Top infosec trends in the social media spotlight this week

This week, the security community descended on Las Vegas to celebrate the biggest event(s) in the infosec calendar.
Dubbed ‘Summer Camp’, security bods flocked to the city for Def Con, Black Hat, and BSides LV to listen to inspiring talks, learn new skills, and meet up with friends from across the globe.
And Wednesday also saw the return of the Pwnie awards, held to commend the best – and worst – exploits disclosed in 2018 so far.
This year’s awards, part of the Black Hat conference, saw some big-name vulnerabilities scoop prizes, such as Meltdown/Spectre, which was named best privilege escalation bug.
Organizers also rewarded the worst of 2018, with prizes for most over-hyped bug (’Holey Beep’) and lamest vendor response, which went to last-minute entry, BitFi.
The John McAfee-backed cryptocurrency wallet vendor was slammed last week after claiming that BitFi is “unhackable”, just days before they were proved wrong when a security researched allegedly cracked one of their wallets.
Their response? Well, McAfee is still running with the ’unhackable’ line, and the BitFi creators are claiming that an “army of trolls” hired by rival companies is behind the criticism on Twitter.
As you can probably guess, no one from BitFi was present to accept their award…
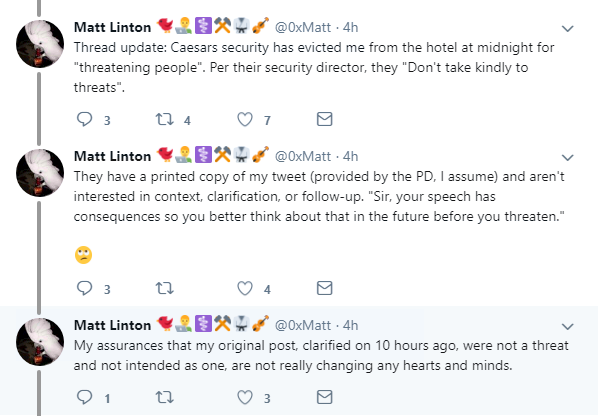
At Def Con, one Google security worker saw himself thrown out after a fallout with hotel staff.
Matt Linton, ‘chaos specialist’ at Google, was booted out of his hotel room at Caesars Palace in the early hours of Friday morning after a mis-judged tweet backfired.
Linton was in Vegas for both BH and Def Con to discuss the Meltdown/Spectre vulnerability.
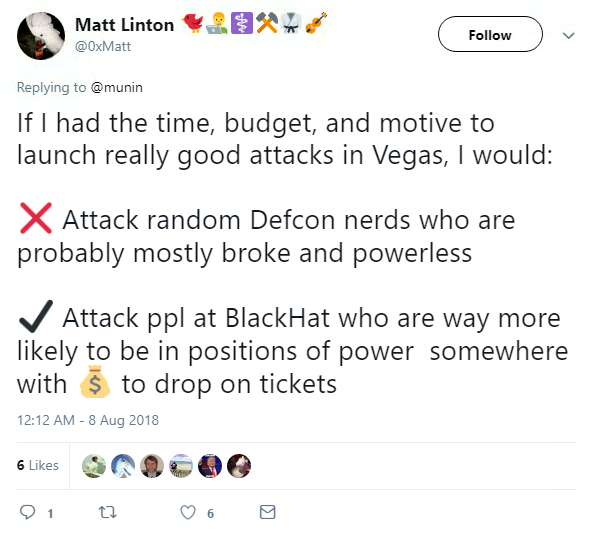
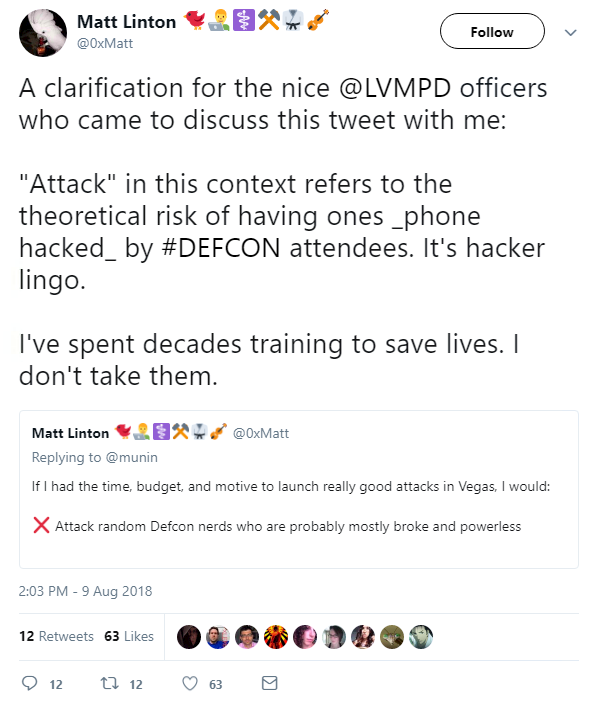
But after joking online about “attacking” Black Hat attendees, he found himself thrown out of Caesars and facing the Las Vegas Police Department.
The offending tweet read:
Which led to this:
Linton managed to smooth things over with the LVPD, who he said understood the word “attack” was taken out of context after a chat.
He explained:
Linton wrote on Twitter: “I’m not at all upset that someone misunderstood my tweet - looking at it out of context it IS worrisome to a layperson. What’s really disappointing is that my clarification is rejected out of hand.”
When attending any one of the events in Las Vegas, there’s a certain level of assumption that you’re going to be targeted by either a malicious or mischievous hacker.
Or you might be the subject of researchers such as coder Robert Graham, who took an in-depth look at Caesars Palace WiFi network this week.
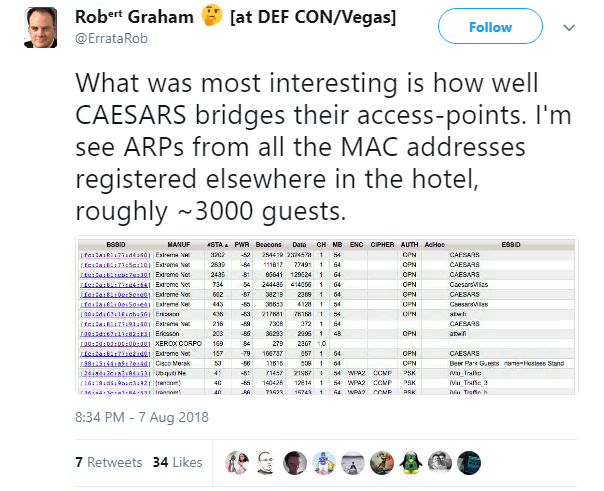
Graham took a deep-dive into the hotel WiFi to see what he could find – and found a list of every single connected device.
In a write-up, Graham noted: “This post doesn't contain any big hack. It’s fascinating how big WiFi has become, as everyone seems to be walking around with a WiFi device, and most are connecting to the hotel WiFi.
“The biggest takeaway is that even from a single point on the big network on the Caesars compound, I can get a record of some identifier that can in ideal circumstances be traced back to you.
“In theory, I could sit an airport, or drive around your neighborhood, and match up those records with these records. However, because of address randomization in probes, I can only do this is you’ve actually connected to the networks.”
Finally, would you be able to tell if one of your colleagues was a secret black hat?
According to new stats from Osterman Research, one in 13 cybersecurity professionals in the UK have admitted to being a ‘grey hat’ – working as both a cybercriminal and a security professional.
The study, which was commissioned by Malwarebytes, found that almost half of security workers in the UK (46.3%) said it was easy to dip into black hat activities without getting caught.
Motivations included earning more money, overcoming new challenges, seeking revenge on an employer, and moral causes.
The study also polled workers from the US, Germany, Singapore, and Australia.