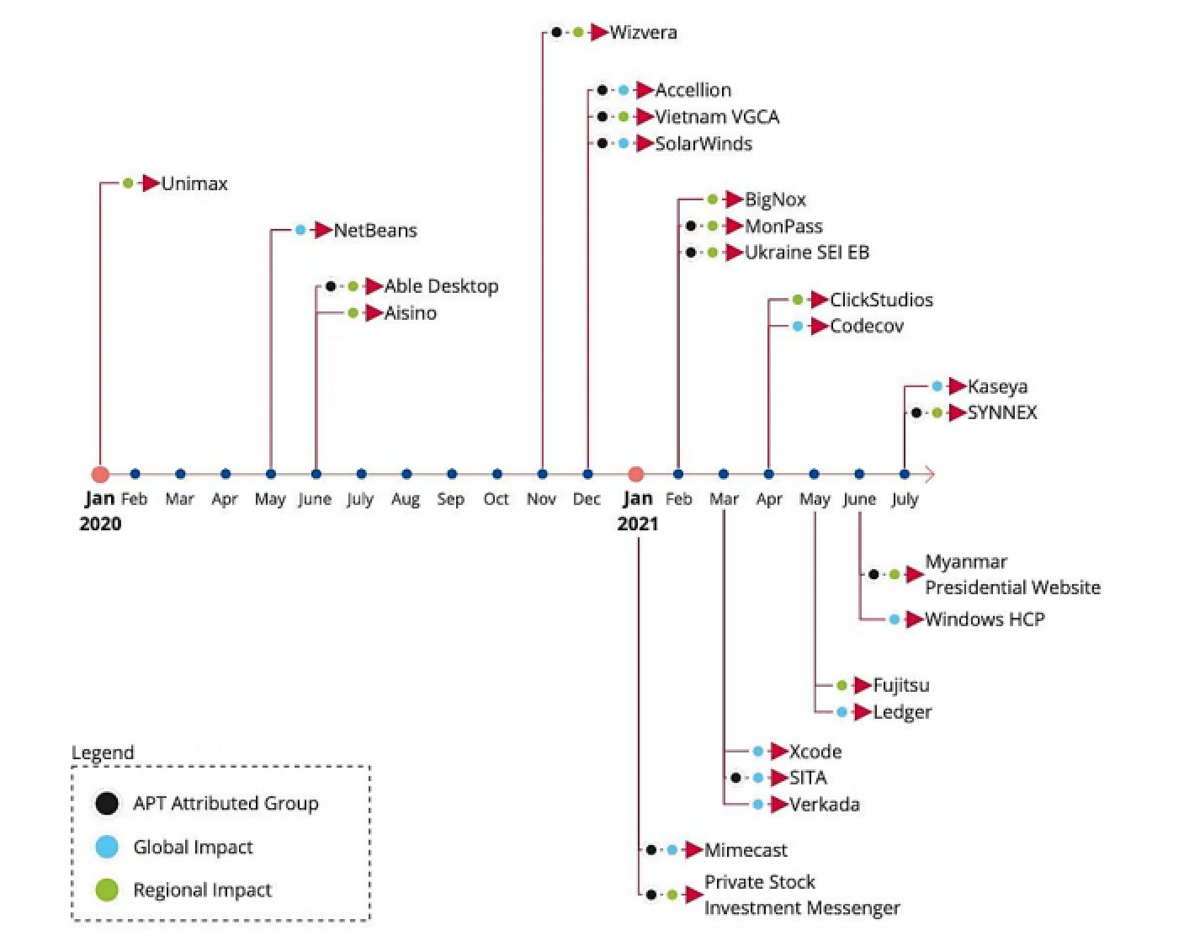 A timeline of the attacks studied in the report
A timeline of the attacks studied in the report
The report stated that 66% of supply chain attacks were committed by exploiting an unknown vulnerability, while 16% leveraged known software flaws.
When it came to supplier assets, most attacks during the specified timeline aimed to compromise code (66%), followed by data (20%) and processes (12%).
As for customer assets, supply chain attacks most commonly targeted customer data (58%), followed by key people (16%) and financial resources (8%).
Classifying cases
The report’s authors also proposed introducing a taxonomy – a scheme of classification – for mapping supply chain attacks by identifying what has happened, and how.
It takes into account the supplier and the customer, pinpointing what assets were targeted and what techniques were used to gain access.
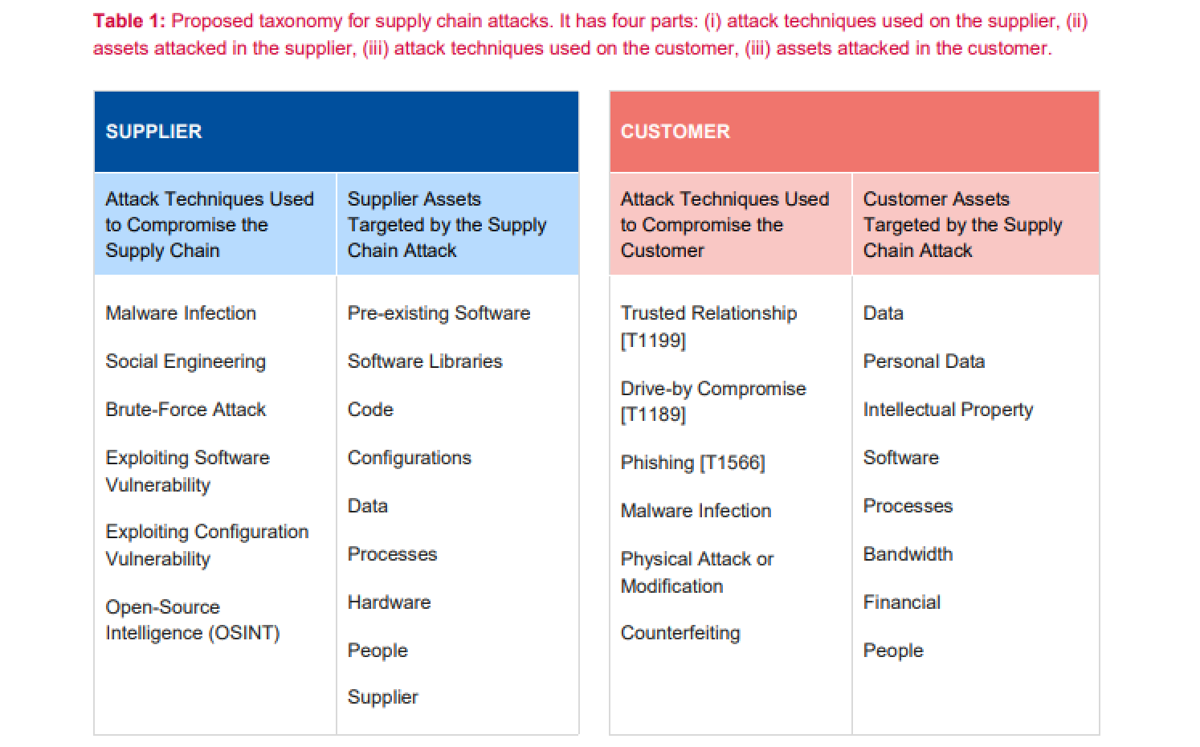 The report's authors proposed a taxonomy for supply chain attacks
The report's authors proposed a taxonomy for supply chain attacks
“For each of these four distinguishing elements in the taxonomy, we have defined the elements that better characterize a supply chain attack,” the report states.
“By selecting the corresponding elements, it is possible to have a better understanding of what is known or not known about an attack.”
The authors also noted that the taxonomy is “conceptually different” from the Mitre ATT&CK framework, and aims to complement rather than replace it.
Serious risk
The report’s authors concluded that the recent shift towards supply chain attacks is likely to significantly increase the cybersecurity threat this year. Four times more supply chain attacks are expected to take place in 2021 than in 2020.
“The inherent global nature of current supply chains increases the potential impact of these attacks and broadens the attack surface for malicious actors.”
Also increasing the risk is the fact that a large number of attack vectors (66%) in the incidents investigated still remain unknown.
“A lack of transparency or the ability to investigate poses a serious risk to the trust of the supply chain,” wrote the authors, adding that “improving the process of transparency and accountability is the first step to improving the security of all elements in the supply chain and protecting final customers”.
Finally, the report recommends that EU member states “establish good practices” and coordinated actions “to reach a common level of security”.
ANALYSIS Aaron Portnoy – ‘There’s no silver bullet for ransomware or supply chain attacks’






