Dangerous bug could allow attackers to manipulate the behavior of an application by modifying its runtime
A carryover function in the popular node-forge JavaScript library contains a vulnerability that could allow attackers to carry out prototype pollution attacks against applications, according to an advisory on GitHub.
Node-forge, used by more than 3.5 million repositories, implements various cryptography utilities, the TLS protocol, and tools for developing web applications.
Prototype pollution is a dangerous bug that allows attackers to manipulate the behavior of an application by modifying its code at runtime.
It is usually carried out through malicious input, and depending on the vulnerable components, can lead to a range of attacks, including denial of service or even remote code execution (RCE).
The culprit in node-forge was util.setPath(), a function that had existed since the early versions of the library before it became focused on cryptography.
BACKGROUND Prototype pollution: The dangerous vulnerability impacting JavaScript applications
“util.setPath had a potential prototype pollution security issue when used with unsafe inputs,” the changelog of node-forge writes. setPath is a general-purpose function that allows developers to change the properties of objects by passing text strings.
The bug was first reported to Snyk, which disclosed its findings after the maintainers of node-forge released a patch.
The vulnerability has been given a high-severity 9.8 score on Snyk and 7.3 by the National Vulnerability Database. A proof of concept posted on Snyk’s website shows that setPath can be used to pollute the __prototype__ property of the base Object, resulting in application-wide modifications.
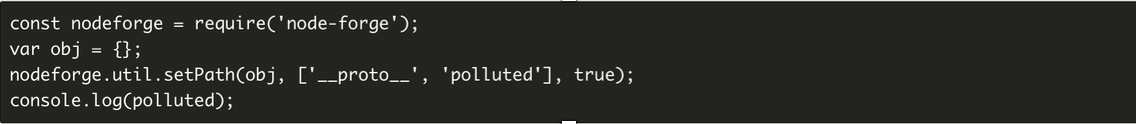 A potential prototype pollution security issue when util.setPath() is used with unsafe inputs
A potential prototype pollution security issue when util.setPath() is used with unsafe inputs
“These functions are not used by forge itself. They date from an early time when forge was targeted at providing general helper functions,” the node-forge changelog writes.
David Lehn, the maintainer of node-forge, told The Daily Swig: “We’ve never observed anyone using that function at all, including within forge itself, much less exploiting it.”
Along with other related functions, setPath was removed from the latest version of node-forge.
The maintainers of node-forge suggest using other libraries that have similar property-setting functionalities, such as lodash, but also warn about possible prototype pollution vulnerabilities in those libraries.
“lodash set() is similar to what setPath() did (and a fine supported replacement for setPath). I imagine other people have written similar object-path-setting code. It’s quite useful when used properly,” Lehn said, but added that any code that provides this functionality could have similar security issues if the input is not sanitized.
YOU MAY ALSO LIKE TrojanNet – a simple yet effective attack on machine learning models






