Leaky buckets, phishing, and malware take center stage in latest data breach report
Spying, ransomware, and misconfigured cloud-based systems were a leading cause of data breaches last year, according to the latest edition of Verizon’s Data Breach Investigations Report (DBIR).
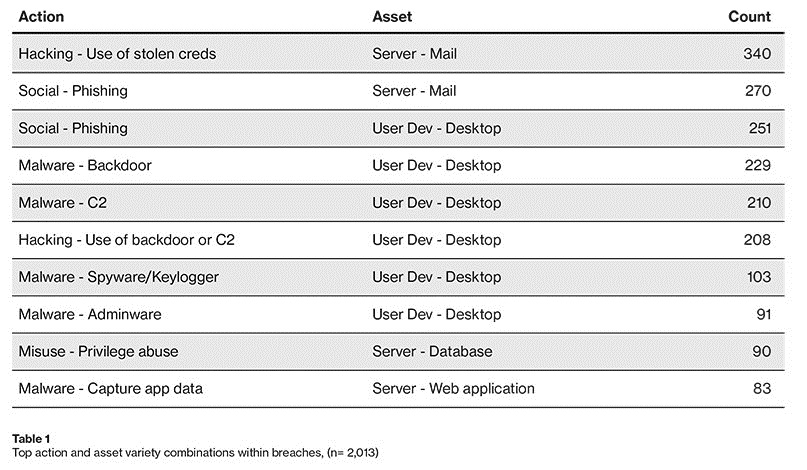
Attackers breaking into cloud-based email servers using stolen credentials featured as the main vector in 60% of web application-based attacks.
By contrast, only 6% of breaches in the DBIR involved vulnerability exploitation – something comparable to the Apache Struts security flaw exploited in the infamous Equifax breach of 2017.
Malware that captured web data – such as Magecart – and privilege abuse on databases each featured in around 4% of attacks, but the root cause of most breaches remained some combination of either phishing and/or malware.
According to the DBIR, a third of data breaches involved at least some element of social engineering, while 28% featured malware as a component. One in five (21%) included human error.
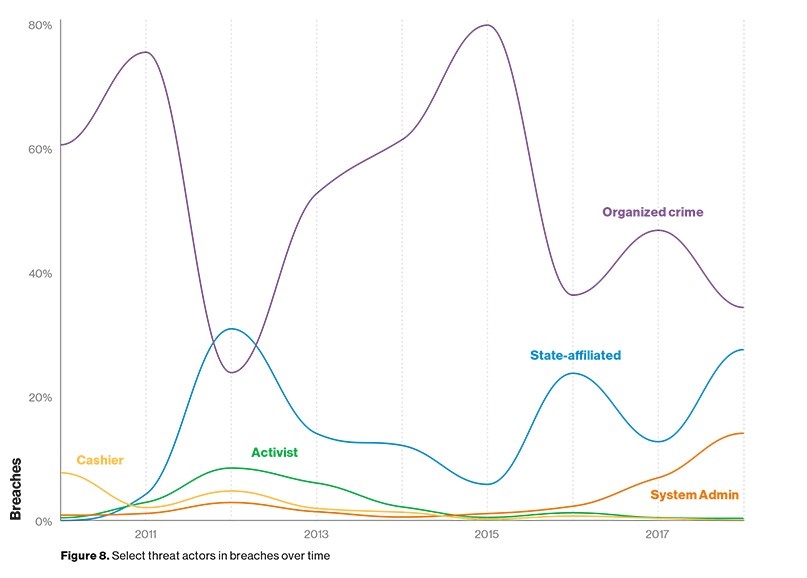
Espionage and cyber sabotage were the key motivation behind a nearly a quarter of all breaches, with nation states or state-affiliated actors blamed for 23% of breaches.
Although a major cause of breaches, cyber espionage was eclipsed by incidents linked to either cybercrime (39%), insiders, partners, or attributed to simple human error.
The study, released on Wednesday, also found that more 60 million records were breached in the last 12 months due to misconfigured cloud-based file storage, such as Amazon buckets, illustrating that even a small slip-up can expose a huge volume of sensitive information.
Ransomware remains a huge threat and accounted for almost a quarter of all related malware-related incidents.
By contrast, crypto-mining accounted for less than 5% of incidents recorded in the DBIR. Crypto-miners of all types failed to make it into the top 10 list of malware varieties in this year’s report.
The 2019 edition of Verizon’s DBIR is based on an analysis of more than 41,000 security incidents. It includes more than 2,000 confirmed data breaches across 180 countries during the last 12 months.
Nearly half (43%) involved small business victims, but healthcare-related organizations (15%), the financial services industry (10%), and public sector entities (16%) were also very much in the firing line.
Enterprises are still slow to locate attacks, with over half of all breaches taking one month or longer to discover.
The lag between breach and discovery gives attackers plenty of time to hack deep into targeted network before locating and exfiltrating sensitive data.
Businesses and their customers are left open to the threat that their data could be used maliciously before anyone realizes something is amiss, Verizon warns.
The DBIR is based on real-world data breaches investigated by Verizon and third-party contributors including the likes of the FBI, US Secret Service, UK legal services firm Mishcon de Reya, UK insurer Chubb, and the Irish Reporting and Information Security Service (IRISS CERT), among others.
Industry partners include McAfee, Check Point Software, CrowdStrike, Recorded Future, Rapid7, Palo Alto Networks, Tripwire, and Kaspersky Labs.






