Top infosec trends in the social media spotlight this week

Although it launched with the admittedly brilliant tagline, ‘Make America Date Again’, a new dating app aimed at Trump supporters hit the headlines for all the wrong reasons this week, after it was immediately found to be leaking its entire database of users.
As reported by TechCrunch, Donald Daters acquired more than 1,600 users on its launch day. This was known because a security researcher found issues with the app that made it possible to download the entire user database. Doh.
Donald Daters’ CEO Emily Moreno subsequently issued a statement to users that the company had taken “swift and decisive action” to fix the security issue, which was identified in the app’s third-party chat feature.
Following a cursory audit of the singles app, Motherboard editor-in-chief Jason Koebler issued a not-too-positive privacy report of his own:
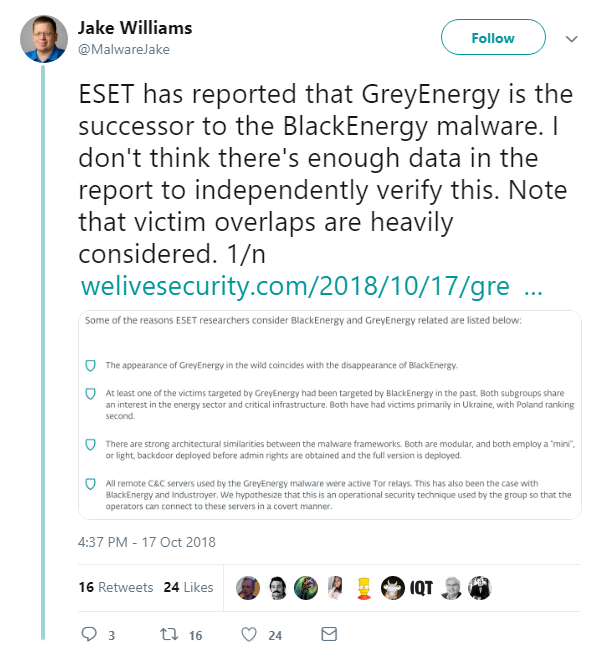
From leaky dating apps to state-sponsored hacks, researchers at ESET said they have uncovered details of the successor to BlackEnergy – the APT group whose main toolset was last seen during the attack against the Ukrainian power grid in December 2015.
According to ESET, analysis of a malware framework attributed to a new threat group, dubbed GreyEnergy, has since been used to attack energy companies and other high-value targets in Ukraine and Poland for the past three years.
“GreyEnergy’s malware framework bears many similarities to BlackEnergy,” said ESET. “It is similarly modular in construction, so its functionality is dependent on the particular combination of modules its operator uploads to each of the targeted victim systems.”
ESET’s findings were widely reported around the world. However, at least one security specialist urged caution when it comes to linking this new malware framework to the BlackEnergy group:
In government news, it was revealed that the UK’s Ministry of Defence (MoD) was subject to dozens of data security incidents last year.
Heavily redacted documents obtained by Sky News indicate that the MoD “failed to protect military and defense data in 37 incidents” in 2017.
Across the Atlantic, meanwhile, the Pentagon has admitted that the personal information and credit card data of up to 30,000 military workers had been exposed following a third-party security breach.
According to the Associated Press, the breach of a “single commercial vendor” resulted in Defense Department travel records being compromised.
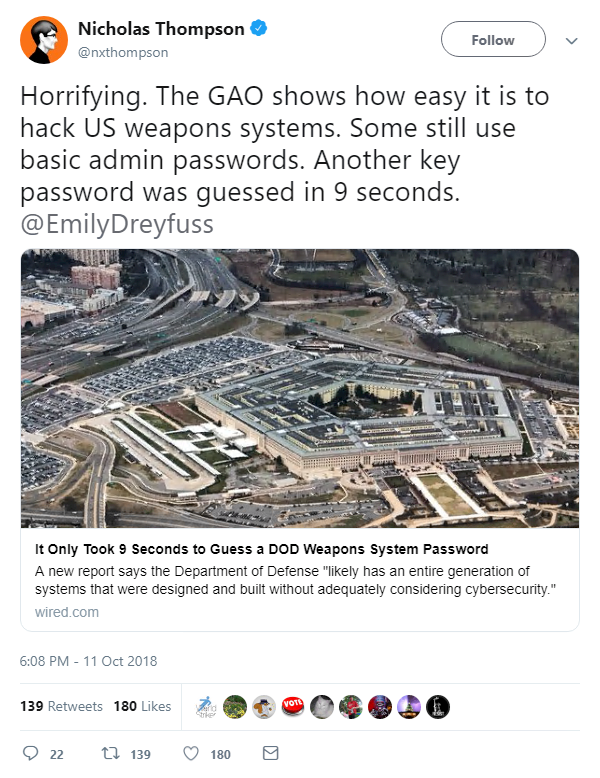
All this came as the US Government Accountability Office (GAO) issued a new report that suggests the Department of Defense is only just beginning to grapple with the scale of vulnerabilities impacting the security of its weapons systems.
While the report says the department has recently taken several steps to improve weapon systems cybersecurity, GAO said that almost all weapons tested between 2012 and 2017 have “mission critical” flaws.
“Using relatively simple tools and techniques, testers were able to take control of systems and largely operate undetected, due in part to basic issues such as poor password management and unencrypted communications,” the report reads.
And finally, following last week’s announcement that Google will close its floundering Google+ social media service, coupled with reports that YouTube was subject to a worldwide outage on October 16, one Reddit user has been harvesting karma by the bucketload after they published a tongue-in-cheek video that demonstrates what went wrong behind the scenes:
Check out the video here.