Amid the platform’s continued growth, the potentially immense security challenges have not gone unheeded

The GitHub Security Lab was set up by the software development platform in November 2019.
Headed up by Nico Waisman, the lab’s mission, first and foremost, is to improve security in open source projects.
With GitHub claiming that more than 90% of enterprise software now uses at least some open source elements, the need to improve the security of the OSS ecosystem is more important than ever.
And, as Waisman points out, there is an imbalance between software developers and security professionals: GitHub estimates the ratio at 500:1.
Securing open source, he says, needs an open source approach.
Under the Hub
Last year marked another milestone for GitHub, as the Microsoft-owned company saw 50 million users create a jaw-dropping 44 million project repositories.
Amid the software development platform’s continued growth, however, the potentially immense security challenges have not gone unheeded.
“GitHub is where most of the world’s development happens,” Waisman told The Daily Swig. “GitHub believes that security is not just an opportunity for us, but a responsibility.
“My team tries to bring together security researchers and maintainers, and companies across the industry to share that belief that we need to do something about open source, and try to help secure that open source ecosystem.
“It is a huge task that nobody can do by themselves. That is why the team has its own security researchers, but also works with the community and industry.”

Nico Waisman
The GitHub Security Lab has three different aspects. The first is a core group of security researchers who are working to help secure the open source ecosystem.
“This year alone, we’ve found around 122 vulnerabilities,” Waisman explained. “But we don’t just want to find unique vulnerabilities. That’s like a game of Whack-a-Mole. We want to do that at scale. Instead of vulnerabilities alone, we want to go after BadClasses. The reason for that, is once you are able to go after BadClasses you will find them in all the codebases.
“The other aspect is the community,” he added. “We want to nurture a community of security researchers around GitHub and around OS projects. We need that help. We need the help of everyone we can get to secure open source projects. We want to scale security researchers around the world to help us.
“Finally, the other aspect of my team is the industry. We’ve funded an open source community of around 20 companies, around the same philosophy. We know lot of companies in the industry have the problem of needing to secure the open source supply chain.
“Everyone is doing their own thing, working on their own plans. Some of those plans overlap so there was a need in the industry to build a coalition of companies, to work with the same objectives.”
Security at scale
Waisman was a security engineer at GitHub before moving to the Security Lab. Prior to that, he spent some 20 years as a security researcher in his native Argentina, becoming vice president for Latin America at security vendor Immunity.
But security research was not always Waisman’s goal: he had previously planned to become a journalist.
“I am not an engineer. I dropped out of school a couple of times, and finished my studies in journalism,” he recalls. “I started in cyber research, but I was getting burned out through working non-stop, so I decided to study journalism as a hobby, midway through my career.”
In the end, Waisman decided against a move into the media. After a spell running the consulting arm of US vendor Cyxtera, he moved to Semmle.
Semmle developed automated code analysis software and was acquired by GitHub last year. The organization’s QL tool formed the basis of GitHub’s CodeQL vulnerability discovery tool.
BACKGROUND GitHub showcases new code-scanning security tools at virtual event
Waisman hopes that CodeQL, and the collaborative nature of the GitHub Security Lab, can make open source applications more robust.
“Nowadays, security has to be part of the developer culture,” he argues. “For every 500 developers you have one security researcher. So, the model of a security researcher reviewing millions of lines of code is basically impossible. And that’s the case in open source, and for private companies too.
“So, we need a way to scale security researchers and to take that knowhow and make it a force multiplier. And have developers see security as part of their culture. One of the main tasks we are working on is building the tools to help development teams around the world make that easy.”
 A raft of new security features were unveiled at the GitHub Satellite event in May
A raft of new security features were unveiled at the GitHub Satellite event in May
Part of this is code scanning, which Waisman argues takes away a lot of the heavy lifting that comes with checking projects for vulnerabilities.
Each time a developer issues a pull request – asking for their code to be incorporated into the original author’s code base – or committing code to a repository, the scanner runs a series of security checks.
“That builds a DevSec pipeline in every open source project, and I firmly believe this is one of those things that will move that needle, in terms of security,” he says.
This also allows developers to work on the security flaws in their own code as, Waisman says, they know their code best. This smooths the sometimes-troubled relationship between developers and security teams, and make sure vulnerabilities are fixed earlier in the development cycle.
“What security researchers can do… is model vulnerability classes. Security researchers have that knowhow. Now they can model a vulnerability class in Code QL.
“Once we’ve modelled it, we can run it on every open source project in GitHub, so we can work on the next thing and prevent the next thing from happening.”
According to Waisman, one advantage of the Security Lab’s automated approach is that once a vulnerability is spotted, anyone who makes the same mistake – even in entirely different code – receives an alert.
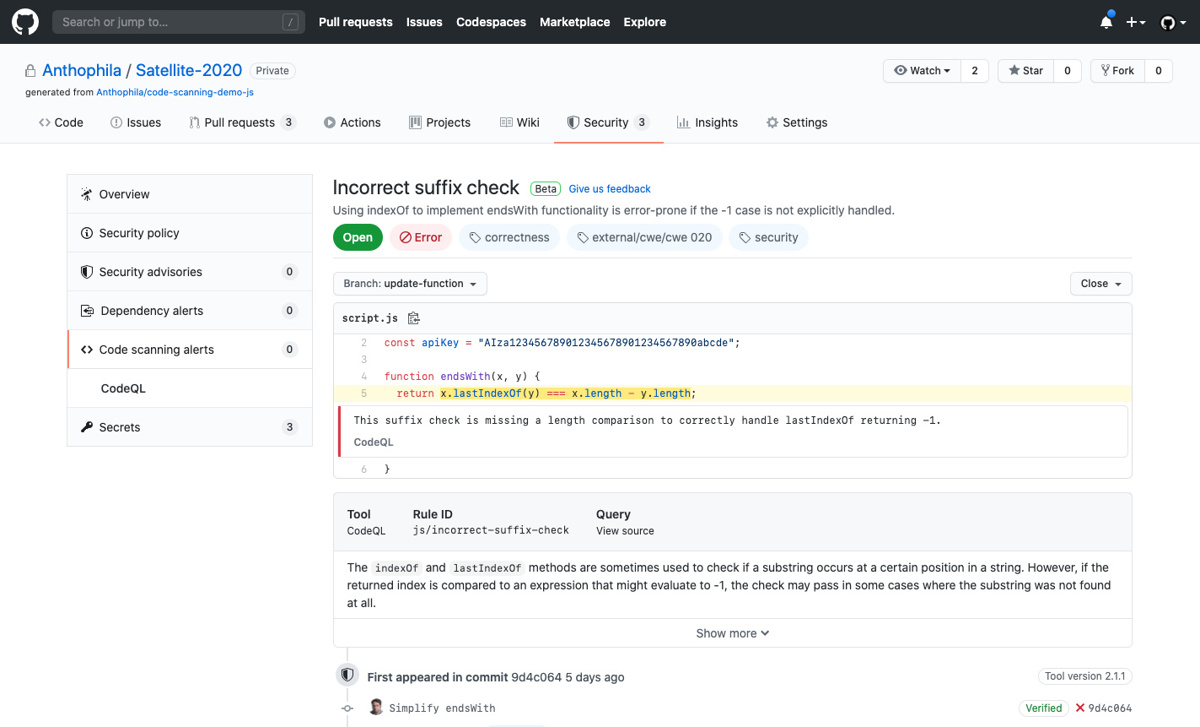 Code scanning made easy
Code scanning made easy
Push and pull
Flagging errors in code, though, is only effective if developers act on them. Do they?
“The security community can be very adversarial about developers,” Waisman admits. “The old security idea was [we would] come out of nowhere, point out your problems, and make you do the hard work yourself.
“We are trying to change that. We are building relationships with developers, rather than saying: fix that in so many days or I will go public and make your life miserable.”
It does not have to be that way, he says. GitHub’s motto is “developers first”. The relationship between the security team and developers is changing for the better.
“It is a cultural change we are seeing everywhere,” he says.
Securing GitHub’s own infrastructure
GitHub itself has been a victim of cyber-attacks. In February 2018, the organization was subject to what was then the second largest DDoS assault ever seen.
As a well-known online service, the company is aware that it is a target.
“We have expanded our capacity to defend against attacks like that,” Waisman says. “We have tools and technologies to mitigate against them.”
GitHub has, though, avoided the worst impacts of Covid-19: the business was already highly distributed, with 70% of staff working remotely.
“I would not specifically triangulate security issues with the current crisis,” he says.
RESOURCES How GitHub secures open source software
“We have distributed workflow. The cultural change was already happening in terms of security and we are contributing to that with our tools. With digital transformation there will be more companies online, along with bad actors. The good thing is that security has grown so much over the last couple of years and will continue growing.”
And for Waisman, the goal remains to make open source as secure as it can be.
“For us, it’s a responsibility,” he says. “A lot of development is happening around GitHub and everyone is using open source. We want that to happen – it’s the soul of GitHub. If we want people to continue to use open source, they need to have robust and secure open source projects.
“That’s why we believe that by having secure, open source projects or helping them secure them, we’ll have more people adopting open source.”
READ MORE Interview: Sonatype’s Brian Fox on open source security and ‘drama-free’ DevSecOps






