Attackers defaced homepage and accessed a database backup file containing passwords

NetGalley – a website that gives book reviewers pre-release access to new titles – has warned users about a data breach that may have exposed their passwords and other personal data.
“What initially seemed like a simple defacement of our homepage has, with further investigation, resulted in the unauthorized and unlawful access to a backup file of the NetGalley database,” said the company in a data breach alert published yesterday (December 23).
Users logging in from yesterday onwards must now reset their passwords in order to access their NetGalley account.
Publishing imprint
NetGalley said the compromised backup file contained users’ profile information, including login name and password, first and last name, email address, and country.
Applicable to users who supplied the relevant data, the file also contained mailing addresses, phone numbers, dates of birth, company names, and Kindle email addresses.
“We currently have no evidence of the exposure of any of this data, but we cannot at this stage rule out the possibility,” said the breach notification.
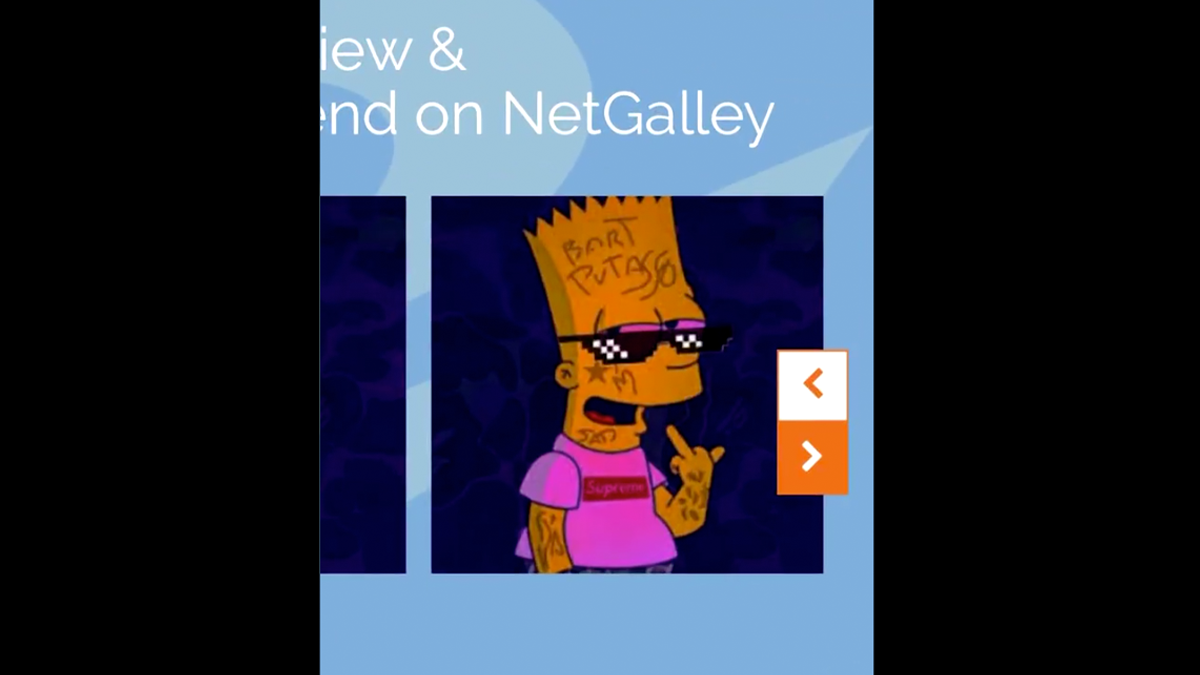 The NetGalley website was apparently defaced as part of the same incident
The NetGalley website was apparently defaced as part of the same incident
The Daily Swig has contacted NetGalley seeking clarification as to whether all (or some portion of) users’ profiles were exposed – we will update the article if and when we get a response.
The company said no financial information, such as bank account or credit card numbers, was exposed.
“Some profile photos” had been deleted from the system too, it added.
Catch up on the latest data breach news
NetGalley said the breach occured on Monday (December 21). “Once we found the cause of the breach, we were able to shut it down within an hour of identifying the breach,” it said.
The company said it had “re-secured” its testing sites, updated security protocols, “revised” their “database backup procedure”, and “changed all legacy password that had access to any NetGalley systems or data” in response to the attack.
A number of NetGalley users have taken to Twitter to criticize the company for what they assumed was the storage of passwords without encryption.
Stolen usernames and passwords are frequently used in automated ‘credential stuffing’ attacks against login pages of third-party web sites, a tactic that works because many users reuse the same password across multiple accounts.
RELATED Swedish university fined $66,000 for GDPR violations






