Second batch in recent months likely came via online theft, reports Group-IB
UPDATED A database featuring more than 460,000 payment card records – almost all from India – is being offered for sale through a darknet bazaar, threat intel firm Group-IB warns.
The source of the payment card batch, which went on sale on the Joker’s Stash on Wednesday (February 5), remains unconfirmed, although circumstantial evidence suggests it came from online theft.
The vast majority (98% of the records) came from Indian banks, Group-IB said in its threat report.
Upon the discovery of the database, Group-IB has immediately informed the Indian Computer Emergency Response Team (CERT-In) about the sale of the payment records, so they could act to limit the harm resulting from the illicit sale.
The Daily Swig asked CERT-In to comment on what action is has taken, which might include notifying affected banks, to mitigate potential fraud arising from the illegal underground sale.
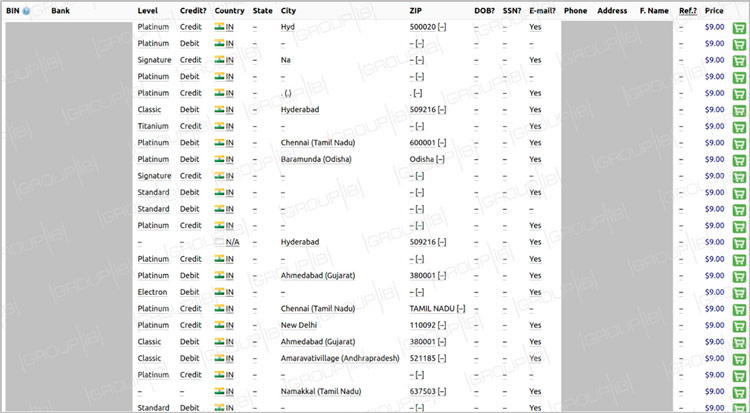
The vast majority of the stolen credit card records came from Indian banks
According to Group-IB’s threat intelligence team, the database is made up of 461,976 payment records, featuring card numbers, expiration dates, security codes and, in this case, some additional information such as cardholders’ full name, as well as their emails, phone numbers and addresses.
All the cards from the database are being sold for $9 each, representing a collective black-market value of $4.16 million.
As of the morning on February 6, a relatively modest 16 cards were reported to have been sold. However, in an update to The Daily Swig on the morning of February 10, Group-IB researchers said this figure had grown to 487.
Second helping for would-be fraudsters
A huge database holding more than 1.3 million credit and debit card records of mostly Indian banks’ customers was uploaded to the illicit Joker’s Stash marketplace last October, as previously reported.
Last year’s sale was bigger by volume but offered only the information contained in magnetic stripes of compromised cards.
The dataset associated with the latest sale (which offers CVV/CVC codes absent from the October batch) suggests that cards were compromised online, according to Group-IB.
“This is the second major leak of cards relating to Indian banks detected by Group-IB Threat Intelligence team in the past several months,” comments Dmitry Shestakov, head of Group-IB’s cybercrime research unit.
“In the current case, we are dealing with so-called ‘fullz’ – they have info on card number, expiration date, CVV/CVC, [and] cardholder name, as well as some extra personal info.”
RELATED Massive stolen credit card sale features 1.3m mostly Indian records
Shestakov added: “Such type of data is likely to have been compromised online – with the use of phishing, malware, or JS-sniffers – while in the previous case, we dealt with card dumps (the information contained in the card magnetic stripe), which can be stolen through the compromise of offline POS terminals, for example”.
According to Group-IB’s latest ‘Hi-Tech Crime Trends 2019/2020’ report, the size of the carding market rose by 33% year-on-year to reach $878 million by the end of June 2019.
The increase is partly been driven by the increasing popularity of JavaScript-sniffers (AKA Magecart), which enable their operators to steal payment card data from e-commerce websites.
The Southeast Asia region recently witnessed the first arrest of JS-sniffers’ operators anywhere in the world.
Three suspected cybercriminals from Indonesia recently confessed to stealing payment card data with the help of GetBilling JS-sniffer family.
The arrests came as a result of a joint operation of Interpol, Group-IB and Indonesian police.
This article has been updated to add new stolen card sales data from Group-IB.
READ MORE India’s answer to GDPR: New legislation set to pass this year






