Top infosec trends in the media spotlight this week

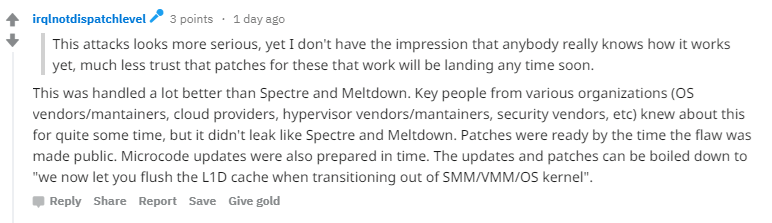
This week saw the disclosure of yet another bug affecting Intel chips, this time dubbed Foreshadow.
The vulnerability affects processors released since 2015, and by exploiting the flaw an attacker may access sensitive information.
A processor’s lock box could be specifically targeted to leak data, the research team from KU Leuven university and the universities of Adelaide and Michigan said.
The flaw, which has now been patched, was likened by many to the Meltdown and Spectre vulnerabilities, which work in a similar way to this attack.
It also signaled the final straw for some who were already losing patience with vendors.
However, it should be pointed out that, unlike with the Spectre and Meltdown flaws, the disclosure of this bug came after a patch had already been devised.
It’s been almost a whole week since Defcon 26 wrapped up, but tongues are still wagging about the multiple security incidents at Caesars Hotel, where the event was hosted.
Last week, we reported how one Google researcher was even kicked out by security thanks to a misjudged tweet.
Now, multiple reports of hotel staff entering rooms and claims they searched through personal belongings has led Defcon organizers to investigate what exactly happened.
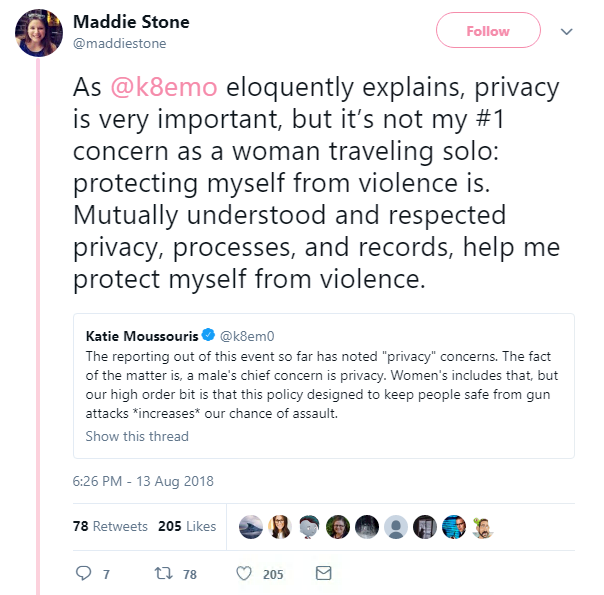
Katie Moussouris, hacker and founder of Luta Security, detailed her shocking account on Twitter.
She said she opened the door to security wanting to search her room (who staff at the front desk failed to verify), was shouted at by management, and claims she was “attacked by people in her own community” for speaking out.
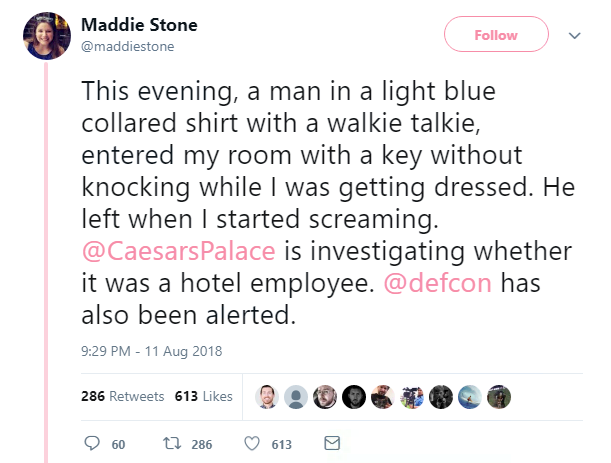
Google engineer Maddie Stone also said a male member of staff entered her room without knocking while she was getting dressed.
After the horrific mass shooting in Vegas last October that killed 58 people and injured 851, Caesars was one of the many hotels that has stepped-up security efforts.
Staff now perform searches of all hotel rooms with a ‘do not disturb’ tag on their door for more than 24 hours – but policy insists that a “visual” sweep is conducted, and that personal belongings are left untouched.
But representative of Queercon, a group promoting LGBT diversity in infosec, claimed to have video showing two staff members taking photographs and filming belongings in a room they rented out – a clear violation of this policy.
Scores of Defcon attendees were affected by the searches, and Moussouris threatened not to return to the event after her experience at Caesars.
Defcon’s Marc Rogers even offered his resignation in an open letter to the hacker community.
An investigation is ongoing into what exactly happened, and Rogers is urging anyone who was affected to get in touch.
As Rogers put it: “I do not support or endorse these room searches or how they are executed. I sympathize with the challenge these hotels are facing but believe they need to take a harder look at the efficiency, impact and long term (sic) cost of this strategy.
“We MUST NOT let our hotels become like our airports. If we do, then the terrorists win.”
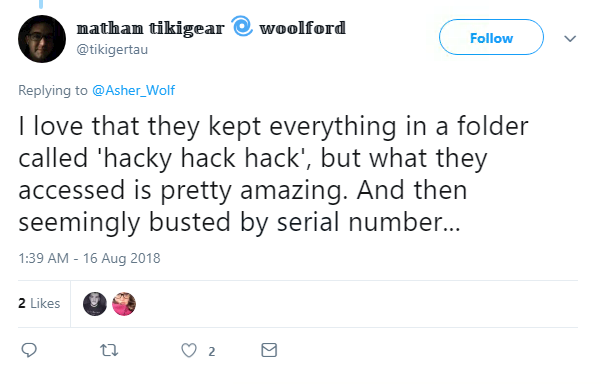
An Australian 16-year-old who hacked into Apple’s network and downloaded internal files stored the documents in a folder called ‘hacky hack hack’.
The boy – whose name cannot be reported – broke into the tech giant’s network multiple times over the course of a year, The Age newspaper reported.
He was also accused of boasting of the activities on WhatsApp.
Now you’d assume the teenager wouldn’t want to get caught committing the illegal act, which is why the naming of the folder has left some Twitter users dumbfounded.
He will be sentenced at a later date.
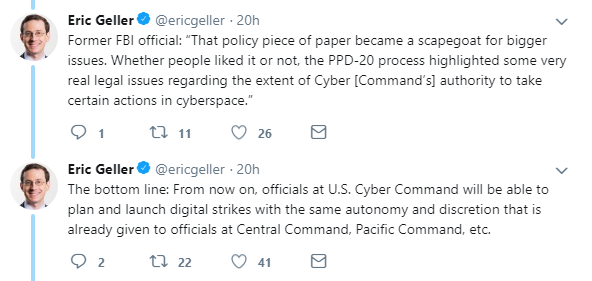
Finally, President Donald Trump this week signed an order relaxing the rules around the US launching cyber-attacks – with one official claiming it was “an offensive step forward”.
Guidelines were brought in by President Obama which ruled that multiple federal agencies needed to be involved with any cyberwarfare.
President Trump has relaxed the restrictions according to the White House, however the exact details of the amended guidelines are classified.
The former rules were revealed in the 2013 Edward Snowden leak.