Top infosec trends in the social media spotlight this week

Today marks International Women’s Day, a chance to celebrate pioneering women’s contributions across all industries – while also addressing the ever-present gender gap in some.
Last year, The Daily Swig spoke to a number of cybersecurity’s leading female figures and asked them what the industry needs to do increase gender diversity.
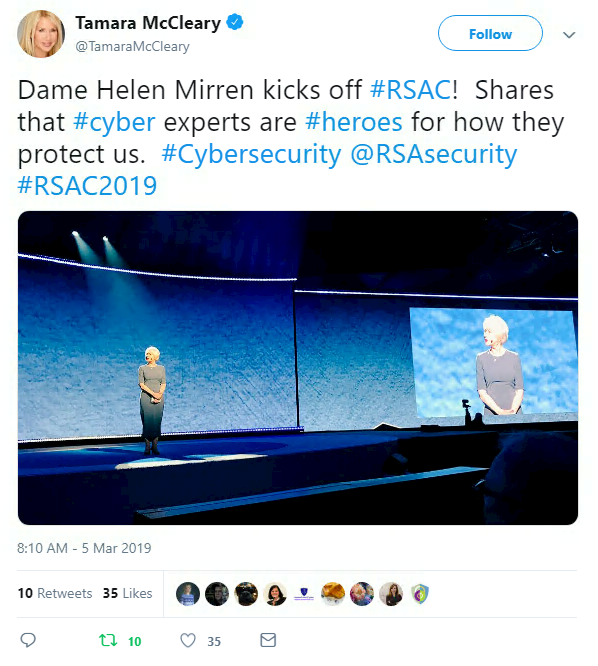
This week, the RSA Conference (RSAC) held in San Francisco made true on its promise to do better by adding more women to its roster, including (surprisingly) British Oscar-winning actress Dame Helen Mirren.
In 2018, RSAC booked just one woman to deliver a keynote, Monica Lewinsky. According to research by Eclat Marketing, there was a 213% increase in female keynote speakers this year.
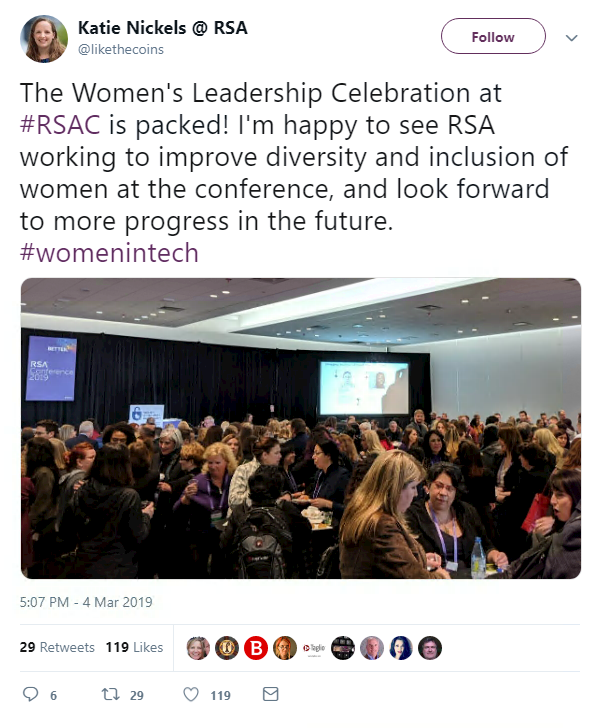
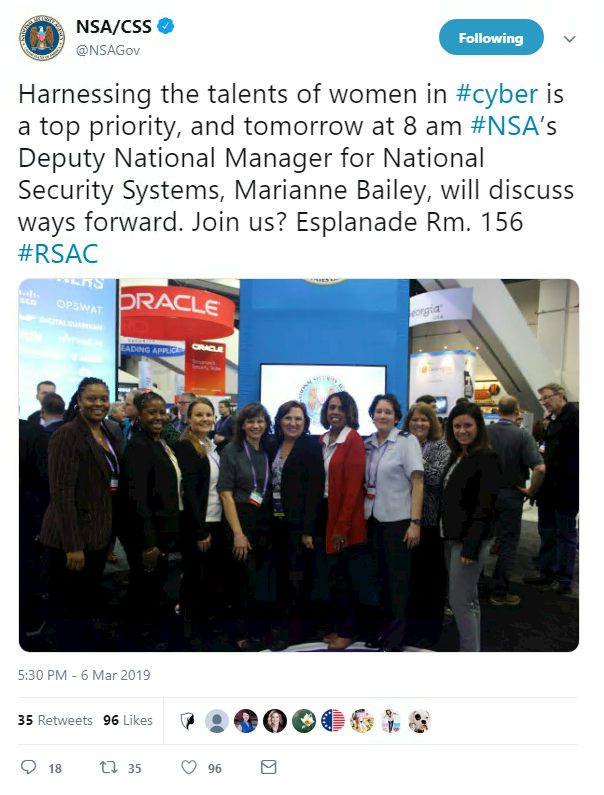
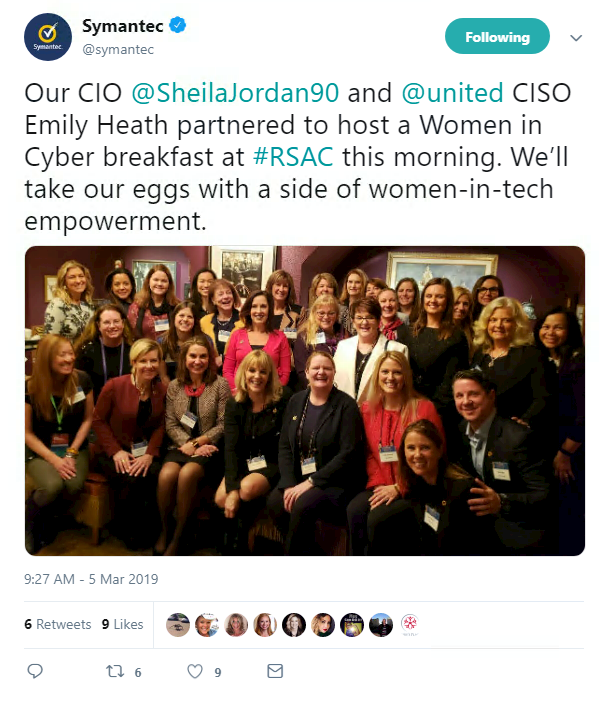
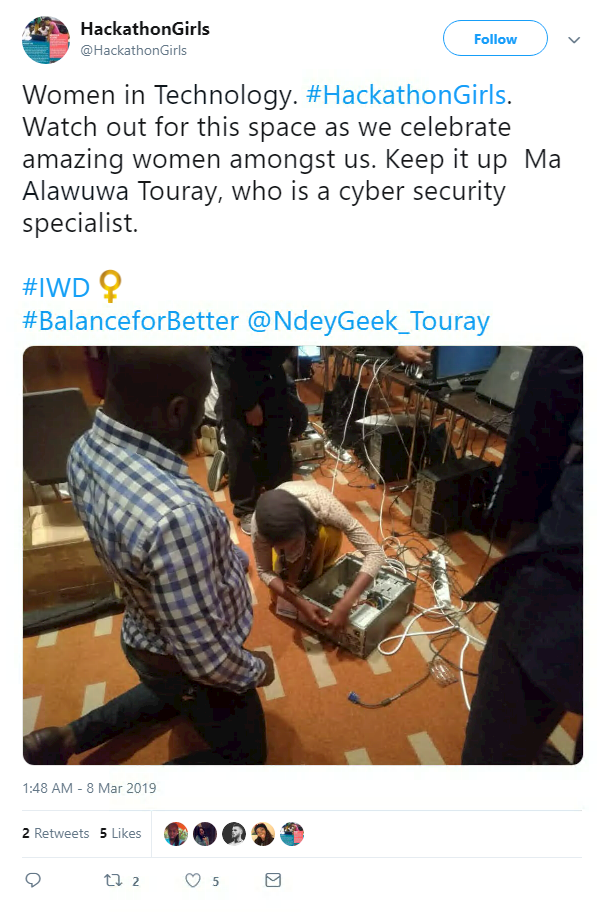
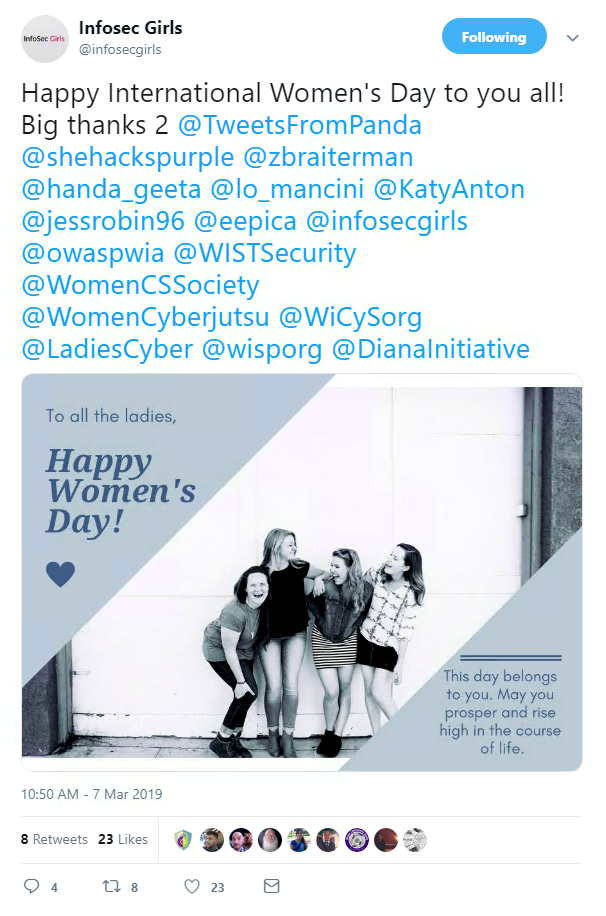
Beyond conference speakers, the security community as a whole has been praising women’s achievements on Twitter today.
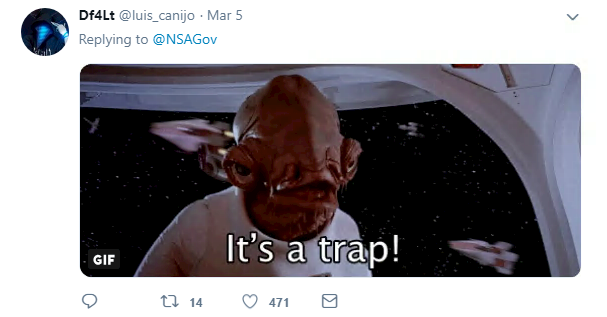
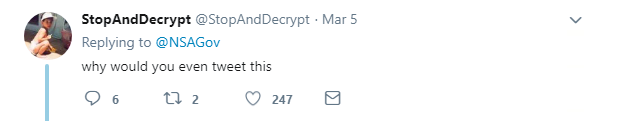
Back at RSAC, and the US National Security Agency (NSA) raised eyebrows when it offered free charging points to conference attendees.
It’s not entirely clear if NSA was joking, since every security bod worth their salt would question plugging their phone in to a charger maintained by the planet’s most various data-harvesting spy agency.
Needless to say, the Twitter replies were pretty skeptical about the whole thing.
The prize for the greatest RSAC booth this year has to go to FAKE Security.
The 90s-styled vendors peddled their unique brand of “security products” (also in travel size), guaranteeing that if they can’t fix your cybersecurity problem then… well… it “can’t be fixed”.
Even Twitter’s own Jake Williams, aka @MalwareJake, was won over by the prank.
Fortunately, the stunt was all a clever PR job designed to remind people that cybersecurity is no joke.
The booth was the brainchild of vendor Authentic8 which states: “For decades, there has been an unhealthy cycle of exploits, solutions, purchases, and more exploits. FAKE Security is our way of poking fun at the absurdity of the $100 billion cybersecurity industry.”
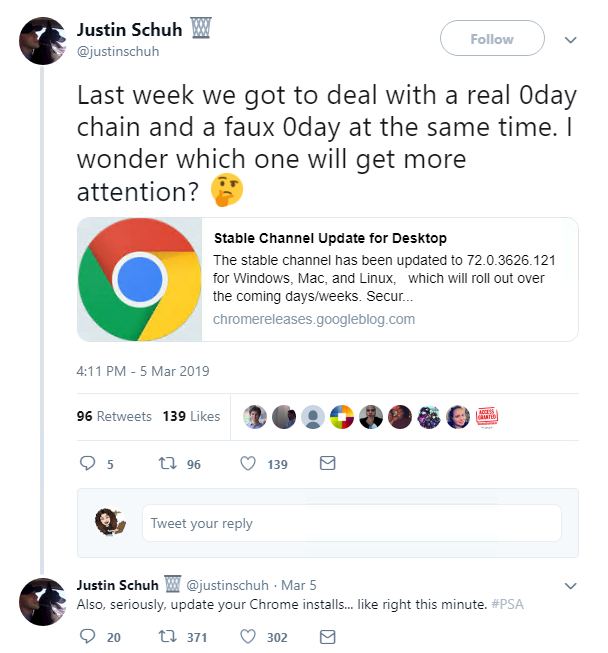
A seriously worrying 0-day was discovered in Google Chrome this week, a use-after-free vulnerability in the FileReader API that can lead to the execution of code and denial-of-service attacks.
The bug (CVE-2019-5786) is being actively exploited in the wild, leading the tech giant to issue warnings to its users.
Head of Chrome’s security and desktop team Justin Schuh released a Public Service Announcement on Twitter to remind people to update immediately.
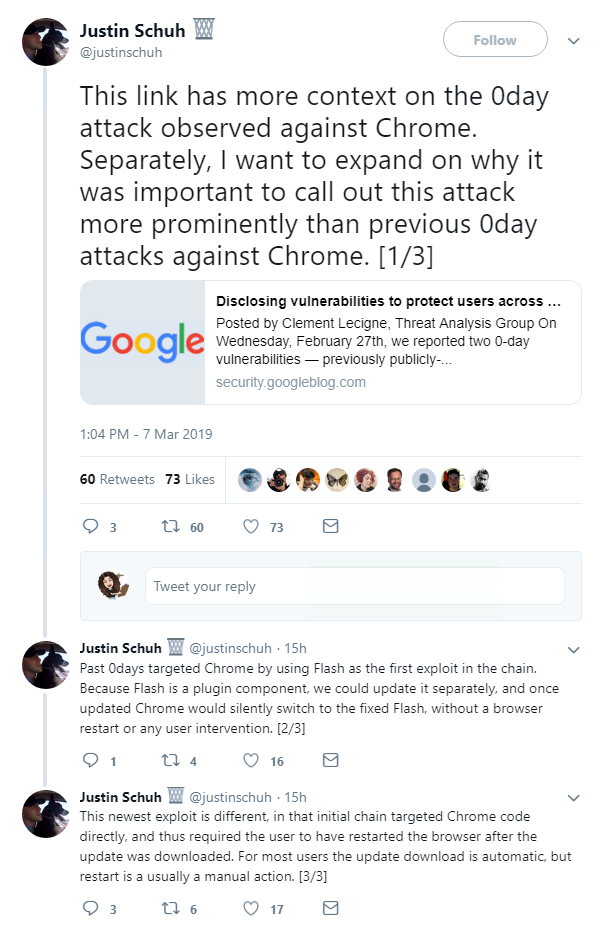
He also gave more context as to why he was drawing attention to this 0-day, rather than others in the past.
So if you’re using Chrome and haven’t already, then seriously – update your browser.
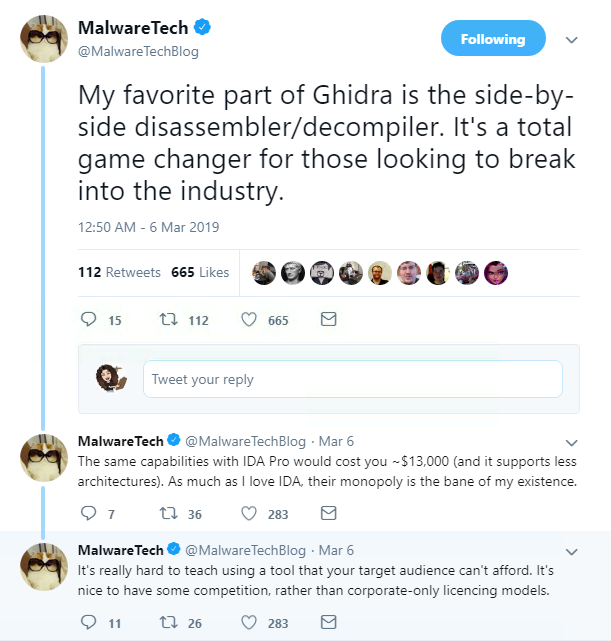
Finally, the NSA’s newly-released Ghidra tool was the talk of the security industry this week.
The platform allows the analysis of suspicious code samples by security researchers and reverse engineering enthusiasts, among other features, as The Swig reported this week.
It gained a mixed reaction online. There were those who were slightly suspicious, but the free tool pulled in the plaudits from other researchers, especially when compared to the current expensive options.
In fact, the online community was so intrigued by Ghidra, that two fans even wrote a song about it.
It remains to be seen whether the song, which opens with “the NSA used to hack without remorse, now their tools are becoming open source”, will catch on.