Defending against this brute-force hacking technique is more important now than ever before
Credential stuffing is a widely used hacking technique for exploiting data breach dumps in order to hijack victims’ online accounts.
The Daily Swig takes a deeper look at the dramatic rise to prominence of an account takeover technique that was unheard of until 2011.
What is credential stuffing?
Credential stuffing is a form of cyber-attack in which username/password pairs stolen from one website are automatically fed into the login pages of other web applications.
Leveraging the principle of trial and error, attackers use specialized software to ‘stuff’ an enormous volume of credential combinations into sign-in pages at high velocity in a bid to compromise accounts.
The technique – also called a ‘password reuse’ attack – only works because so many people use the same login details across multiple online accounts.
How does a credential stuffing attack work?
Credential stuffing attacks require an attacker to first source the necessary ‘ingredients’ – usually login credentials harvested from previous data breaches that are obtained through darknet marketplaces.
The attacker then uses account-checking software to inject hundreds, thousands, or even millions of credential pairs into various target websites at high speed.
Cybercrooks also deploy proxy services to obfuscate attacks and bypass IP blacklists.
Once an account is breached, attackers can then obtain additional sensitive information, hijack victims’ identities, and potentially bypass more rigorous authentication processes in place at, for instance, banks.
 Credential stuffing is used by attackers to fraudulently gain access to user accounts
Credential stuffing is used by attackers to fraudulently gain access to user accounts
How effective are credential stuffing attacks?
“Credential stuffing is one of the easiest and most effective attacks and has a high rate of return because every part of it can be automated,” Angel Grant, director of digital risk solutions at US digital risk firm RSA Security, tells The Daily Swig.
“Today, there are billions of stolen credentials available to purchase on the dark web, and this surplus means they’re being offered at low prices” – $1-2 per account, according to a 2019 report from Recorded Future – “so there’s really very [low] barriers to entry.”
US threat intel firm Recorded Future estimates the success rate of credential stuffing login attempts is around 1-3%. This may be a low figure, but when scaled up to, say, one million username/password pairs, cybercriminals have the potential to enjoy a massive return on investment.
Importantly, if malicious hackers are able to breach one account, they will no doubt attempt to compromise additional accounts belonging to the same user.
The evolution of credential stuffing infrastructure
The term ‘credential stuffing’ was coined in 2011 by Sumit Agarwal, then deputy assistant secretary of defense at the US Department of Defense, when he noticed a surge in brute-force attacks against military websites that appeared to use credentials spilled from other websites.
However, the phenomenon only became widespread around 2014 with the arrival of automated underground bazaars that did for the trade in data breach records what eBay achieved for the used goods market.
Read more of the latest security deep dives
A new breed of account checkers also emerged – such as STORM, WOXY, and Sentry MBA – that could support custom plugins, validate stolen credentials, and circumvent login protections – all typically for less than $50.
“Fraudsters can fully configure how the tool behaves,” says Angel Grant of the latest tools. “For example, they can change the number of logins attempts and change settings to make it appear to be a human not an automated tool.”
Tony Lauro, director of security technology and strategy at cybersecurity company Akamai, tells The Daily Swig that the most alarming recent innovation is how credential stuffing tools are “being integrated into the attacker workflow” with the effect of streamlining the trial-and-error process.
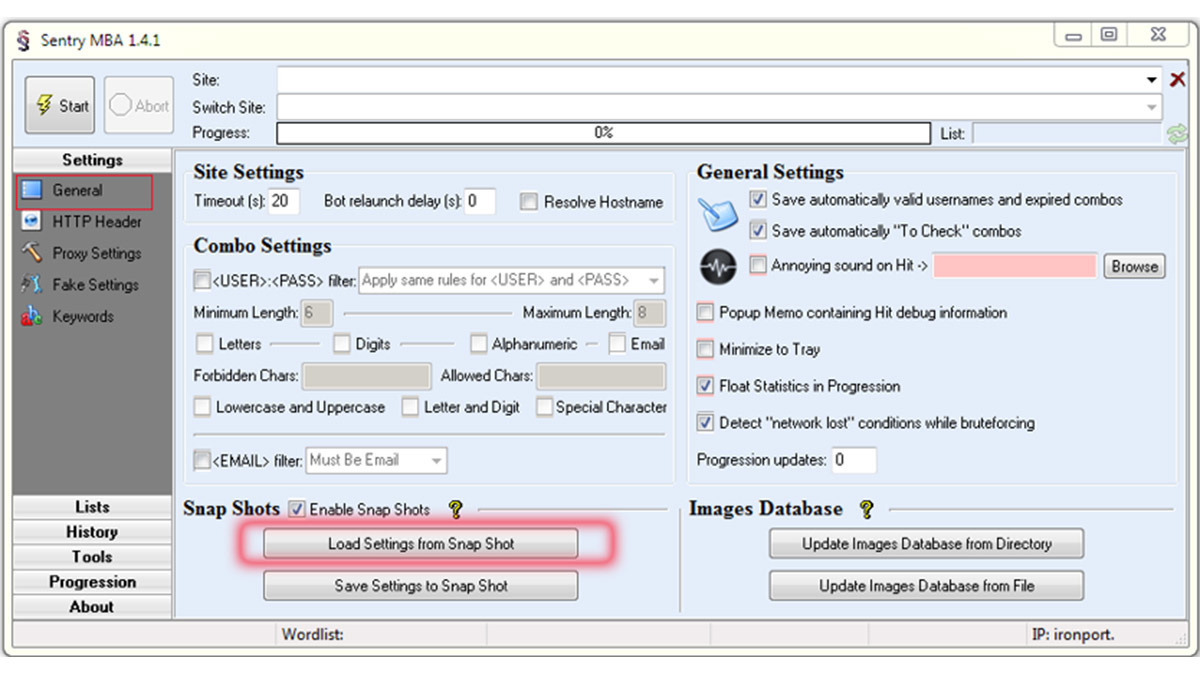 Sentry MBA is a well known credential stuffing tool
Sentry MBA is a well known credential stuffing tool
Credential stuffing, password spraying, and other brute-force techniques
Along with password spraying, credential stuffing is a form of brute-force attack, which is defined as any account takeover technique that involves the automated injection of password permutations.
Whereas credential stuffing harnesses troves of login details obtained from previous data breaches, password spraying targets a significant volume of known usernames with a small number of widely used passwords. This avoids triggering countermeasures that lock a user’s account after three or five failed login attempts.
However, unlike credential stuffing, password spraying’s effectiveness is blunted by the use of ‘strong’, difficult-to-guess passwords.
Other brute-forcing techniques include dictionary attacks, where attackers use a dictionary of possible passwords, and reverse brute-force attacks that test out potential usernames with a common password.
Examples of credential stuffing attacks
In September 2020, the FBI alerted the US financial services industry to the credential stuffing threat, noting that since 2017 the technique had led to “nearly 50,000 account compromises” in the sector.
Akamai recently reported that the gaming sector, too, was being pummeled – “in the pursuit of free service, access to payment card information, or to simply take advantage of the new ecosystem of micro-transactions”, according to Tony Lauro.
The gaming industry accounted for nearly 10 billion of the 100 billion-plus credential stuffing attacks recorded by Akamai between July 2018 to June 2020.
Streaming platforms such as Dailymotion are also an increasingly favored target.
In August, meanwhile, attacks against GCKey, the authentication service through which Canadians access various government services, resulted in the compromise of more than 9,000 GCKey accounts.
How can you detect and defend against a credential stuffing attack?
Users can essentially make themselves impervious to credential stuffing attacks by doing the following:
- Using a password manager to generate and save ‘strong’ and – crucially – unique passwords on all accounts
- Enabling multi-factor authentication (if this isn’t an option “it’s worth re-evaluating your relationship with that provider”, Andrew Shikiar, executive director at the FIDO Alliance, tells The Daily Swig)
- Subscribing to notification services that alert users when their credentials surface in fresh data breach dumps
However, the continuing effectiveness of credential stuffing attacks is evidence enough that all too few users are prepared to tolerate the inconvenience that password hygiene entails – even after learning that a new breach has put them at risk (PDF).
Andrew Shikiar of the FIDO Alliance, which champions alternative authentication standards to passwords, says: “Organizations have struggled to strike the right balance between frictionless yet secure online logins,” adding that passwords “have become incredibly cumbersome and difficult to properly manage”.
CAPTCHAs, the challenge-response technique that involves choosing, say, tiles containing images of cars within a traffic scene to prove you are human, are one widespread solution that is said to be flawed in both security and UX terms.
RELATED Machine learning techniques applied to crack CAPTCHAs
Tony Lauro says he has even seen ‘inventory sniping’ tools with “a CAPTCHA catcher mechanism” that can dupe Google’s low-friction reCAPTCHA technology.
He anticipates that bot defenses will become more adept at recognizing and arresting bot operators’ progress within compromised accounts with “crypto worker challenges” that don’t disrupt the legitimate user’s experience.
Angel Grant advocates “a risk-based approach to customer authentication” that RSA Security has fleshed out in a recent report analyzing ‘the credential stuffing Gold Rush’.
Epic Games, which responded to a recent spate of attacks against players of the popular Fortnite video game by encouraging users to activate multi-factor authentication in order to receive in-game perks, is an exemplar of how to “add friction” and “decrease the rate of success”, Grant says.
 Stolen account credentials are easily available on underground darknet marketplaces
Stolen account credentials are easily available on underground darknet marketplaces
“An easy first step” for a cross-site analysis of credential abuse campaigns, says Tony Lauro, is “scanning publicly available datasets for shared logins” that “have already been compromised and shared somewhere else”.
However, attackers are increasingly obfuscating their campaigns by “spreading requests among more IP addresses and making fewer requests per IP”, he notes.
In one campaign analyzed by Akamai, 92% of botnet members sent fewer than 20 login attempts within 24 hours, with 10% contributing a single login attempt.
Cross-analysis with other customers’ login attempts revealed that “the botnet was actually targeting 71 different websites”, added Lauro.
Lauro also recommends integrating consumer identity information into the detection process.
“Attackers often know much about the browser and the applications they’re attacking, because all that information is publicly gleaned using OSINT of their target system.”
But detection checks based on the fact that the user “always connects from an AT&T Business network from Dallas, Texas”, or “the device headers that he’s logging in from usually belong to an iOS mobile device” are “nearly impossible [for attackers to fool] at large scale”.
In the long term, Andrew Shikiar believes that universal adoption of “the latest on-device public key cryptography standards” will both neutralize the credential stuffing threat and “provide a friction-free user experience”.
Here, the user is validated “through a single gesture” such as touching a security key or looking at a screen, while a corresponding public key sits on a server “that, even if stolen, cannot be reused by hackers or other bad actors”.
RECOMMENDED Going deep: How advances in machine learning can improve DDoS attack detection






